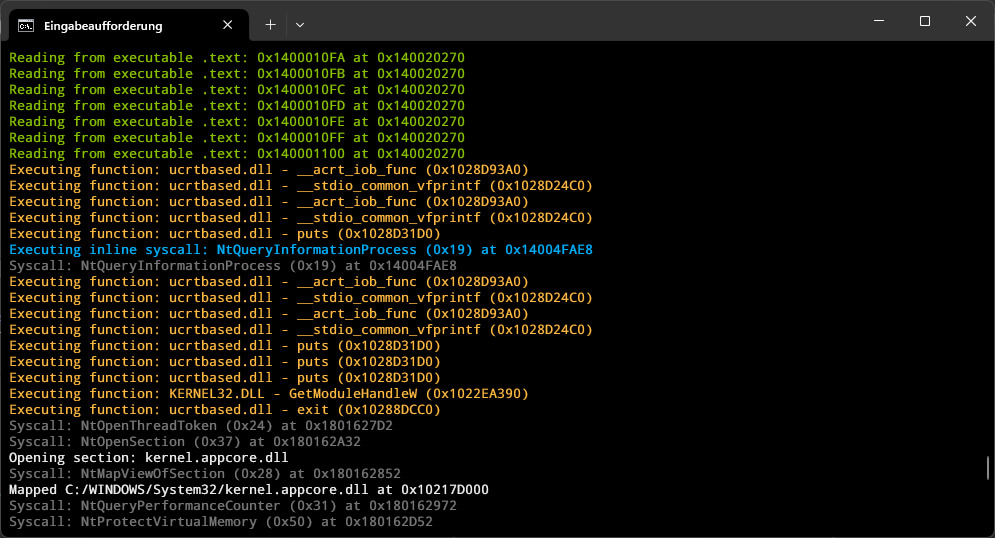
A high-performance Windows process emulator that operates at syscall level, providing full control over process execution through comprehensive hooking capabilities.
Built in C++ and powered by the Unicorn Engine.
Perfect for security research, malware analysis, and DRM research where fine-grained control over process execution is required.
Note
The project is still in a very early, prototypy state. The code still needs a lot of cleanup and many features and syscalls need to be implemented. However, constant progress is being made :)

Click here for the slides.
Clone the repository with submodules:
git clone https://github.com/momo5502/emulator.git
cd emulator
git submodule update --init --recursiveRun the following commands in an x64 Development Command Prompt
cmake --preset=vs2022Solution will be generated at build/vs2022/emulator.sln
Debug build:
cmake --workflow --preset=debugRelease build:
cmake --workflow --preset=releaseThe project uses CTest for testing. Choose your preferred method:
Visual Studio:
RUN_TESTS targetNinja:
cd build/release # or build/debug
ctest