
功能•安装•用法•配置•运行揭露•加入Discord
Uninover是使用众所周知的搜索引擎API快速发现Internet上暴露的主机的API。它是在自动化的情况下构建的,因此您可以通过当前的管道工具查询并利用结果。
发现需要GO1.21才能成功安装。运行以下命令以获取repo-
go install -v github.com/projectdiscovery/uncover/cmd/uncover@latestuncover -h这将显示该工具的帮助。这是它支持的所有标志:
Usage:
./uncover [flags]
Flags:
INPUT:
-q, -query string[] search query, supports: stdin,file,config input (example: -q 'example query', -q 'query.txt')
-e, -engine string[] search engine to query (shodan,shodan-idb,fofa,censys,quake,hunter,zoomeye,netlas,criminalip,publicwww,hunterhow,google) (default shodan)
SEARCH-ENGINE:
-s, -shodan string[] search query for shodan (example: -shodan 'query.txt')
-sd, -shodan-idb string[] search query for shodan-idb (example: -shodan-idb 'query.txt')
-ff, -fofa string[] search query for fofa (example: -fofa 'query.txt')
-cs, -censys string[] search query for censys (example: -censys 'query.txt')
-qk, -quake string[] search query for quake (example: -quake 'query.txt')
-ht, -hunter string[] search query for hunter (example: -hunter 'query.txt')
-ze, -zoomeye string[] search query for zoomeye (example: -zoomeye 'query.txt')
-ne, -netlas string[] search query for netlas (example: -netlas 'query.txt')
-cl, -criminalip string[] search query for criminalip (example: -criminalip 'query.txt')
-pw, -publicwww string[] search query for publicwww (example: -publicwww 'query.txt')
-hh, -hunterhow string[] search query for hunterhow (example: -hunterhow 'query.txt')
-gg, -google string[] search query for google (example: -google 'query.txt')
CONFIG:
-pc, -provider string provider configuration file (default "$CONFIG/uncover/provider-config.yaml")
-config string flag configuration file (default "$CONFIG/uncover/config.yaml")
-timeout int timeout in seconds (default 30)
-rl, -rate-limit int maximum number of http requests to send per second
-rlm, -rate-limit-minute int maximum number of requests to send per minute
-retry int number of times to retry a failed request (default 2)
OUTPUT:
-o, -output string output file to write found results
-f, -field string field to display in output (ip,port,host) (default "ip:port")
-j, -json write output in JSONL(ines) format
-r, -raw write raw output as received by the remote api
-l, -limit int limit the number of results to return (default 100)
-nc, -no-color disable colors in output
DEBUG:
-silent show only results in output
-version show version of the project
-v show verbose output 示例目录中提供了使用Unikover AS库的示例。
默认的提供商配置文件应位于$CONFIG/uncover/provider-config.yaml ,并以以下内容为例。
注意:需要API键,并且必须在运行揭幕前配置。
shodan :
- SHODAN_API_KEY_1
- SHODAN_API_KEY_2
censys :
- CENSYS_API_ID_1:CENSYS_API_SECRET_1
- CENSYS_API_ID_2:CENSYS_API_SECRET_2
fofa :
- FOFA_EMAIL_1:FOFA_KEY_1
- FOFA_EMAIL_2:FOFA_KEY_2
quake :
- QUAKE_TOKEN_1
- QUAKE_TOKEN_2
hunter :
- HUNTER_API_KEY_1
- HUNTER_API_KEY_2
zoomeye :
- ZOOMEYE_API_KEY_1
- ZOOMEYE_API_KEY_2
netlas :
- NETLAS_API_KEY_1
- NETLAS_API_KEY_2
criminalip :
- CRIMINALIP_API_KEY_1
- CRIMINALIP_API_KEY_2
publicwww :
- PUBLICWWW_API_KEY_1
- PUBLICWWW_API_KEY_2
hunterhow :
- HUNTERHOW_API_KEY_1
- HUNTERHOW_API_KEY_2
google :
- GOOGLE_API_KEY_1:Google_API_CX_1
- GOOGLE_API_KEY_2:Google_API_CX_2当配置文件中的同一提供商指定了多个键/凭据时,每个执行都将使用随机键。
另外,您还可以将API密钥设置为bash配置文件中的环境变量。
export SHODAN_API_KEY=xxx
export CENSYS_API_ID=xxx
export CENSYS_API_SECRET=xxx
export FOFA_EMAIL=xxx
export FOFA_KEY=xxx
export QUAKE_TOKEN=xxx
export HUNTER_API_KEY=xxx
export ZOOMEYE_API_KEY=xxx
export NETLAS_API_KEY=xxx
export CRIMINALIP_API_KEY=xxx
export PUBLICWWW_API_KEY=xxx
export HUNTERHOW_API_KEY=xxx
export GOOGLE_API_KEY=xxx
export GOOGLE_API_CX=xxx可以通过在以下平台,Censys,Fofa,Quake,Hunter,Zoomeye,Netlas,Netlas,pruferwww,PublicWWW和Google [1],[1],[2]上注册所需的API键。
unigover支持多种方法来制作查询,包括stdin或q flag,因为如果未指定任何引擎,则使用默认的shodan引擎进行搜索。
echo 'ssl:"Uber Technologies, Inc."' | uncover
__ ______ _________ _ _____ _____
/ / / / __ / ___/ __ | / / _ / ___/
/ /_/ / / / / /__/ /_/ / |/ / __/ /
__,_/_/ /_/___/____/|___/___/_/ v0.0.9
projectdiscovery.io
[WRN] Use with caution. You are responsible for your actions
[WRN] Developers assume no liability and are not responsible for any misuse or damage.
[WRN] By using uncover, you also agree to the terms of the APIs used.
107.180.12.116:993
107.180.26.155:443
104.244.99.31:443
161.28.20.79:443
104.21.8.108:443
198.71.233.203:443
104.17.237.13:443
162.255.165.171:443
12.237.119.61:443
192.169.250.211:443
104.16.251.50:443使用包含每行多个搜索查询的文件输入运行发现。
cat dorks.txt
ssl:"Uber Technologies, Inc."
title:"Grafana" uncover -q dorks.txt
__ ______ _________ _ _____ _____
/ / / / __ / ___/ __ | / / _ / ___/
/ /_/ / / / / /__/ /_/ / |/ / __/ /
__,_/_/ /_/___/____/|___/___/_/ v0.0.9
projectdiscovery.io
[WRN] Use with caution. You are responsible for your actions
[WRN] Developers assume no liability and are not responsible for any misuse or damage.
[WRN] By using uncover, you also agree to the terms of the APIs used.
107.180.12.116:993
107.180.26.155:443
104.244.99.31:443
161.28.20.79:443
104.21.8.108:443
198.71.233.203:443
2607:7c80:54:3::74:3001
104.198.55.35:80
46.101.82.244:3000
34.147.126.112:80
138.197.147.213:8086透明支持多个搜索引擎,因为使用了默认的shodan ,因此-e标志可用于针对任何或所有搜索引擎运行相同的查询。
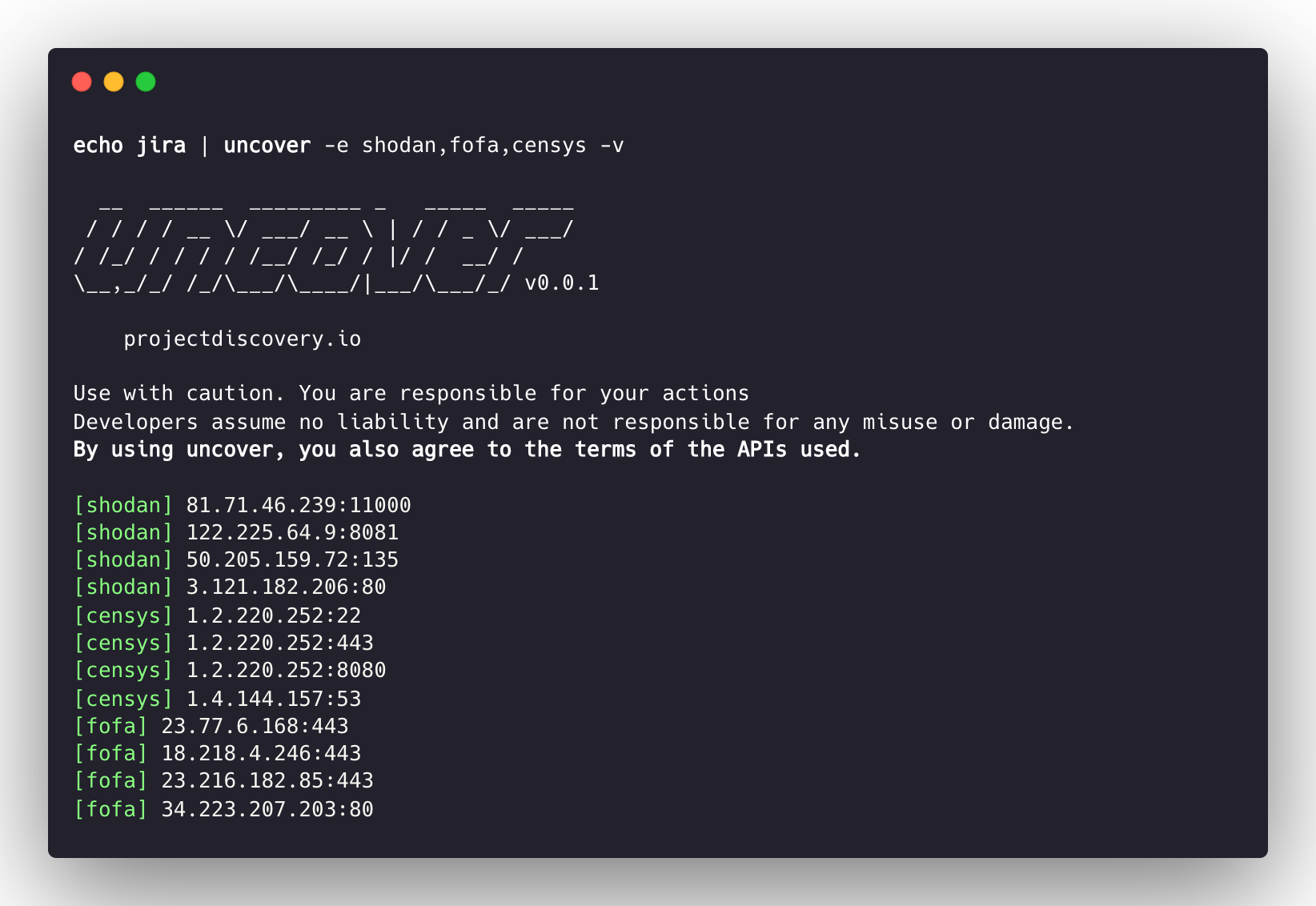
echo jira | uncover -e shodan,censys,fofa,quake,hunter,zoomeye,netlas,criminalip
__ ______ _________ _ _____ _____
/ / / / __ / ___/ __ | / / _ / ___/
/ /_/ / / / / /__/ /_/ / |/ / __/ /
__,_/_/ /_/___/____/|___/___/_/ v0.0.9
projectdiscovery.io
[WRN] Use with caution. You are responsible for your actions
[WRN] Developers assume no liability and are not responsible for any misuse or damage.
[WRN] By using uncover, you also agree to the terms of the APIs used.
176.31.249.189:5001
13.211.116.80:443
43.130.1.221:631
192.195.70.29:443
52.27.22.181:443
117.48.120.226:8889
106.52.115.145:49153
13.69.135.128:443
193.35.99.158:443
18.202.109.218:8089
101.36.105.97:21379
42.194.226.30:2626 uncover -shodan 'http.component:"Atlassian Jira"' -censys 'services.software.product=`Jira`' -fofa 'app="ATLASSIAN-JIRA"' -quake 'Jira' -hunter 'Jira' -zoomeye 'app:"Atlassian JIRA"' -netlas 'jira' -criminalip 'Jira'
__ ______ _________ _ _____ _____
/ / / / __ / ___/ __ | / / _ / ___/
/ /_/ / / / / /__/ /_/ / |/ / __/ /
__,_/_/ /_/___/____/|___/___/_/ v0.0.9
projectdiscovery.io
[WRN] Use with caution. You are responsible for your actions
[WRN] Developers assume no liability and are not responsible for any misuse or damage.
[WRN] By using uncover, you also agree to the terms of the APIs used.
104.68.37.129:443
162.222.160.42:443
34.255.84.133:443
52.204.121.166:443
23.198.29.120:443
136.156.180.95:443
54.194.233.15:443
104.117.55.155:443
149.81.4.6:443
54.255.218.95:443
3.223.137.57:443
83.228.124.171:443
23.202.195.82:443
52.16.59.25:443
18.159.145.227:443
104.105.53.236:443发现支持Shodan-InternetDB API为给定的IP/CIDR输入拉可用端口。
当将IP/CIDR作为输入提供时, shodan-idb用作默认引擎,否则将使用shodan搜索引擎。
echo 51.83.59.99/24 | uncover
__ ______ _________ _ _____ _____
/ / / / __ / ___/ __ | / / _ / ___/
/ /_/ / / / / /__/ /_/ / |/ / __/ /
__,_/_/ /_/___/____/|___/___/_/ v0.0.9
projectdiscovery.io
[WRN] Use with caution. You are responsible for your actions
[WRN] Developers assume no liability and are not responsible for any misuse or damage.
[WRN] By using uncover, you also agree to the terms of the APIs used.
51.83.59.1:53
51.83.59.1:10000
51.83.59.2:53
51.83.59.3:25
51.83.59.3:80
51.83.59.3:389
51.83.59.3:443
51.83.59.3:465
51.83.59.3:587
51.83.59.3:993-f, -field标志可用于指示支持哪些字段,当前, ip , port和host受支持,可用于返回所需的字段。
uncover -q jira -f host -silent
ec2-44-198-22-253.compute-1.amazonaws.com
ec2-18-246-31-139.us-west-2.compute.amazonaws.com
tasks.devrtb.com
leased-line-91-149-128-229.telecom.by
74.242.203.213.static.inetbone.net
ec2-52-211-7-108.eu-west-1.compute.amazonaws.com
ec2-54-187-161-180.us-west-2.compute.amazonaws.com
185-2-52-226.static.nucleus.be
ec2-34-241-80-255.eu-west-1.compute.amazonaws.comUninover具有一个-f, -field标志,可用于自定义输出格式。例如,在uncover -f https://ip:port/version ,ip:端口的情况下,将用输出中的结果替换,同时保持格式定义时,它也可以用于指定已知的方案/路径/路径/文件以准备输出,以便可以立即将其作为输入传递到管道中的其他工具。
echo kubernetes | uncover -f https://ip:port/version -silent
https://35.222.229.38:443/version
https://52.11.181.228:443/version
https://35.239.255.1:443/version
https://34.71.48.11:443/version
https://130.211.54.173:443/version
https://54.184.250.232:443/version可以将发现的输出进一步输送到工作流程中的其他项目,例如,接受stdin作为输入,例如:
uncover -q example -f ip | naabu在发现的主机上运行Naabu进行港口扫描。uncover -q title:GitLab | httpx运行HTTPX用于Web服务器,探索所找到的结果。uncover -q 51.83.59.99/24 | httpx在从Shodan -InternetDB获得的主机/端口上运行HTTPX。 uncover -q http.title:GitLab -silent | httpx -silent
https://15.185.150.109
https://139.162.137.16
https://164.68.115.243
https://135.125.215.186
https://163.172.59.119
http://15.236.10.197
https://129.206.117.248uncover -q 'org:"Example Inc."' | httpx | nuclei - 运行HTTPX /核进行脆弱性评估。 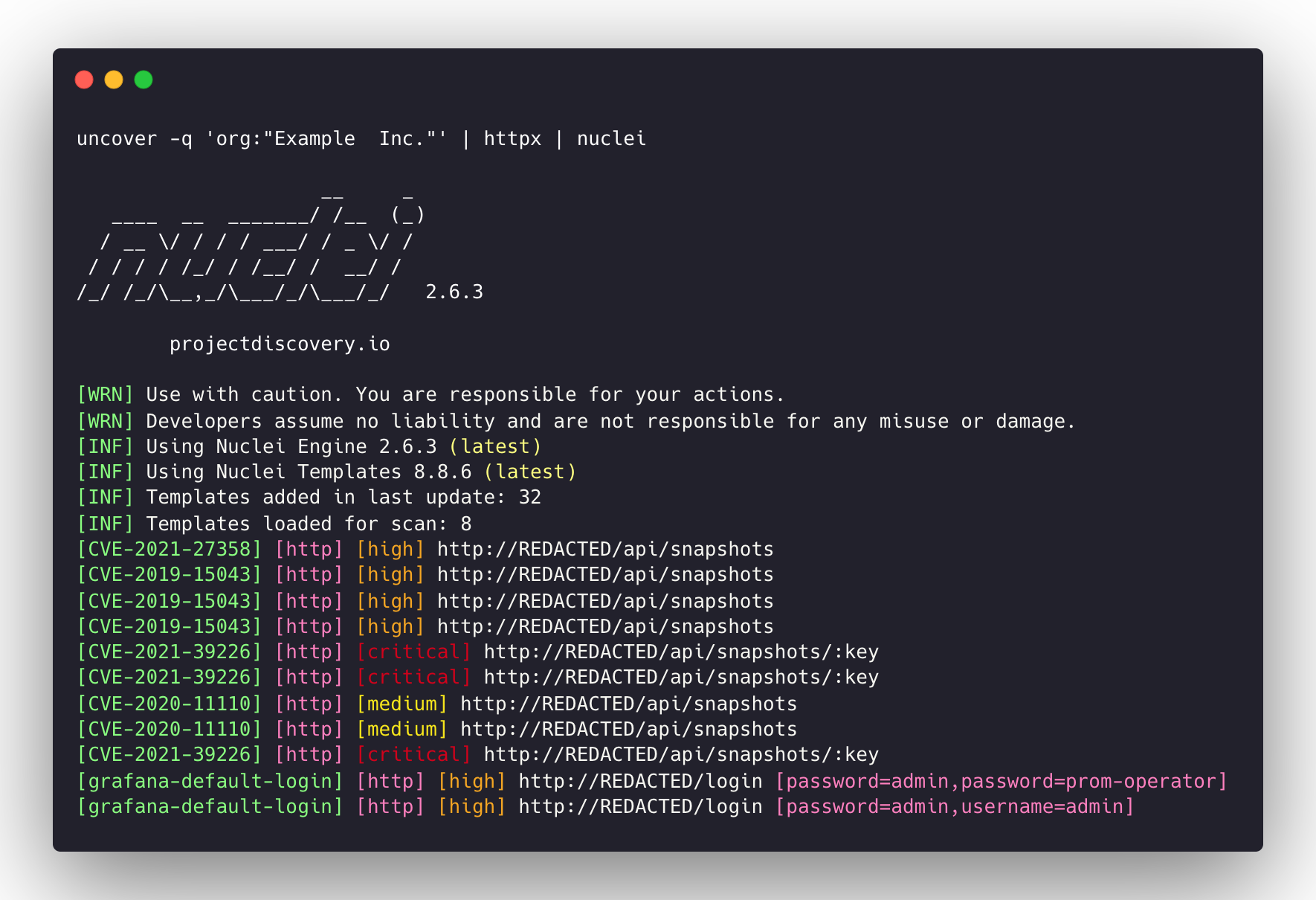
query标志支持搜索引擎支持的全部和仅过滤器。100 ,并且可以使用limit标志增加。shodan-idb API不需要API键并开箱即用。shodan-idb API用作默认引擎。发现是由?由Project Discovery团队。