Hacksys Driver Rentan Ekstrim
ooooo ooooo oooooooooooo oooooo oooo oooooooooo.
`888' `888' `888' `8 `888. .8' `888' `Y8b
888 888 888 `888. .8' 888 888
888ooooo888 888oooo8 `888. .8' 888 888
888 888 888 " `888.8' 888 888
888 888 888 o `888' 888 d88'
o888o o888o o888ooooood8 `8' o888bood8P'
Hacksys Extreme Rentan Driver (HEVD) adalah driver kernel Windows yang sengaja rentan. Ini telah dikembangkan untuk para peneliti dan penggemar keamanan untuk meningkatkan keterampilan mereka dalam eksploitasi tingkat kernel .
HEVD menawarkan berbagai kerentanan, mulai dari buffer tumpukan sederhana hingga masalah yang lebih kompleks seperti penggunaan-bebas , luapan buffer biliar , dan kondisi balapan . Hal ini memungkinkan para peneliti untuk mengeksplorasi teknik eksploitasi untuk setiap kerentanan yang diimplementasikan.
Black Hat Arsenal 2016
Posting Blog
- http://www.payatu.com/hacksys-extreme-vulnerable-driver/
Eksploitasi eksternal
- https://github.com/sam-b/hacksysdriverexploits
- https://github.com/sizzop/hevd-exploits
- https://github.com/badd1e/bug-free-adventure
- https://github.com/fuzzysecurity/hacksysteam-pskernelpwn
- https://github.com/theevilbit/exploits/tree/master/hevd
- https://github.com/gradiusx/hevd-python-solutions
- http://pastebin.com/alkdpdsf
- https://github.com/cn33liz/hsevd-stackoverflow
- https://github.com/cn33liz/hsevd-stackoverflowx64
- https://github.com/cn33liz/hsevd-stackcookiebypass
- https://github.com/cn33liz/hsevd-arbitraryoverwrite
- https://github.com/cn33liz/hsevd-arbitraryoverwritegdi
- https://github.com/cn33liz/hsevd-stackoverflowgdi
- https://github.com/cn33liz/hsevd-arbitraryoverwritelowil
- https://github.com/mgeeky/hevd_kernel_exploit
- https://github.com/tekwizz123/hevd-exploit-solutions
- https://github.com/fullshade/windows-kernel-exploitation-hevd
- https://github.com/w4fz5uck5/3xpl01t5/tree/master/osee_training
Posting blog eksternal
- http://niiconsulting.com/checkmate/2016/01/windows-kernel-exploitation/
- http://samdb.xyz/2016/01/16/intro_to_kernel_exploitation_part_0.html
- http://samdb.xyz/2016/01/17/intro_to_kernel_exploitation_part_1.html
- http://samdb.xyz/2016/01/18/intro_to_kernel_exploitation_part_2.html
- http://samdb.xyz/2017/06/22/intro_to_kernel_exploitation_part_3.html
- https://sizzop.github.io/2016/07/05/kernel-hacking-with-hevd-part-1.html
- https://sizzop.github.io/2016/07/06/kernel-hacking-with-hevd-part-2.html
- https://sizzop.github.io/2016/07/07/kernel-hacking-with-hevd-part-3.html
- https://sizzop.github.io/2016/07/08/kernel-hacking-with-hevd-part-4.html
- https://www.fuzzysecurity.com/tutorials/expdev/14.html
- https://www.fuzzysecurity.com/tutorials/expdev/15.html
- https://www.fuzzysecurity.com/tutorials/expdev/16.html
- https://www.fuzzysecurity.com/tutorials/expdev/17.html
- https://www.fuzzysecurity.com/tutorials/expdev/18.html
- https://www.fuzzysecurity.com/tutorials/expdev/19.html
- https://www.fuzzysecurity.com/tutorials/expdev/20.html
- http://dokydoky.tistory.com/445
- https://hshrzd.wordpress.com/2017/05/28/startting-with-windows-kernel-exploitation-part-1-setting-up-the-lab/
- https://hshrzd.wordpress.com/2017/06/05/startting-with-windows-kernel-exploitation-part-2/
- https://hshrzd.wordpress.com/2017/06/22/startting-with-windows-kernel-exploitation-part-3-stealing-the-access-token/
- https://osandamalith.com/2017/04/05/windows-kernel-exploitation-stack-overflow/
- https://osandamalith.com/2017/06/14/windows-kernel-exploitation-arbitrary-overwrite/
- https://osandamalith.com/2017/06/22/windows-kernel-exploitation-null-pointer-dereference/
- http://dali-mrabet1.rhcloud.com/windows-kernel-exploitation-arbitrary-memory-overwrite-hevd-challenges/
- https://blahcat.github.io/2017/08/31/arbitrary-write-prite-in-windows-kernel-hevd/
- https://klue.github.io/blog/2017/09/hevd_stack_gs/
- https://glennmcgui.re/introduction-to-windows-kernel-exploitation-pt-1/
- https://glennmcgui.re/introduction-to-windows-kernel-driver-exploitation-pt-2/
- https://kristal-g.github.io/2021/02/07/hevd_stackoverflowgs_windows_10_rs5_x64.html
- https://kristal-g.github.io/2021/02/20/hevd_type_confusion_windows_10_rs5_x64.html
- https://wafzsucks.medium.com/hacksys-extreme-vulnerable-driver-arbitrary-write-null-new-solution-7d45bfe6d116
- https://wafzsucks.medium.com/how-a-simple-k-typeconfusion-took-me-3-months-long-to-create-a-exploit-f643c94d445f
- https://mdanilor.github.io/posts/hevd-0/
- https://mdanilor.github.io/posts/hevd-1/
- https://mdanilor.github.io/posts/hevd-2/
- https://mdanilor.github.io/posts/hevd-3/
- https://mdanilor.github.io/posts/hevd-4/
Pengarang
Ashfaq Ansari
ashfaq [at] hacksys [dot] io
Blog | @Hacksysteam
https://hacksys.io/
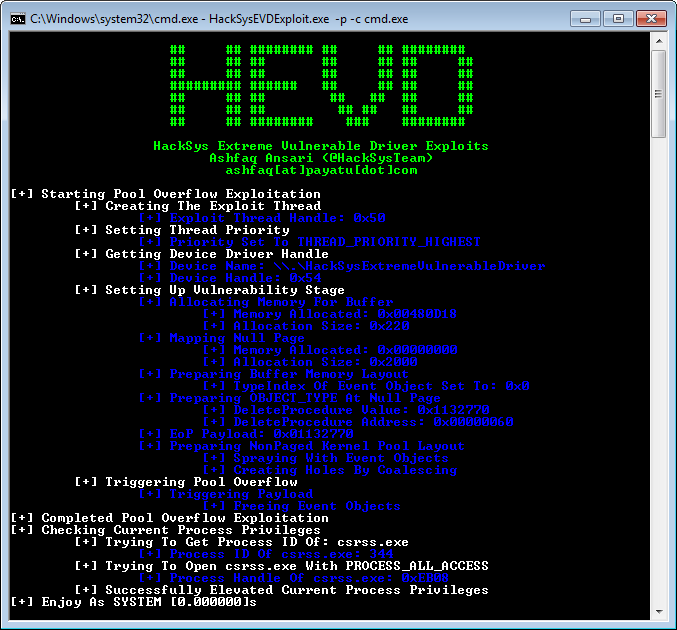
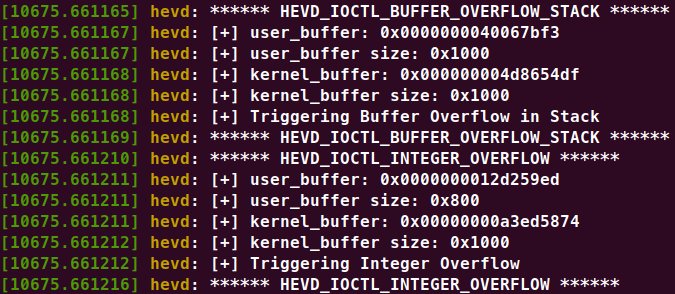
Tangkapan layar
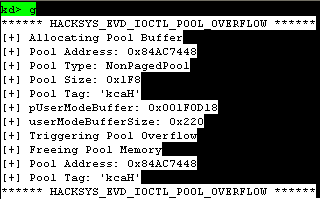
Kerentanan diterapkan
- Tulis NULL
- Ambil ganda
- Buffer overflow
- Tumpukan
- Tumpukan GS
- Nonpage -cool
- Nonpagedpoolnx
- Pagedpoolsession
- Gunakan setelah gratis
- Nonpage -cool
- Nonpagedpoolnx
- Ketik kebingungan
- Integer overflow
- Pengungkapan memori
- Nonpage -cool
- Nonpagedpoolnx
- Kenaikan sewenang -wenang
- Timpa sewenang -wenang
- Dereferensi penunjuk nol
- Memori yang tidak diinisialisasi
- Akses sumber daya kernel yang tidak aman
Membangun pengemudi
- Instal Visual Studio 2017
- Instal Windows Driver Kit
- Jalankan pembangun driver yang sesuai
Build_HEVD_Vulnerable_x86.bat atau Build_HEVD_Vulnerable_x64.bat
Unduh
Jika Anda tidak ingin membangun driver rentan Hacksys Extreme dari Source, Anda dapat mengunduh eksekusi yang sudah dibangun untuk rilis terbaru:
https://github.com/hacksysteam/hacksysextremevulnerableDriver/releases
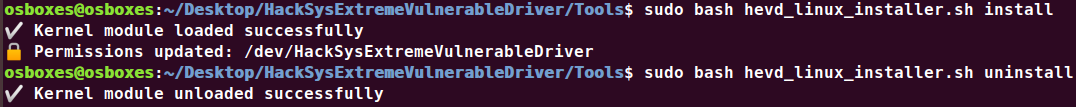
Menginstal driver
Gunakan OSR Driver Loader untuk menginstal Hacksys Extreme Rentan Driver
Pengujian
Driver rentan Hacksys Extreme dan eksploitasi masing -masing telah diuji pada Windows 7 SP1 X86 dan Windows 10 X64
Sesi dilakukan
- Eksploitasi Kernel Windows 1
- Eksploitasi Kernel Windows 2
- Eksploitasi Kernel Windows 3
- Eksploitasi Kernel Windows 4
- Eksploitasi Kernel Windows 5
- Eksploitasi Kernel Windows 6
- Eksploitasi Kernel Windows 7
Lokakarya dilakukan
- Windows Kernel Exploitation Humla Pune
- Eksploitasi kernel windows humla mumbai
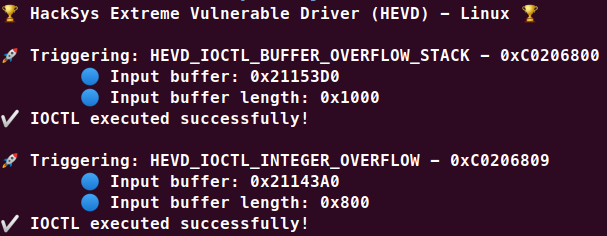
HEVD untuk Linux
Lisensi
Silakan lihat LICENSE file untuk menyalin izin
Pedoman Kontribusi
Silakan lihat file CONTRIBUTING.md untuk pedoman kontribusi
Laporan Todo & Bug
Harap ajukan permintaan tambahan atau laporan bug melalui pelacak edisi github di alamat di bawah ini: https://github.com/hacksysteam/hacksysextremevulnerableDriver/issues
Ucapan Terima Kasih
Terima kasih pergi ke orang -orang luar biasa ini :?