hacksys極限脆弱的驅動程序
ooooo ooooo oooooooooooo oooooo oooo oooooooooo.
`888' `888' `888' `8 `888. .8' `888' `Y8b
888 888 888 `888. .8' 888 888
888ooooo888 888oooo8 `888. .8' 888 888
888 888 888 " `888.8' 888 888
888 888 888 o `888' 888 d88'
o888o o888o o888ooooood8 `8' o888bood8P'
Hacksys Extreme脆弱驅動程序(HEVD)是有意脆弱的Windows內核驅動程序。它是為安全研究人員和愛好者開發的,以提高其內核級剝削的技能。
HEVD提供了一系列漏洞,從簡單的堆棧緩衝區溢出到更複雜的問題,例如無用後,泳池緩衝區溢出和競賽條件。這使研究人員可以探索每個實施漏洞的剝削技術。
黑帽阿森納2016年
博客文章
- http://www.payatu.com/hacksys-extreme-vulnerable-driver/
外部利用
- https://github.com/sam-b/hacksysdriverexploits
- https://github.com/sizzop/hevd-exploits
- https://github.com/badd1e/bug-free-adventure
- https://github.com/fuzzysecurity/hacksysteam-pskernelpwn
- https://github.com/theevilbit/exploits/tree/master/hevd
- https://github.com/gradiusx/hevd-python-solutions
- http://pastebin.com/alkdpdsf
- https://github.com/cn33liz/hsevd stackoverflow
- https://github.com/cn33liz/hsevd-stackoverflowx64
- https://github.com/cn33liz/hsevd stackcookiebypass
- https://github.com/cn33liz/hsevd-arbitraryoverwrite
- https://github.com/cn33liz/hsevd-arbitraryoverwritegdi
- https://github.com/cn33liz/hsevd stackoverflowgdi
- https://github.com/cn33liz/hsevd-arbitraryoverwritelowil
- https://github.com/mgeeky/hevd_kernel_exploit
- https://github.com/tekwizz123/hevd-exploit-solutions
- https://github.com/fullshade/windows-kernel-ecploitation-hevd
- https://github.com/w4fz5uck5/3xpl01t5/tree/master/master/ose_training
外部博客文章
- http://niiconsulting.com/checkmate/2016/01/windows-kernel-exploitation/
- http://samdb.xyz/2016/01/16/intro_to_kernel_exploitation_part_0.html
- http://samdb.xyz/2016/01/17/intro_to_kernel_exploitation_part_1.html
- http://samdb.xyz/2016/01/18/intro_to_kernel_exploitation_part_2.html
- http://samdb.xyz/2017/06/22/intro_to_kernel_exploitation_part_3.html
- https://sizzop.github.io/2016/07/05/kernel-hacking-with-hevd-part-part-part-1.html
- https://sizzop.github.io/2016/07/06/kernel-hacking-with-hevd-part-part-part-2.html
- https://sizzop.github.io/2016/07/07/kernel-hacking-with-hevd-part-part-3.html
- https://sizzop.github.io/2016/07/08/kernel-hacking-with-hevd-part-part-4.html
- https://www.fuzzysecurity.com/tutorials/expdev/14.html
- https://www.fuzzysecurity.com/tutorials/expdev/15.html
- https://www.fuzzysecurity.com/tutorials/expdev/16.html
- https://www.fuzzysecurity.com/tutorials/expdev/17.html
- https://www.fuzzysecurity.com/tutorials/expdev/18.html
- https://www.fuzzysecurity.com/tutorials/expdev/19.html
- https://www.fuzzysecurity.com/tutorials/expdev/20.html
- http://dokydoky.tistory.com/445
- https://hshrzd.wordpress.com/2017/05/28/starting-with-windows-kernel-exploitation-proitation-part-part-1-setting-the-lab/
- https://hshrzd.wordpress.com/2017/06/05/starting-with-windows-kernel-exploitation-part-part-2/
- https://hshrzd.wordpress.com/2017/06/22/starting-with-with-windows-kernel-exploitation-part-part-3-stealing-the-tealing-the-access-token/
- https://osandamalith.com/2017/04/05/windows-kernel-exploitation-stack-overflow/
- https://osandamalith.com/2017/06/14/windows-kernel-exploitation-arbitrary-overwrite/
- https://osandamalith.com/2017/06/22/windows-kernel-exploitation-null-pointer-dereference/
- http://dali-mrabet1.rhcloud.com/windows-kernel-exploitation-arbitrary-memory-memory-overwrite-hevd-challenges/
- https://blahcat.github.io/2017/08/31/arbitrary-write-primitive-in-windows-kernel-hevd/
- https://klue.github.io/blog/2017/09/hevd_stack_gs/
- https://glennmcgui.re/indroduction-to-windows-kernel-exploitation-pt-1/
- https://glennmcgui.re/indroduction-to-windows-kernel-driver-exploitation-pt-2/
- https://kristal-g.github.io/2021/02/07/hevd_stackoverflows_windows_windows_10_rs5_x64.html
- https://kristal-g.github.io/2021/02/20/hevd_type_confusion_windows_windows_10_rs5_x64.html
- https://wafzsucks.medium.com/hacksys-extreme-vulnerable-driver-driver-arbitrary-write-null-null-new-new-solution-7d45bfe6d116
- https://wafzsucks.medium.com/how-a-simple-k-ty-peconfusion-took-me-3-months-long-to to-to-to-a-a-a-exploit-f643c94d4445f
- https://mdanilor.github.io/posts/hevd-0/
- https://mdanilor.github.io/posts/hevd-1/
- https://mdanilor.github.io/posts/hevd-2/
- https://mdanilor.github.io/posts/hevd-3/
- https://mdanilor.github.io/posts/hevd-4/
作者
Ashfaq Ansari
ashfaq [at] hacksys [dot] io
博客| @hacksysteam
https://hacksys.io/
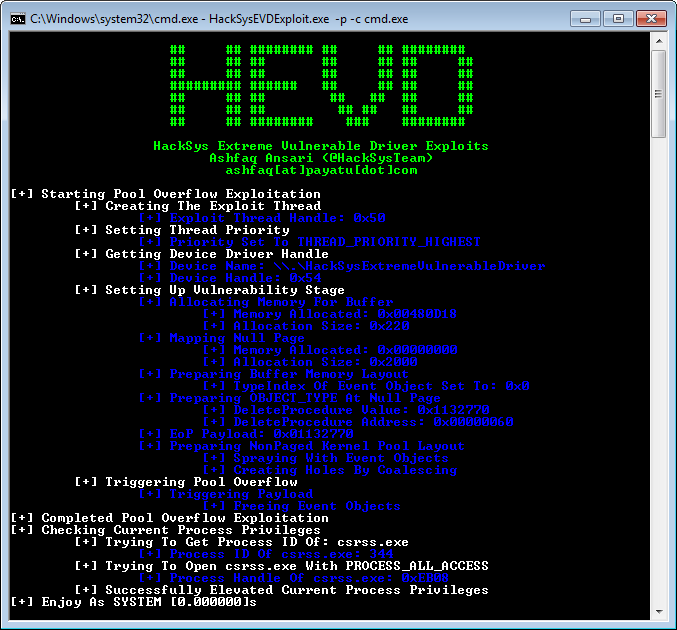
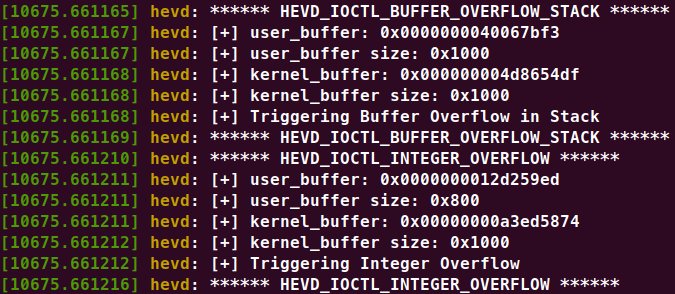
屏幕截圖
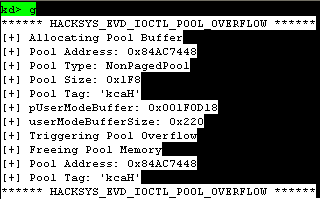
實施漏洞
- 寫null
- 雙提取
- 緩衝區溢出
- 堆
- 堆棧GS
- 非頁碼
- 非pagedpoolnx
- page夫
- 免費使用後使用
- 類型混亂
- 整數溢出
- 內存披露
- 任意增量
- 任意覆蓋
- 空指針取消
- 非初始化的內存
- 不安全的內核資源訪問
建造駕駛員
- 安裝Visual Studio 2017
- 安裝Windows驅動程序套件
- 運行適當的驅動程序builder
Build_HEVD_Vulnerable_x86.bat或Build_HEVD_Vulnerable_x64.bat
下載
如果您不想從源構建Hacksys Extreme脆弱驅動程序,則可以下載預製的可執行文件以獲取最新版本:
https://github.com/hacksysteam/hacksysextremevulnerabledriver/releases
安裝驅動程序
使用OSR驅動程序加載程序安裝Hacksys Extreme脆弱驅動程序
測試
Hacksys極限易受攻擊的驅動程序和各自的漏洞已在Windows 7 SP1 X86和Windows 10 x64上進行了測試
進行了會議
- Windows內核開發1
- Windows內核剝削2
- Windows內核開發3
- Windows內核剝削4
- Windows內核剝削5
- Windows內核開發6
- Windows內核開發7
講習班進行
- Windows內核剝削Humla Pune
- Windows內核剝削Humla Mumbai
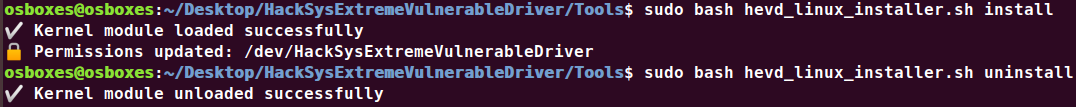
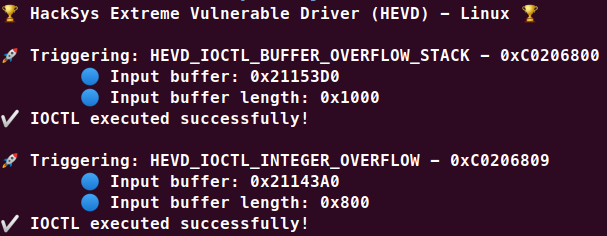
HEVD為Linux
執照
請參閱文件LICENSE以復制許可
貢獻指南
請參閱文件CONTRIBUTING.md文件以獲取貢獻指南
待辦事項報告
請通過GITHUB DOUSSE TRACKER在以下地址上提交任何增強請求或錯誤報告:https://github.com/hacksysteam/hacksysextremevulnerabledriver/issues
致謝
謝謝這些好人:?