☠️
██╗██████╗ ██╗ ███████╗███████╗███████╗██╗███╗ ██╗ ██████╗
██║██╔══██╗██║ ██╔════╝██╔════╝██╔════╝██║████╗ ██║██╔════╝
██║██████╔╝██║ █████╗ ███████╗███████╗██║██╔██╗ ██║██║ ███╗
██║██╔══██╗██║ ██╔══╝ ╚════██║╚════██║██║██║╚██╗██║██║ ██║
██║██████╔╝███████╗███████╗███████║███████║██║██║ ╚████║╚██████╔╝
╚═╝╚═════╝ ╚══════╝╚══════╝╚══════╝╚══════╝╚═╝╚═╝ ╚═══╝ ╚═════╝
iblessing adalah toolkit yang mengeksploitasi keamanan iOS, terutama termasuk pengumpulan informasi aplikasi , analisis statis dan analisis dinamis .iblessing didasarkan pada mesin unicorn, mesin batu penjuru dan mesin kunci.Cross-Platform: Diuji pada MacOS dan Ubuntu.
Ekstrak info statis aplikasi iOS, termasuk metadata, deeplinks, URL, dll.
Mach-O Parser dan Dyld Symbol Bind Simulator
Kelas Objective-C Menyadari dan Parsing
Pemindai membuat analisis dinamis untuk kode perakitan ARM64 dan temukan informasi utama atau permukaan serangan
Pemindai menggunakan unicorn untuk mensimulasikan sebagian eksekusi kode Mach-O Arm64 dan menemukan beberapa fitur
Generator yang dapat memberikan pemrosesan sekunder pada laporan pemindai untuk memulai server kueri, atau menghasilkan skrip untuk IDA
Pemindai Super Objc_MSGSend XREFS?
Tes
Pemindai Android Support
Log Diagnostik
Infrastruktur pemindai yang lebih fleksibel untuk plugin pemindai baru
Jika Anda membutuhkan dukungan tentang iblessing atau apa pun yang terkait dengannya, Anda dapat:
Untuk mulai menyusun iblessing, silakan ikuti langkah -langkah di bawah ini:
git clone --recursive -j4 https://github.com/Soulghost/iblessing
cd iblessing
./compile-cmake.sh
Konsep Dasar
Pemindai
Generator
Jika ada kesalahan, Anda dapat dengan memandangi Capstone dan Unicorn, maka seret libcapstone.a dan libunicorn.a ke vendor/lib proyek proyek XCODE.
Jika semua ini berhasil berjalan, Anda dapat menemukan biner dalam Direktori Build:
> ls ./build
iblessing
> file ./build/iblessing
./build/iblessing: Mach-O 64-bit executable x86_64
$ iblessing -h
☠️
██╗██████╗ ██╗ ███████╗███████╗███████╗██╗███╗ ██╗ ██████╗
██║██╔══██╗██║ ██╔════╝██╔════╝██╔════╝██║████╗ ██║██╔════╝
██║██████╔╝██║ █████╗ ███████╗███████╗██║██╔██╗ ██║██║ ███╗
██║██╔══██╗██║ ██╔══╝ ╚════██║╚════██║██║██║╚██╗██║██║ ██║
██║██████╔╝███████╗███████╗███████║███████║██║██║ ╚████║╚██████╔╝
╚═╝╚═════╝ ╚══════╝╚══════╝╚══════╝╚══════╝╚═╝╚═╝ ╚═══╝ ╚═════╝
[***] iblessing iOS Security Exploiting Toolkit Beta 0.1.1 (http://blog.asm.im)
[***] Author: Soulghost (高级页面仔) @ (https://github.com/Soulghost)
Usage: iblessing [options...]
Options:
-m, --mode mode selection:
* scan: use scanner
* generator: use generator
-i, --identifier choose module by identifier:
* <scanner-id>: use specific scanner
* <generator-id>: use specific generator
-f, --file input file path
-o, --output output file path
-l, --list list available scanners
-d, --data extra data
-h, --help Shows this page
Pemindai adalah komponen yang digunakan untuk meng-output laporan analisis melalui analisis statis dan dinamis dari file biner, misalnya, pemindai OBJC-MSG-XREF dapat menganalisis sebagian besar referensi silang OBJC_MSGSEND.
[*] Scanner List:
- app-info: extract app infos
- objc-class-xref: scan for class xrefs
- objc-msg-xref: generate objc_msgSend xrefs record
- predicate: scan for NSPredicate xrefs and sql injection surfaces
- symbol-wrapper: detect symbol wrappers
Generator adalah komponen yang melakukan pemrosesan sekunder pada laporan yang dihasilkan oleh pemindai, misalnya, dapat menghasilkan skrip IDA berdasarkan laporan referensi silang OBJC-MSG-XREF pemindai.
[*] Generator List:
- ida-objc-msg-xref: generator ida scripts to add objc_msgSend xrefs from objc-msg-xref scanner's report
- objc-msg-xref-server: server to query objc-msg xrefs
- objc-msg-xref-statistic: statistics among objc-msg-send reports
> iblessing -m scan -i app-info -f <path-to-app-bundle>
Mari kita ambil WeChat sebagai contoh:
> iblessing -m scan -i app-info -f WeChat.app
[*] set output path to /opt/one-btn/tmp/apps/WeChat/Payload
[*] input file is WeChat.app
[*] start App Info Scanner
[+] find default plist file Info.plist!
[*] find version info: Name: 微信(WeChat)
Version: 7.0.14(18E226)
ExecutableName: WeChat
[*] Bundle Identifier: com.tencent.xin
[*] the app allows HTTP requests **without** exception domains!
[+] find app deeplinks
|-- wechat://
|-- weixin://
|-- fb290293790992170://
|-- weixinapp://
|-- prefs://
|-- wexinVideoAPI://
|-- QQ41C152CF://
|-- wx703://
|-- weixinULAPI://
[*] find app callout whitelist
|-- qqnews://
|-- weixinbeta://
|-- qqnewshd://
|-- qqmail://
|-- whatsapp://
|-- wxwork://
|-- wxworklocal://
|-- wxcphonebook://
|-- mttbrowser://
|-- mqqapi://
|-- mqzonev2://
|-- qqmusic://
|-- tenvideo2://
...
[+] find 507403 string literals in binary
[*] process with string literals, this maybe take some time
[+] find self deeplinks URLs:
|-- weixin://opennativeurl/devicerankview
|-- weixin://dl/offlinepay/?appid=%@
|-- weixin://opennativeurl/rankmyhomepage
...
[+] find other deeplinks URLs:
|-- wxpay://f2f/f2fdetail
|-- file://%@?lang=%@&fontRatio=%.2f&scene=%u&version=%u&type=%llu&%@=%d&qqFaceFolderPath=%@&platform=iOS&netType=%@&query=%@&searchId=%@&isHomePage=%d&isWeAppMore=%d&subType=%u&extParams=%@&%@=%@&%@=%@
...
[*] write report to path /opt/one-btn/tmp/apps/WeChat/Payload/WeChat.app_info.iblessing.txt
> ls -alh
-rw-r--r--@ 1 soulghost wheel 29K Jul 23 14:01 WeChat.app_info.iblessing.txt
PEMBERITAHUAN: Binari ARM64 saja
iblessing -m scan -i objc-class-xref -f <path-to-binary> -d 'classes=<classname_to_scan>,<classname_to_scan>,...'
> restore-symbol WeChat -o WeChat.restored
> iblessing -m scan -i objc-class-xref -f WeChat.restored -d 'classes=NSPredicate'
[*] set output path to /opt/one-btn/tmp/apps/WeChat/Payload
[*] input file is WeChat
[+] detect mach-o header 64
[+] detect litten-endian
[*] start Objc Class Xref Scanner
[*] try to find _OBJC_CLASS_$_NSPredicate
[*] Step 1. locate class refs
[+] find _OBJC_CLASS_$_NSPredicate at 0x108eb81d8
[*] Step 2. find __TEXT,__text
[+] find __TEXT,__text at 0x4000
[*] Step 3. scan in __text
[*] start disassembler at 0x100004000
[*] 0x1002e1a50/0x1069d9874 (2.71%) [+] find _OBJC_CLASS_$_NSPredicate ref at 0x1002e1a54
...
[*] Step 4. symbolicate ref addresses
[+] _OBJC_CLASS_$_NSPredicate -|
[+] find _OBJC_CLASS_$_NSPredicate ref -[WCWatchNotificationMgr addYoCount:contact:type:] at 0x1002e1a54
[+] find _OBJC_CLASS_$_NSPredicate ref -[NotificationActionsMgr handleSendMsgResp:] at 0x1003e0e28
[+] find _OBJC_CLASS_$_NSPredicate ref -[FLEXClassesTableViewController searchBar:textDidChange:] at 0x1004a090c
[+] find _OBJC_CLASS_$_NSPredicate ref +[GameCenterUtil parameterValueForKey:fromQueryItems:] at 0x1005a823c
[+] find _OBJC_CLASS_$_NSPredicate ref +[GameCenterUtil getNavigationBarColorForUrl:defaultColor:] at 0x1005a8cd8
...
PEMBERITAHUAN: Binari ARM64 saja
iblessing -m scan -i objc-msg-xref -f <path-to-binary>
iblessing -m scan -i objc-msg-xref -f WeChat -d 'antiWrapper=1'
Mode anti-wrapper akan mendeteksi pembungkus OBJC_MSGSEND dan membuat transformasi, seperti:
; __int64 __usercall objc_msgSend_X0_X22_X20@<X0>(void *obj@<X0>, const char *sel@<X22>, id anyObj@<X20>, ...)
objc_msgSend_X0_X22_X20:
MOV X1, X22
MOV X2, X20
B objc_msgSend
> iblessing -m scan -i objc-msg-xref -f WeChat -d 'antiWrapper=1'
[*] set output path to /opt/one-btn/tmp/apps/WeChat/Payload
[*] input file is WeChat
[+] detect mach-o header 64
[+] detect litten-endian
[*] !!! Notice: enter anti-wrapper mode, start anti-wrapper scanner
[*] start Symbol Wrapper Scanner
[*] try to find wrappers for_objc_msgSend
[*] Step1. find __TEXT,__text
[+] find __TEXT,__text at 0x100004000
[+] mapping text segment 0x100000000 ~ 0x107cb0000 to unicorn engine
[*] Step 2. scan in __text
[*] start disassembler at 0x100004000
[*] / 0x1069d986c/0x1069d9874 (100.00%)
[*] reach to end of __text, stop
[+] anti-wrapper finished
[*] start ObjcMethodXrefScanner Exploit Scanner
[*] Step 1. realize all app classes
[*] realize classes 14631/14631 (100.00%)
[+] get 667318 methods to analyze
[*] Step 2. dyld load non-lazy symbols
[*] Step 3. track all calls
[*] progress: 667318 / 667318 (100.00%)
[*] Step 4. serialize call chains to file
[*] saved to /opt/one-btn/tmp/apps/WeChat/Payload/WeChat_method-xrefs.iblessing.txt
> ls -alh WeChat_method-xrefs.iblessing.txt
-rw-r--r-- 1 soulghost wheel 63M Jul 23 14:46 WeChat_method-xrefs.iblessing.txt
> head WeChat_method-xrefs.iblessing.txt
iblessing methodchains,ver:0.2;
chainId,sel,prefix,className,methodName,prevMethods,nextMethods
182360,0x1008a0ab8,+[A8KeyControl initialize],+,A8KeyControl,initialize,[],[4429#0x1008a1064@4376#0x1008a1050@13769#0x1008a10d0]
182343,0x1008a0ad0,+[A8KeyControl_QueryStringTransferCookie initialize],+,A8KeyControl_QueryStringTransferCookie,initialize,[],[4429#0x1008a1064@4376#0x1008a1050@13769#0x1008a10d0]
145393,0x1008c2220,+[A8KeyResultCookieWriter initWithDomain:weakWebView:andCompleteBlock:],+,A8KeyResultCookieWriter,initWithDomain:weakWebView:andCompleteBlock:,[145386#0x10036367c],[]
145396,0x1008c3df8,+[A8KeyResultCookieWriter setA8KeyCookieExpireTime:],+,A8KeyResultCookieWriter,setA8KeyCookieExpireTime:,[145386#0x1003636e8],[]
145397,0x1008c27e8,+[A8KeyResultCookieWriter writeCompleteMarkerCookieValue:forKey:],+,A8KeyResultCookieWriter,writeCompleteMarkerCookieValue:forKey:,[145386#0x10036380c],[]
253456,0x0,+[AAOperationReq init],+,AAOperationReq,init,[253455#0x1039a9d30],[]
253457,0x0,+[AAOperationReq setBaseRequest:],+,AAOperationReq,setBaseRequest:,[253455#0x1039a9d8c],[]
186847,0x0,+[AAOperationRes length],+,AAOperationRes,length,[186845#0x10342aa54],[]
Laporan ini dapat digunakan oleh generator, sekarang mari kita pergi.
Anda dapat memulai server melalui generator OBJC-MSG-XREF-Server Iblessing untuk menanyakan semua objc_msgsend xrefs.
iblessing -m generator -i objc-msg-xref-server -f <path-to-report-generated-by-objc-msg-xref-scanner>
Alamat mendengarkan default adalah 127.0.0.1:2345, Anda dapat menentukannya dengan opsi -D.
iblessing -m generator -i objc-msg-xref-server -f WeChat_method-xrefs.iblessing.txt -d 'host=0.0.0.0;port=12345'
PEMBERITAHUAN: OBJC-MSG-XREF didasarkan pada unicorn, untuk mempercepat analisis, kami tidak mengikuti panggilan apa pun, sehingga hasilnya sebagian hilang.
> iblessing -m generator -i objc-msg-xref-server -f WeChat_method-xrefs.iblessing.txt
[*] set output path to /opt/one-btn/tmp/apps/WeChat/Payload
[*] input file is WeChat_method-xrefs.iblessing.txt
[*] start ObjcMsgXREFServerGenerator
[*] load method-chain db for version iblessing methodchains,ver:0.2;
[*] table keys chainId,sel,prefix,className,methodName,prevMethods,nextMethods
[-] bad line 104467,0x0,+[TPLock P, ],+,TPLock,P, ,[104426#0x1043b9904],[]
[-] bad line 114905,0x0,?[0x108ce1578 (,],?,0x108ce1578,(,,[114900#0x1011e8c68],[]
[-] bad line 104464,0x0,?[? P, ],?,?,P, ,[104426#0x1043b98a8],[]
[-] bad line 139234,0x0,?[? X
[-] bad line ],?,?,X
[-] bad line ,[139205#0x1013c222c],[]
[+] load storage from disk succeeded!
[*] listening on http://127.0.0.1:2345
Selanjutnya Anda dapat membuka http://127.0.0.1:2345 dengan browser untuk menanyakan objc_msgsend xrefs yang Anda sukai: 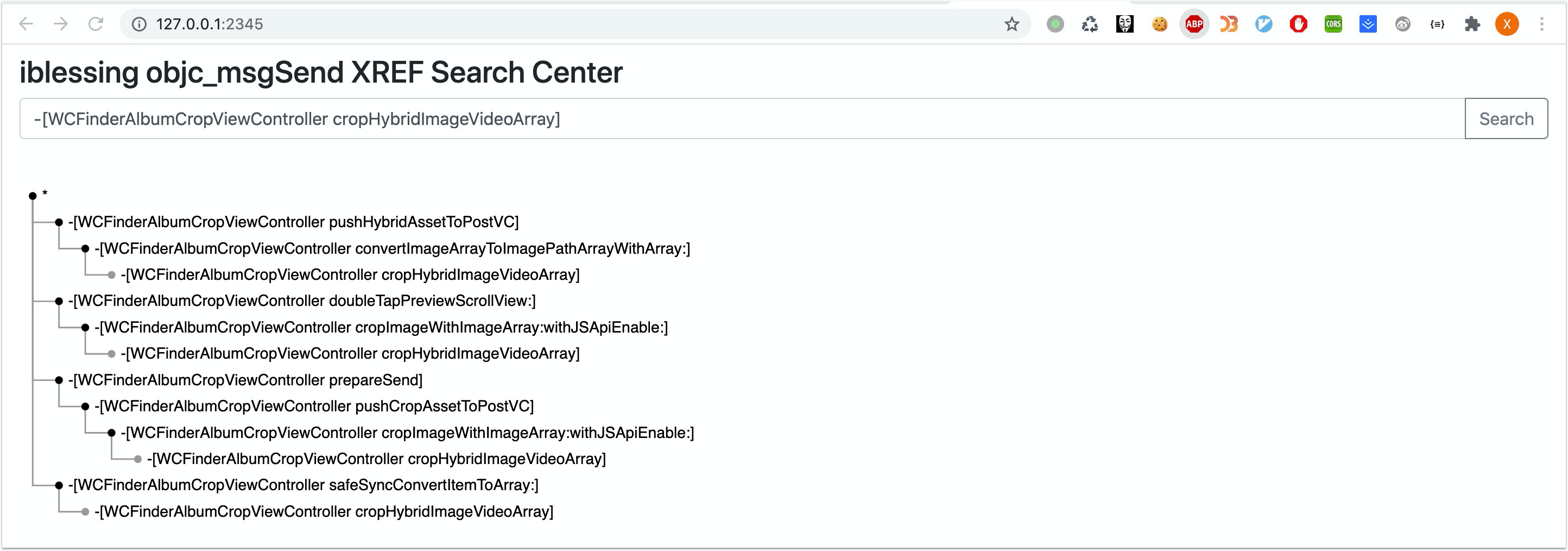
Anda dapat menambahkan objc_msgsend xrefs yang dihasilkan dari pemindai OBJC-MSG-XREF untuk membuat perjalanan rekayasa terbalik Anda lebih cepat dan nyaman.
iblessing -m generator -i ida-objc-msg-xref -f <path-to-report-generated-by-objc-msg-xref-scanner>
PEMBERITAHUAN: OBJC-MSG-XREF didasarkan pada unicorn, untuk mempercepat analisis, kami tidak mengikuti panggilan apa pun, sehingga hasilnya sebagian hilang.
> iblessing -m generator -i ida-objc-msg-xref -f WeChat_method-xrefs.iblessing.txt
[*] set output path to /opt/one-btn/tmp/apps/WeChat/Payload
[*] input file is WeChat_method-xrefs.iblessing.txt
[*] start IDAObjMsgXREFGenerator
[*] load method-chain db for version iblessing methodchains,ver:0.2;
[*] table keys chainId,sel,prefix,className,methodName,prevMethods,nextMethods
[-] bad line 104467,0x0,+[TPLock P, ],+,TPLock,P, ,[104426#0x1043b9904],[]
[-] bad line 114905,0x0,?[0x108ce1578 (,],?,0x108ce1578,(,,[114900#0x1011e8c68],[]
[-] bad line 104464,0x0,?[? P, ],?,?,P, ,[104426#0x1043b98a8],[]
[-] bad line 139234,0x0,?[? X
[-] bad line ],?,?,X
[-] bad line ,[139205#0x1013c222c],[]
[+] load storage from disk succeeded!
[*] Generating XREF Scripts ...
[*] saved to /opt/one-btn/tmp/apps/WeChat/Payload/WeChat_method-xrefs.iblessing.txt_ida_objc_msg_xrefs.iblessing.py
> ls -alh WeChat_method-xrefs.iblessing.txt_ida_objc_msg_xrefs.iblessing.py
-rw-r--r-- 1 soulghost wheel 23M Jul 23 16:16 WeChat_method-xrefs.iblessing.txt_ida_objc_msg_xrefs.iblessing.py
> head WeChat_method-xrefs.iblessing.txt_ida_objc_msg_xrefs.iblessing.py
def add_objc_xrefs():
ida_xref.add_cref(0x10036367c, 0x1008c2220, XREF_USER)
ida_xref.add_cref(0x1003636e8, 0x1008c3df8, XREF_USER)
ida_xref.add_cref(0x10036380c, 0x1008c27e8, XREF_USER)
ida_xref.add_cref(0x103add16c, 0x700006e187a8, XREF_USER)
ida_xref.add_cref(0x102cbee0c, 0x101143ee8, XREF_USER)
ida_xref.add_cref(0x10085c92c, 0x1005e9360, XREF_USER)
ida_xref.add_cref(0x10085c8bc, 0x1005e9274, XREF_USER)
ida_xref.add_cref(0x10085c8dc, 0x1005e92bc, XREF_USER)
ida_xref.add_cref(0x10085c8cc, 0x1005e9298, XREF_USER)
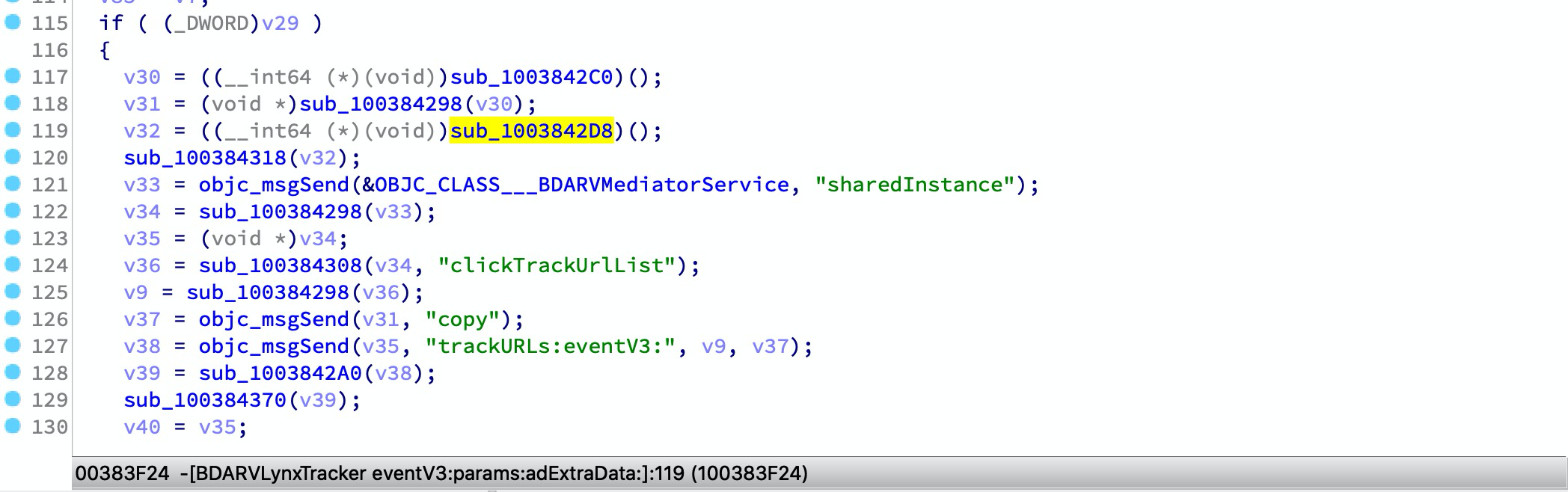
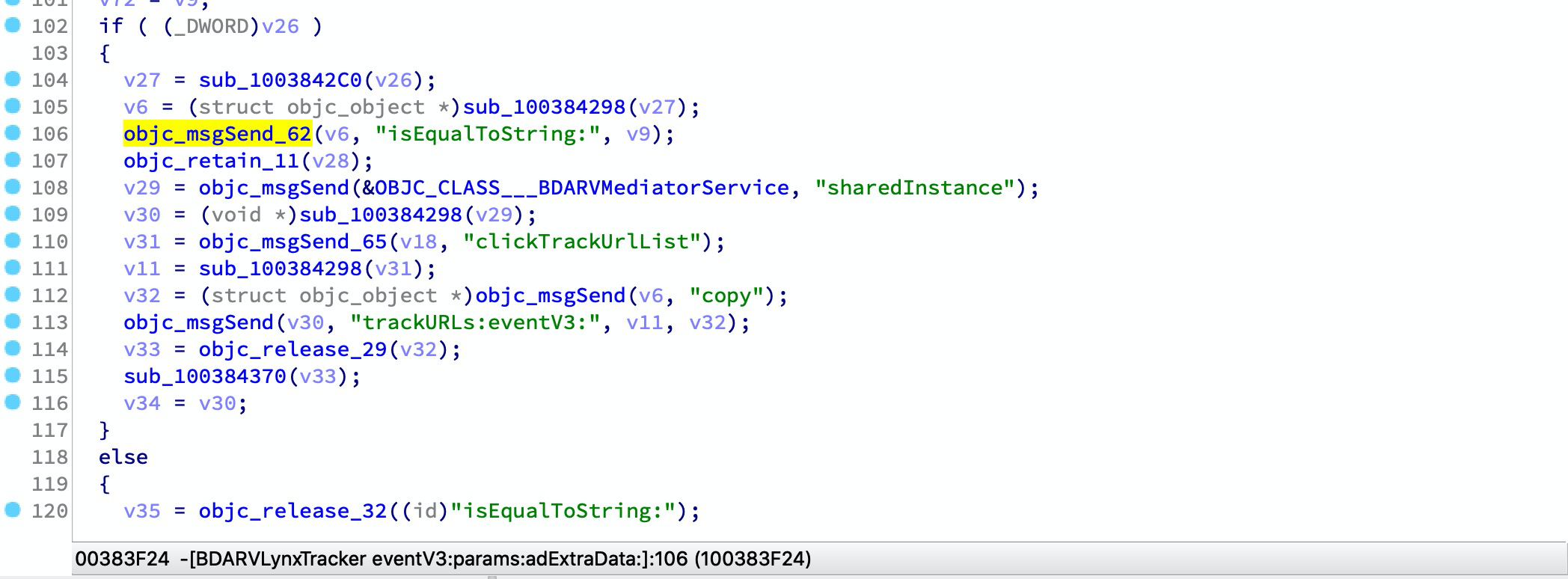
Selanjutnya buka file IDA Anda -> file -> skrip dan muat skrip, langkah ini mungkin memakan waktu lama. Dan setelah selesai, Anda dapat menemukan banyak XREF untuk metode OBJC: 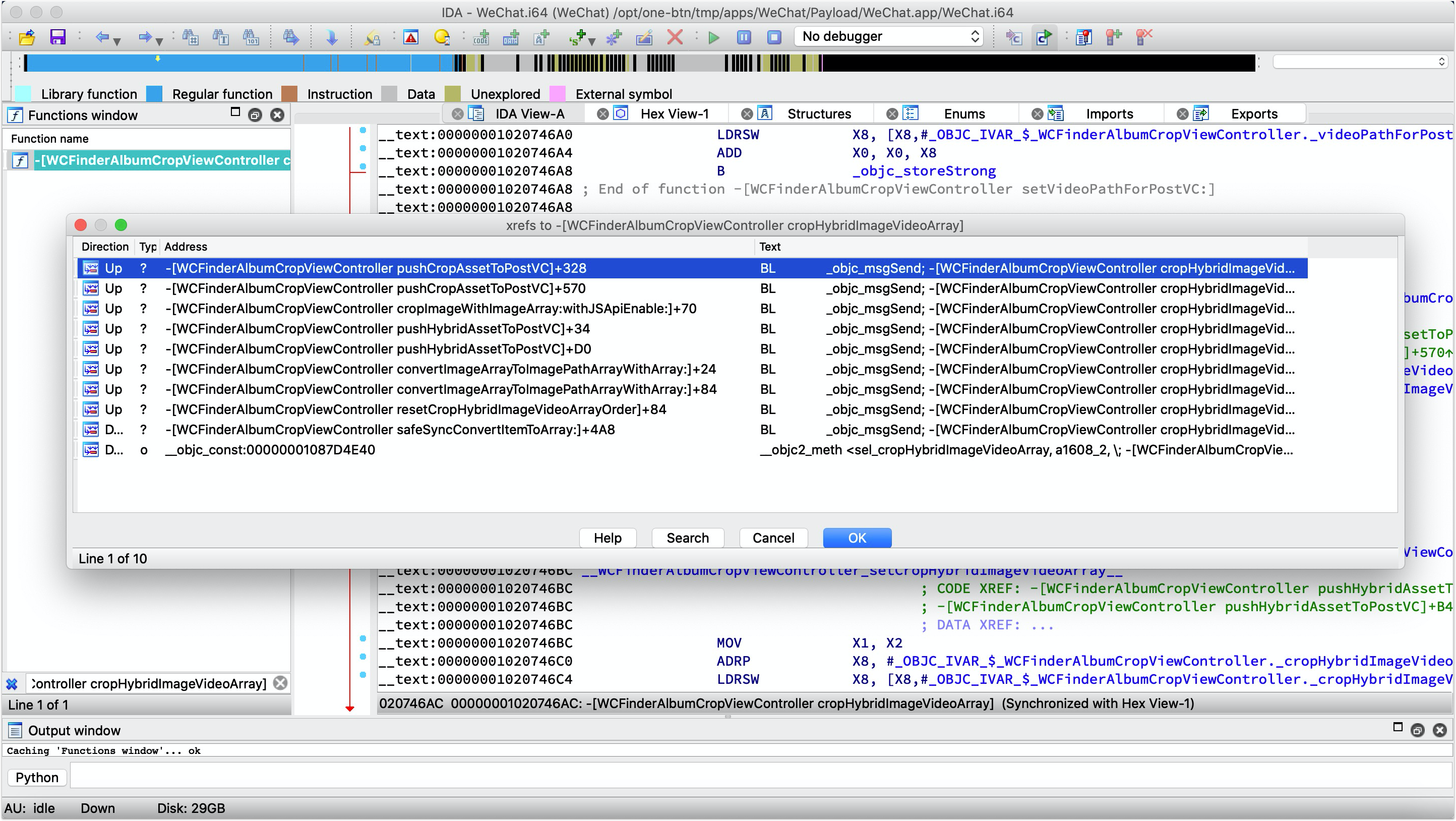
File Mach-O dapat berisi beberapa pembungkus dari simbol impor perpustakaan dinamis yang umum digunakan, seperti:
__text:00000001003842D8 sub_1003842CC ; CODE XREF: -[BDARVLynxTracker eventV3:params:adExtraData:]+168↑p
__text:00000001003842D8 ; -[BDARVLynxTracker eventV3:params:adExtraData:]+214↑p ...
__text:00000001003842D8 MOV X1, X27
__text:00000001003842DC MOV X2, X19
__text:00000001003842E0 B objc_msgSend
Kami dapat mengonversi pembungkusnya dengan UserCall:
__text:00000001003842CC ; id __usercall objc_msgSend_61@<X0>(id@<X23>, const char *@<X28>, ...)
__text:00000001003842CC _objc_msgSend_61 ; CODE XREF: -[BDARVLynxTracker eventV3:params:adExtraData:]+2CC↑p
__text:00000001003842CC ; -[BDARVLynxTracker eventV3:params:adExtraData:]+320↑p ...
__text:00000001003842CC MOV X0, X23
__text:00000001003842D0 MOV X1, X28
__text:00000001003842D4 B objc_msgSend
Pemindai dapat menghasilkan laporan untuk merekam semua pembungkus, maka Anda dapat menggunakan generator ida-symbol-wrapper-naming untuk menghasilkan skrip IDA dan mengimplementasikan perubahan nama pembungkus ini dan perubahan prototipe.
iblessing -m scan -i symbol-wrapper -f <path-to-binary> -d 'symbols=_objc_msgSend,_objc_retain,_objc_release'
iblessing -m scan -i symbol-wrapper -f <path-to-binary> -d 'symbols=*'
Kami akan mengambil Tiktok China sebagai contoh:
> iblessing -m scan -i symbol-wrapper -f /opt/one-btn/tmp/apps/抖音短视频/Payload/Aweme -d 'symbols=*'
[*] set output path to /Users/soulghost/Desktop/git/iblessing-public/iblessing/build/Debug
[*] input file is /opt/one-btn/tmp/apps/抖音短视频/Payload/Aweme
[+] detect mach-o header 64
[+] detect litten-endian
[*] start Symbol Wrapper Scanner
[*] try to find wrappers for_objc_autoreleaseReturnValue, _objc_msgSend, _objc_release, _objc_releaseAndReturn, _objc_retain, _objc_retainAutorelease, _objc_retainAutoreleaseAndReturn, _objc_retainAutoreleaseReturnValue, _objc_retainAutoreleasedReturnValue
[*] Step1. find __TEXT,__text
[+] find __TEXT,__text at 0x100004000
[+] mapping text segment 0x100000000 ~ 0x106da0000 to unicorn engine
[*] Step 2. scan in __text
[*] start disassembler at 0x100004000
[*] / 0x106b68a54/0x106b68a58 (100.00%)
[*] reach to end of __text, stop
[*] Step 3. serialize wrapper graph to file
[*] saved to /Users/soulghost/Desktop/git/iblessing-public/iblessing/build/Debug/Aweme_wrapper-graph.iblessing.txt
> head Aweme_wrapper-graph.iblessing.txt
iblessing symbol-wrappers,ver:0.1;
wrapperId;address;name;prototype
0;0x100022190;_objc_retainAutoreleasedReturnValue;id __usercall f@<x0>(id@<x0>)
1;0x100022198;_objc_retainAutoreleasedReturnValue;id __usercall f@<x0>(id@<x0>)
2;0x1000221a0;_objc_release;id __usercall f@<x0>(id@<x22>)
3;0x1000221a8;_objc_msgSend;id __usercall f@<x0>(id@<x0>, const char*@<x20>, ...)
4;0x100022448;_objc_release;id __usercall f@<x0>(id@<x21>)
5;0x10009c19c;_objc_autoreleaseReturnValue;id __usercall f@<x0>(id@<x0>)
6;0x1000b6f94;_objc_msgSend;id __usercall f@<x0>(id@<x0>, const char*@<x1>, ...)
7;0x100100248;_objc_autoreleaseReturnValue;id __usercall f@<x0>(id@<x0>)
Selanjutnya, kita dapat menghasilkan skrip IDA dari laporan ini.
iblessing -m generator -i ida-symbol-wrapper-naming -f <path-to-report-from-symbol-wrapper>
> iblessing -m generator -i ida-symbol-wrapper-naming -f Aweme_wrapper-graph.iblessing.txt
[*] set output path to /Users/soulghost/Desktop/git/iblessing-public/iblessing/build/Debug
[*] input file is Aweme_wrapper-graph.iblessing.txt
[*] start IDAObjMsgXREFGenerator
[*] load symbol-wrappers db for version iblessing symbol-wrappers,ver:0.1;
[*] table keys wrapperId;address;name;prototype
[*] Generating Naming Scripts ...
[*] saved to /Users/soulghost/Desktop/git/iblessing-public/iblessing/build/Debug/Aweme_wrapper-graph.iblessing.txt_ida_symbol_wrapper_naming.iblessing.py
> head Aweme_wrapper-graph.iblessing.txt_ida_symbol_wrapper_naming.iblessing.py
def namingWrappers():
idc.set_name(0x100022190, '_objc_retainAutoreleasedReturnValue', ida_name.SN_FORCE)
idc.apply_type(0x100022190, idc.parse_decl('id __usercall f@<x0>(id@<x0>)', idc.PT_SILENT))
idc.set_name(0x100022198, '_objc_retainAutoreleasedReturnValue', ida_name.SN_FORCE)
idc.apply_type(0x100022198, idc.parse_decl('id __usercall f@<x0>(id@<x0>)', idc.PT_SILENT))
idc.set_name(0x1000221a0, '_objc_release', ida_name.SN_FORCE)
idc.apply_type(0x1000221a0, idc.parse_decl('id __usercall f@<x0>(id@<x22>)', idc.PT_SILENT))
idc.set_name(0x1000221a8, '_objc_msgSend', ida_name.SN_FORCE)
idc.apply_type(0x1000221a8, idc.parse_decl('id __usercall f@<x0>(id@<x0>, const char*@<x20>, ...)', idc.PT_SILENT))
idc.set_name(0x100022448, '_objc_release', ida_name.SN_FORCE)
Selanjutnya buka file IDA Anda -> file -> skrip dan muat skrip, langkah ini mungkin memakan waktu lama. Dan ketika itu selesai, Anda dapat mengamati beberapa perubahan kode yang didekompilasi: