

SherlockElf is a powerful tool designed for both static and dynamic analysis of Android ELF binaries and dynamic analysis of iOS Macho-O binaries (experimental). It helps security researchers, developers, and reverse engineers gain insights into ELF (Executable and Linkable Format) binaries used in Android applications and Mach-O (Mach Object) binaries used in iOS applications.
Emulator:
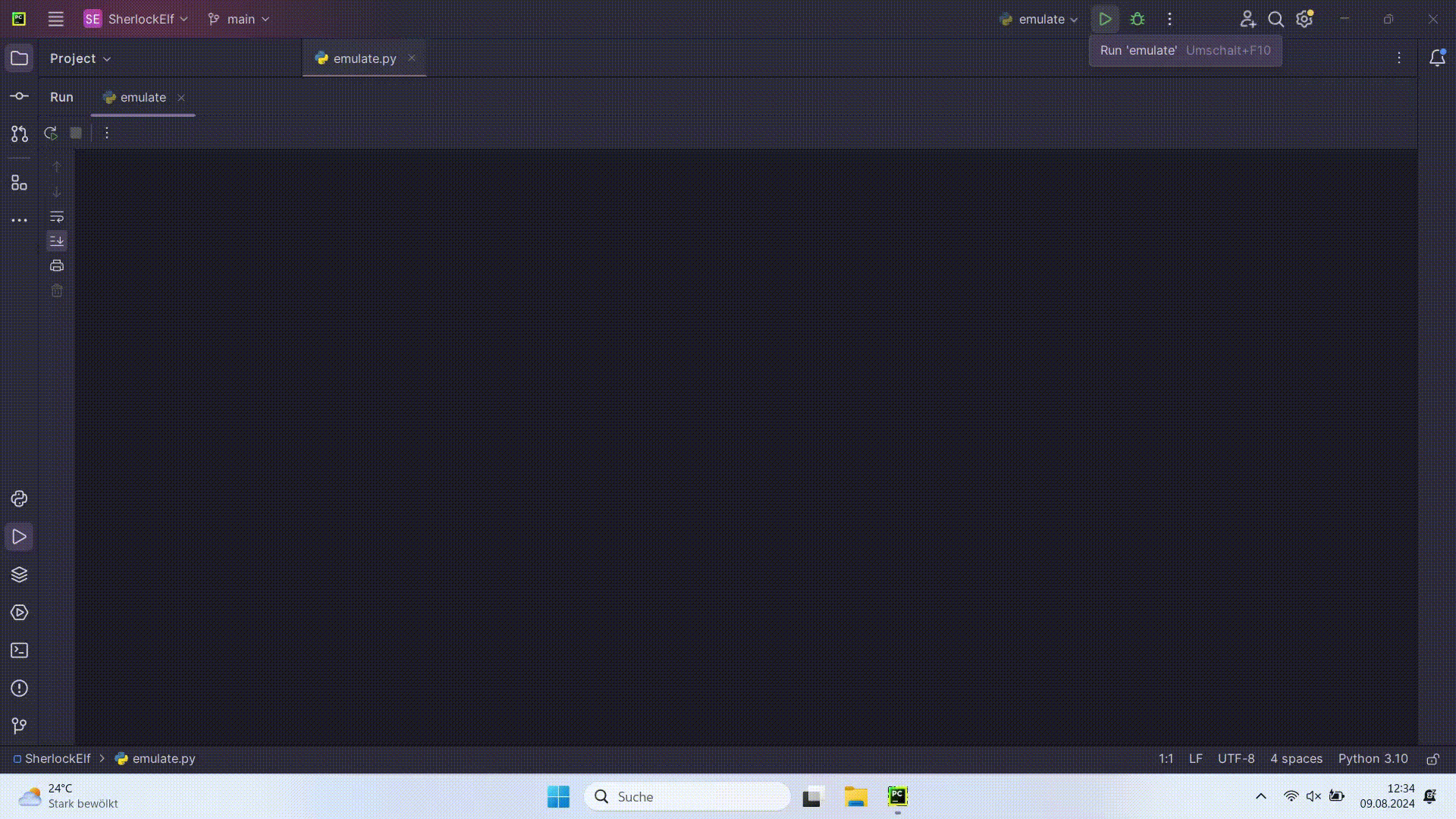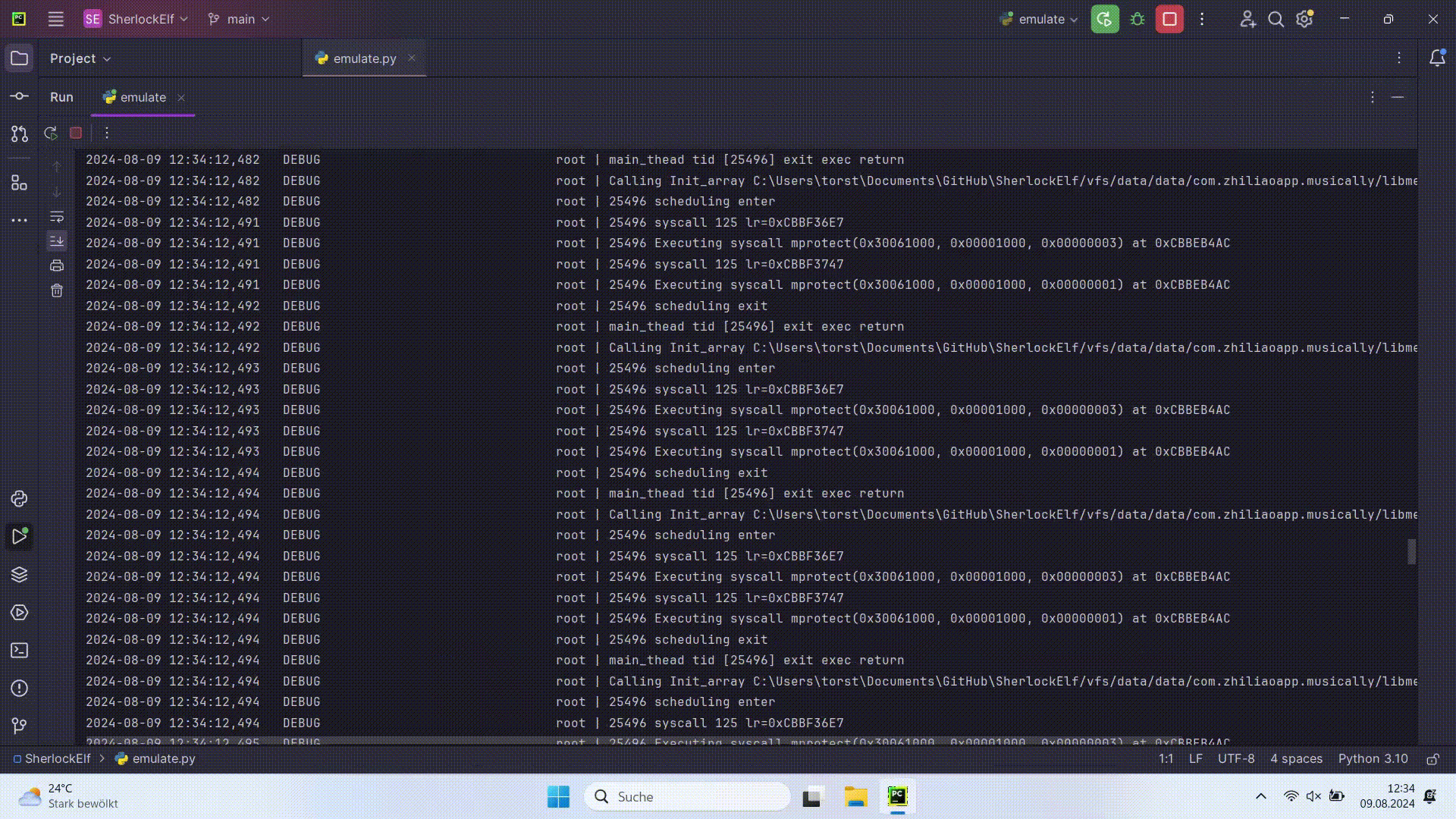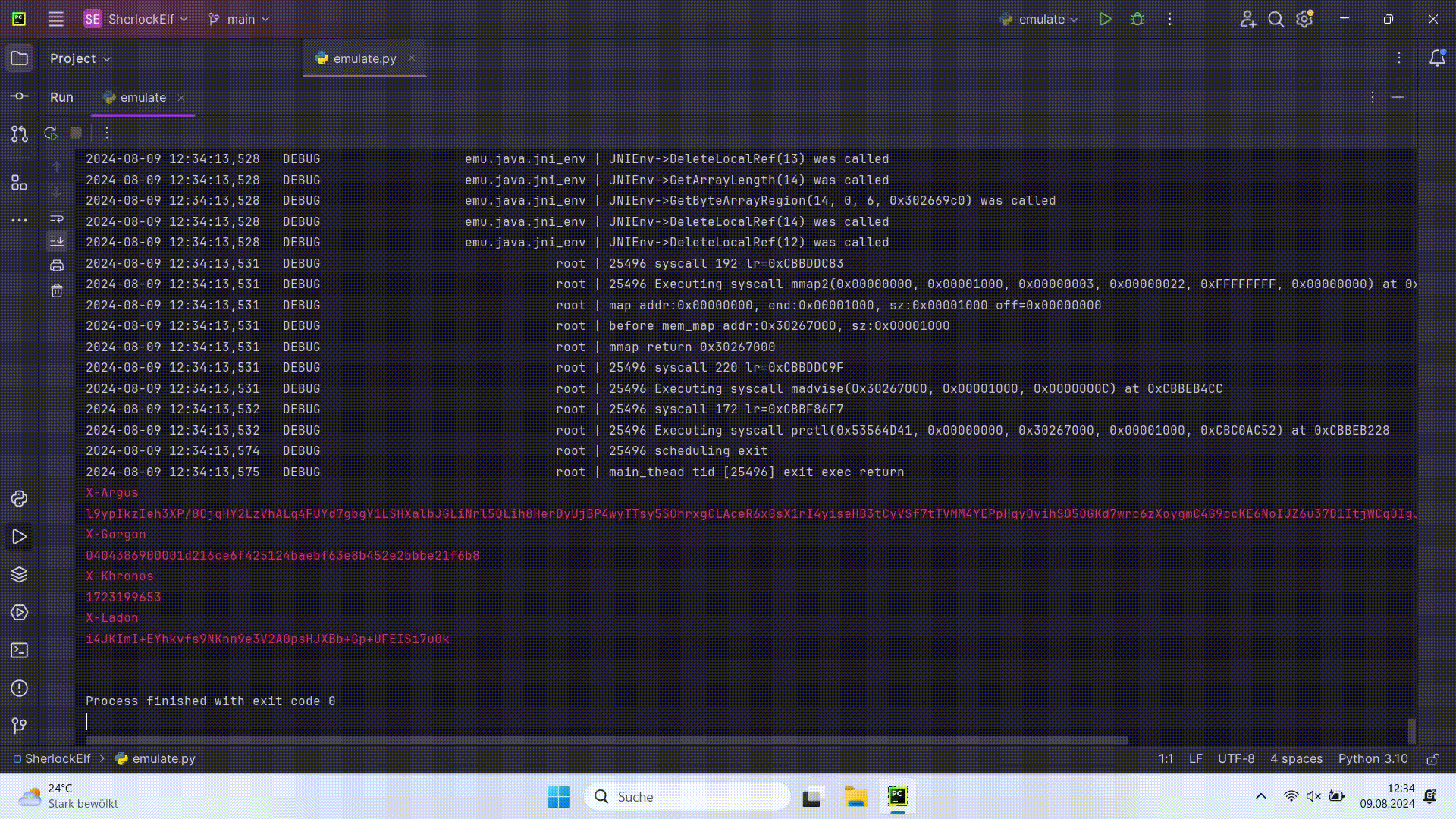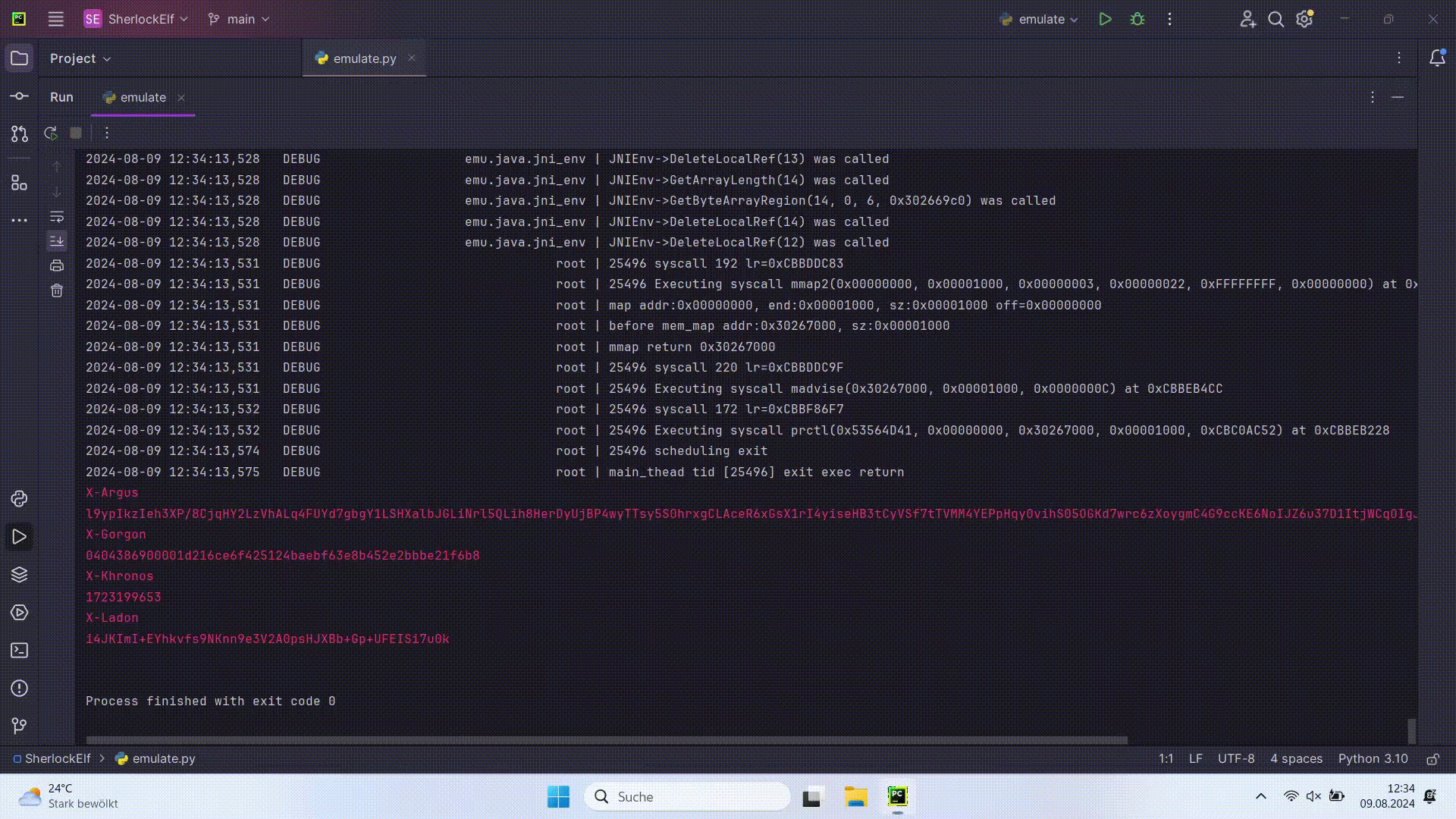
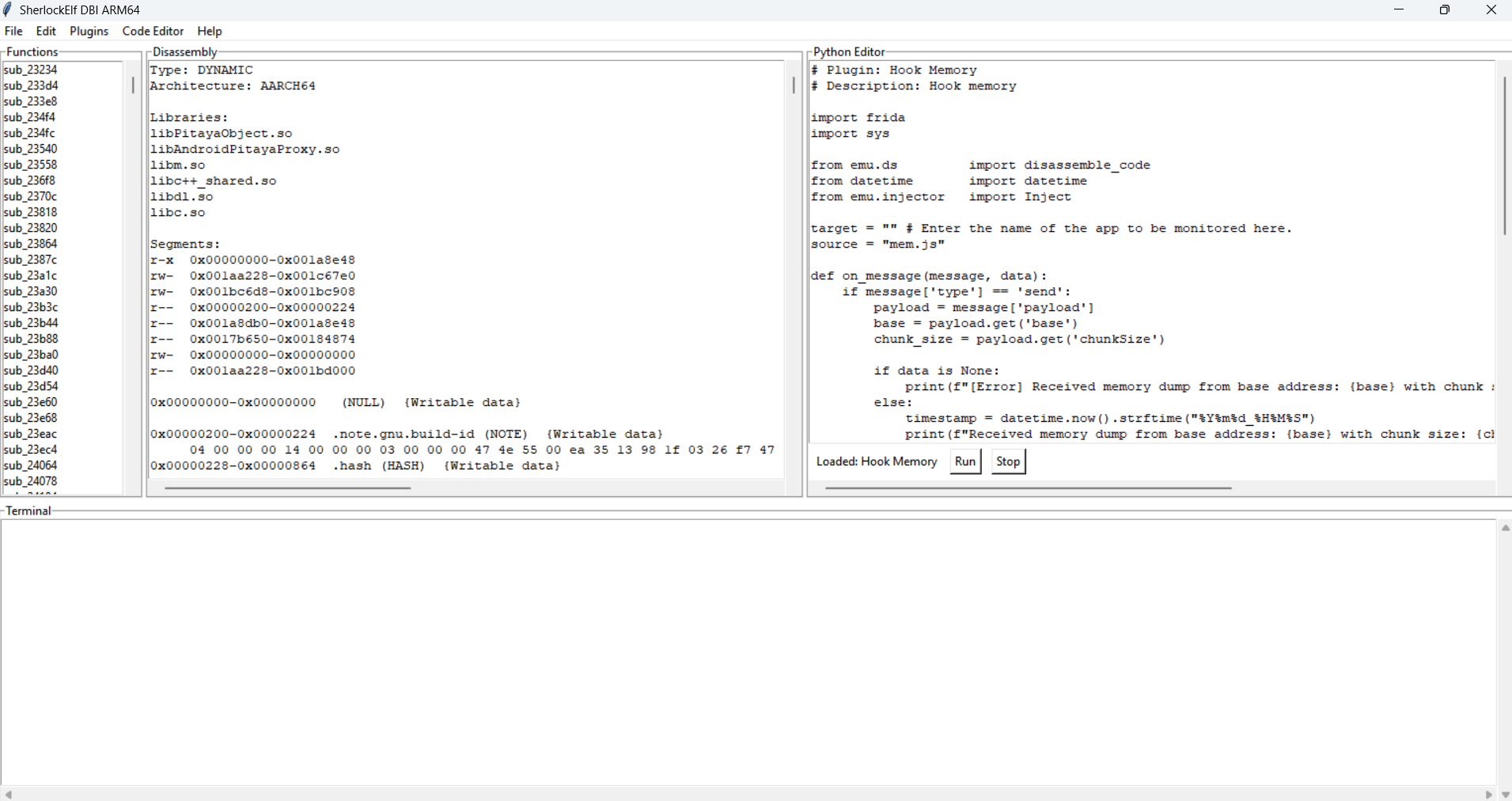
Dynamic Binary Instrumentor:
To get started with SherlockElf, follow these steps:
Clone the Repository:
git clone https://github.com/iamtorsten/SherlockElf.git
cd SherlockElfInstall Dependencies:
pip install -r requirements.txtSetup Environment:
Using SherlockElf is straightforward. Below are some common commands and their descriptions:
python emulator.pywith open("hook/mem.js") as f:
script_code = f.read()
sherlock = Inject(target=target)
device, session = sherlock.attach()
script = sherlock.source(session, script_code)
script.on('message', on_message)
script.load()We welcome contributions from the community! If you'd like to contribute to SherlockElf, please follow these steps:
git clone https://github.com/iamtorsten/SherlockElf.gitgit checkout -b feature-branchgit commit -am 'Add new feature'git push origin feature-branchSherlockElf is licensed under the MIT License. See the LICENSE file for more information.
For any questions or feedback, please reach out via email at [email protected].
This Project is just for personal educational purposed only. You can modify it for your personal used. But i do not take any resonsibility for issues caused by any modification of this project. All processes illustrated in the project serve only as examples.
Use of this code must comply with applicable laws.