
OpenSource解決方案定義和管理所用資源的完整生命週期,並提供為雲!
探索文檔»
SLD有助於加速部署,加權和使IAAC重複使用,生成動態形式並使用相同的代碼在每個環境中維護不同的變量。使用SLD,您可以安排基礎架構部署,例如破壞,通過角色管理用戶,並通過小隊和環境單獨管理堆棧
主要功能:
SLD是使用Terrafrom代碼的簡便方法!
您需要Docker和Docker-Compse或ank(推薦)。
克隆SLD倉庫
git clone https://github.com/D10S0VSkY-OSS/Stack-Lifecycle-Deployment.git在K8中部署SLD
cd Stack-Lifecycle-Deployment/play-with-sld/kubernetes
sh kplay.sh start結果:
Starting SLD for play
Creating cluster " kind " ...
✓ Ensuring node image (kindest/node:v1.20.2) ?
✓ Preparing nodes ? ?
✓ Writing configuration
✓ Starting control-plane ?️
✓ Installing CNI ?
✓ Installing StorageClass ?
✓ Joining worker nodes ?
Set kubectl context to " kind-kind "
You can now use your cluster with:
kubectl cluster-info --context kind-kind創建初始用戶
sh kplay.sh init結果:
kind ok
docker ok
kubectl ok
jq ok
curl ok
init SLD
# ################################################
# Now, you can play with SLD ?️ #
# ################################################
API: http://localhost:5000/docs
DASHBOARD: http://localhost:5000/
---------------------------------------------
username: admin
password: Password08@
---------------------------------------------
列表內註
sh kplay.sh list結果:
kind ok
docker ok
kubectl ok
List endpoints
API: http://localhost:8000/docs
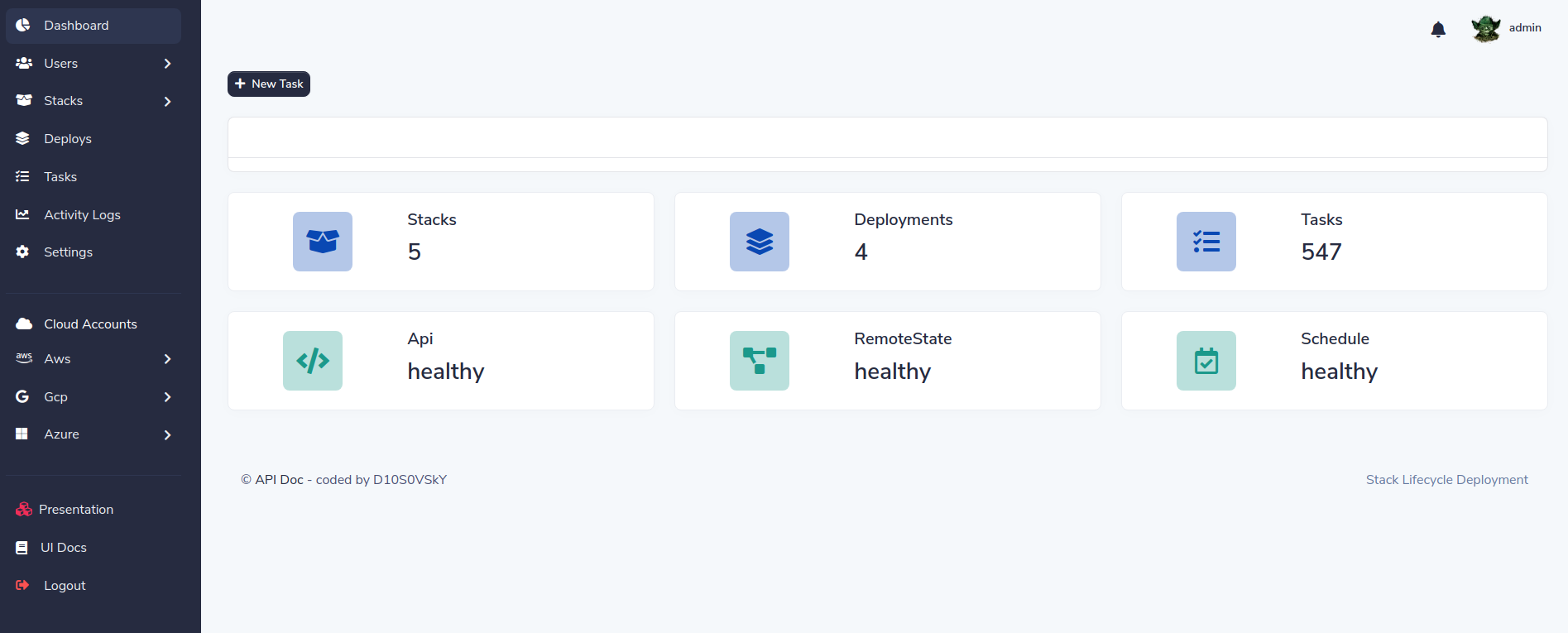
DASHBOARD: http://localhost:5000/登錄儀表板:
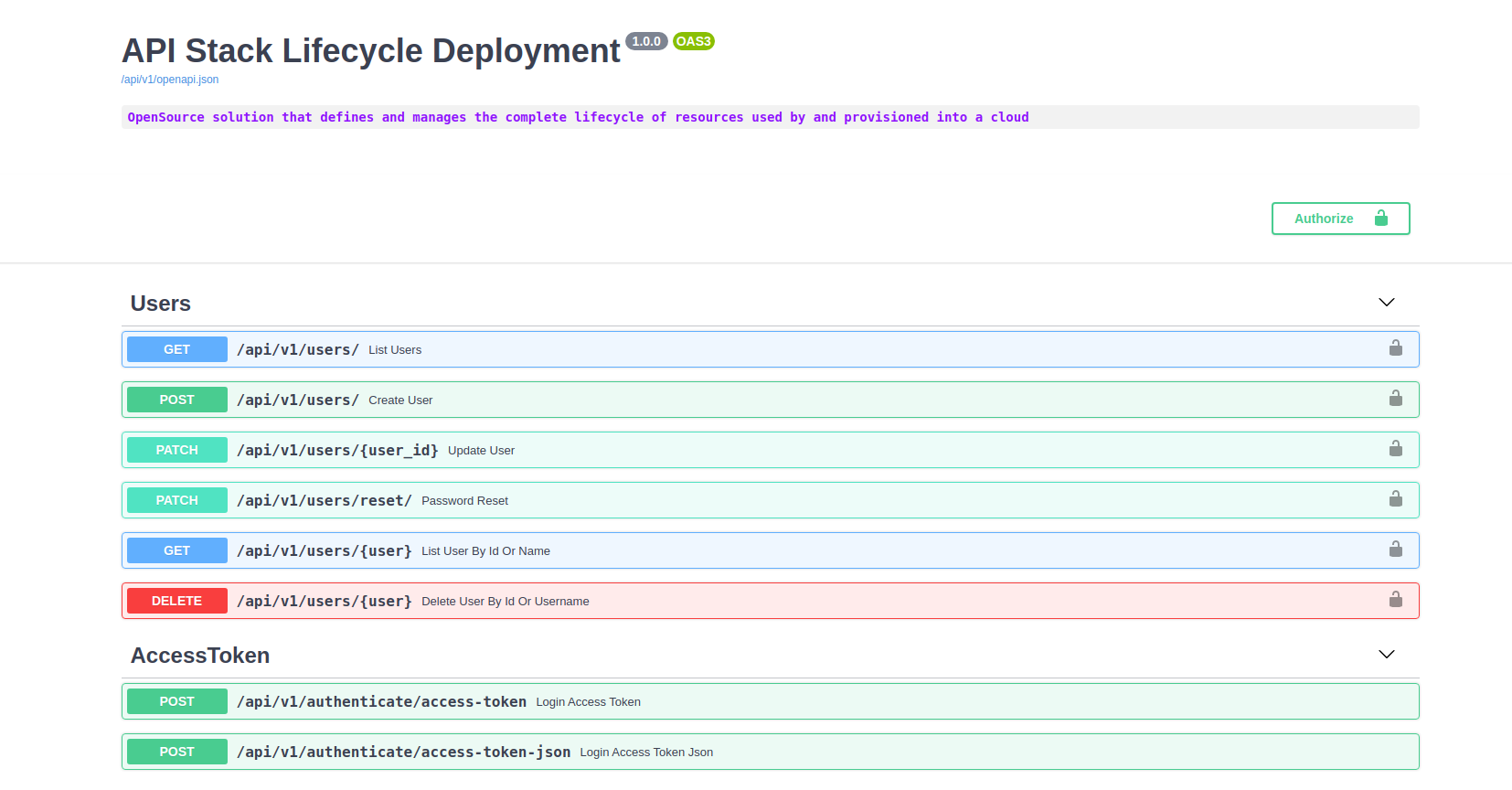
單擊儀表板鏈接:
添加雲帳戶
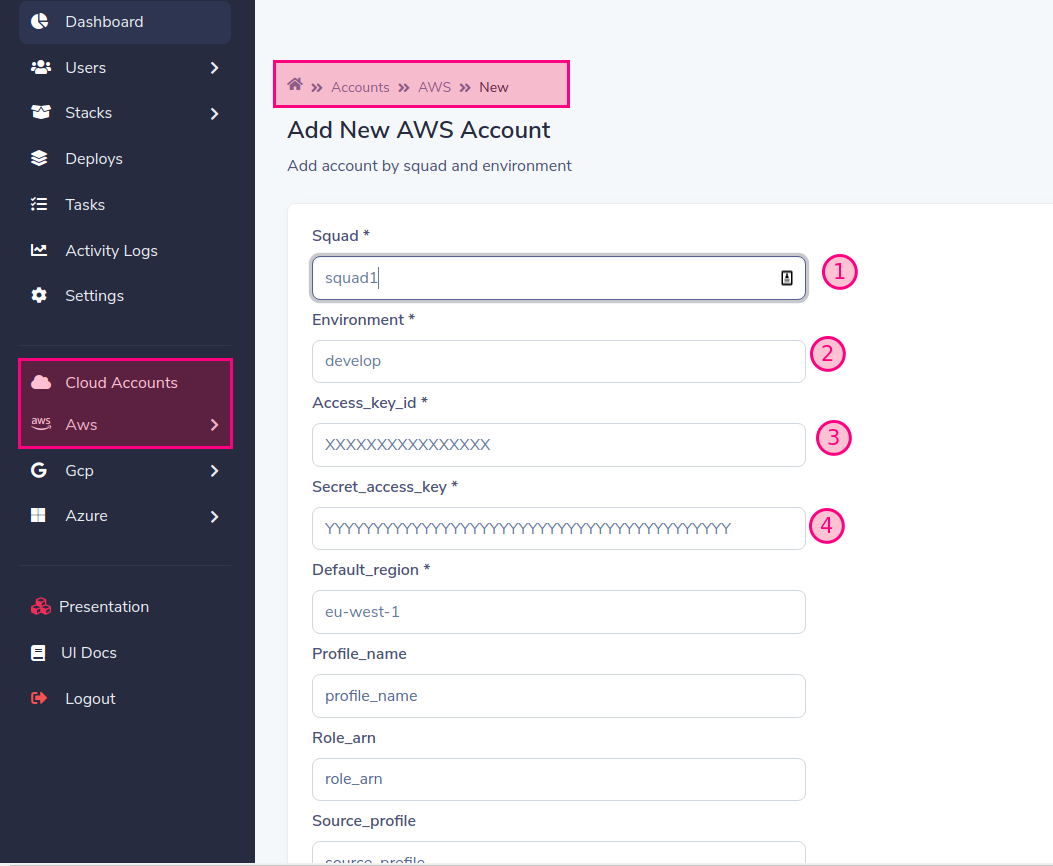
用所需的數據填寫表格。在我們的示例中,我們將使用
默認情況下,工人以squad1和squad2的身份運行,但您可以在需要時更改它並擴展
當您將帳戶添加到提供商(AWS,GCP,Azure)創建一個小隊時,必須為創建的小隊的名稱創建一個工人,如果您不這樣做
最後添加:
添加Terraform模塊或堆棧
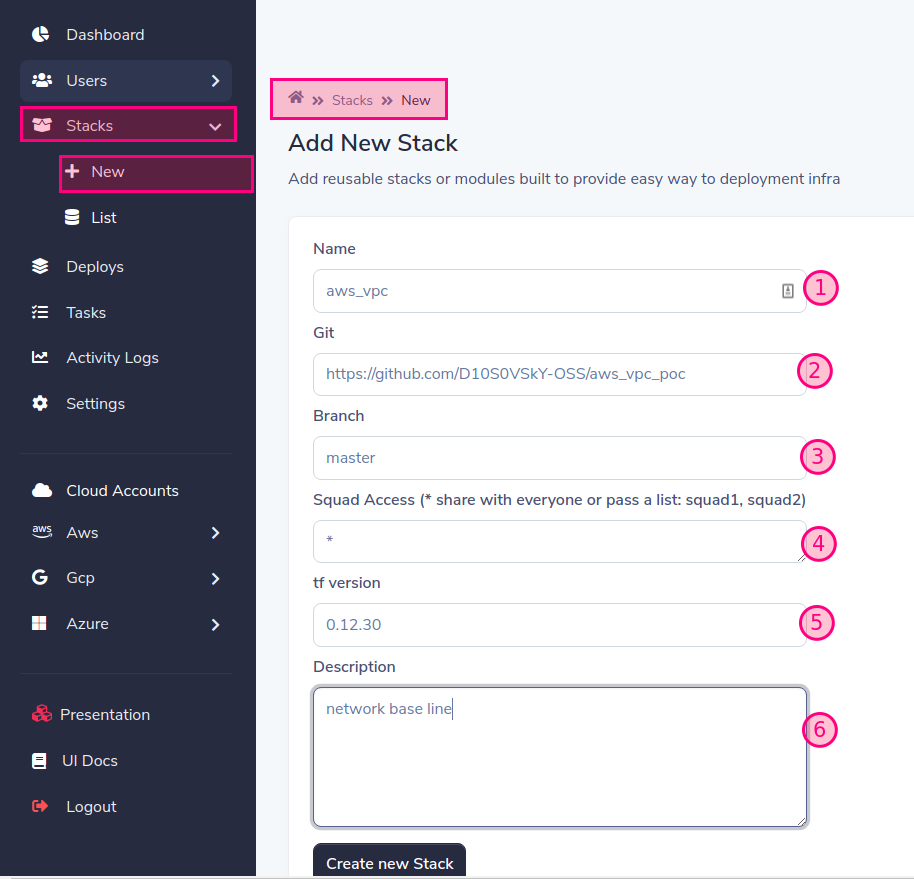
支持的前綴:aws_,gcp_,azure_
您可以將用戶和密碼作為https:// username:[email protected]/aws_vpc for ssh,您可以將其作為部署的秘密傳遞給用戶SLD
'*'=給予所有人,您可以允許訪問一個或多個由逗號分隔的小隊:squead1,squead2
https://releases.hashicorp.com/terraform/
部署您的第一個堆棧! ! !
列出用於部署的堆棧
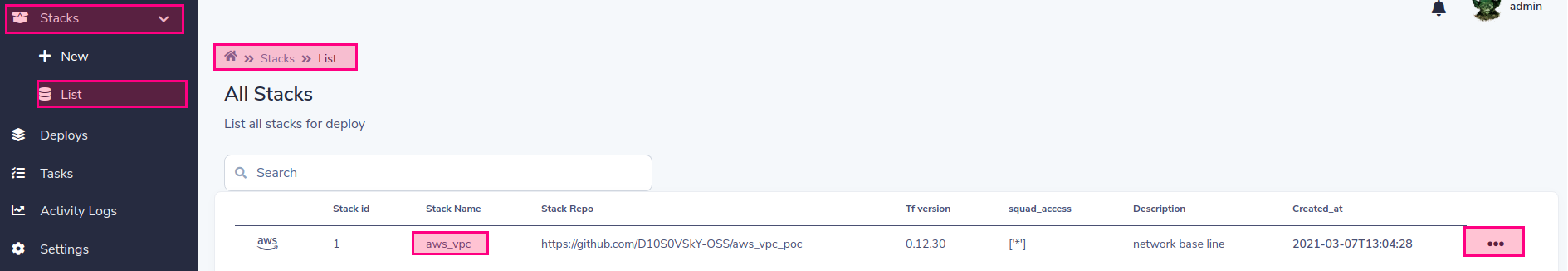
選擇部署
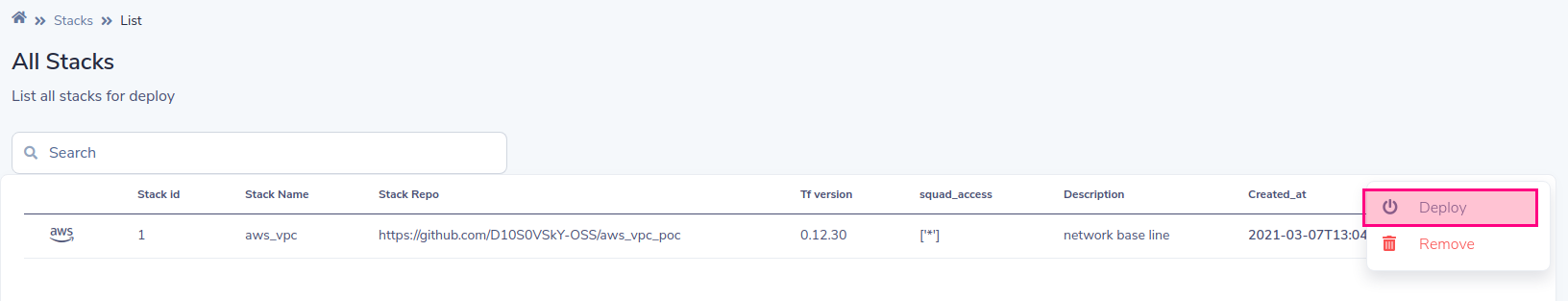
SLD將基於堆棧變量生成動態表單,填寫表單,然後按部署按鈕
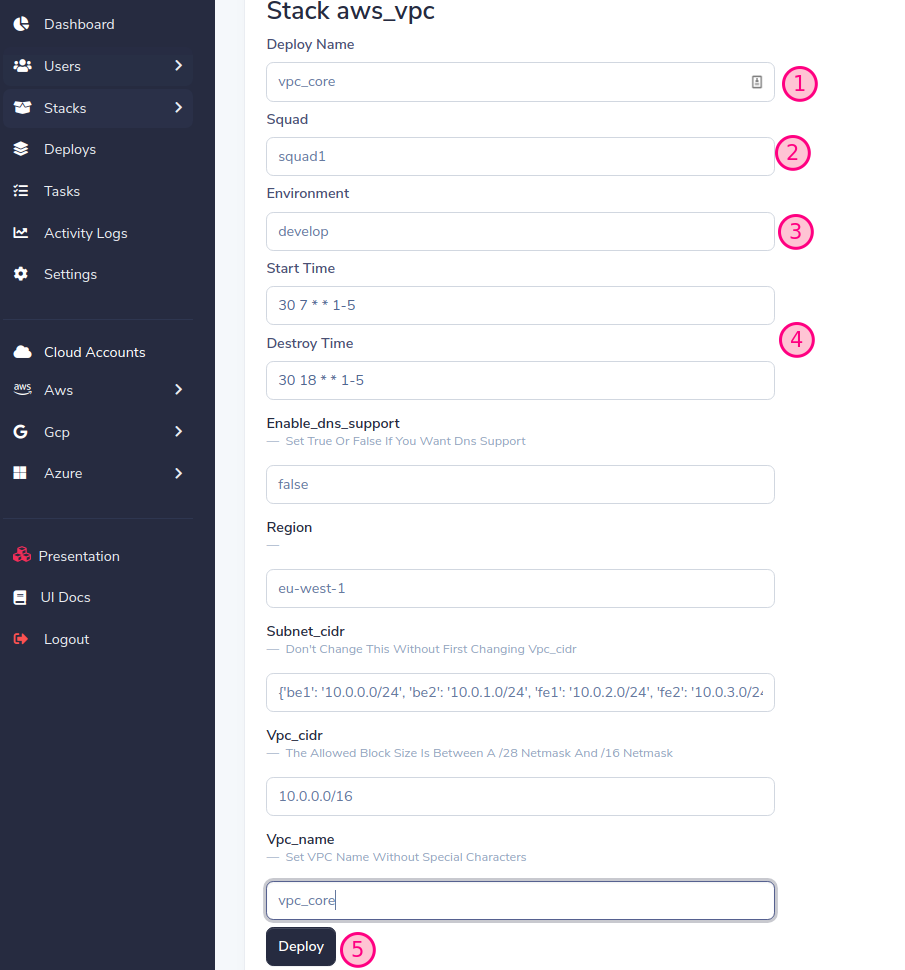
重要的!分配我們在添加帳戶時先前創建的相同的小隊和環境(請參閱添加雲帳戶)
現在,隨著部署的進行,任務的狀態將發生變化。
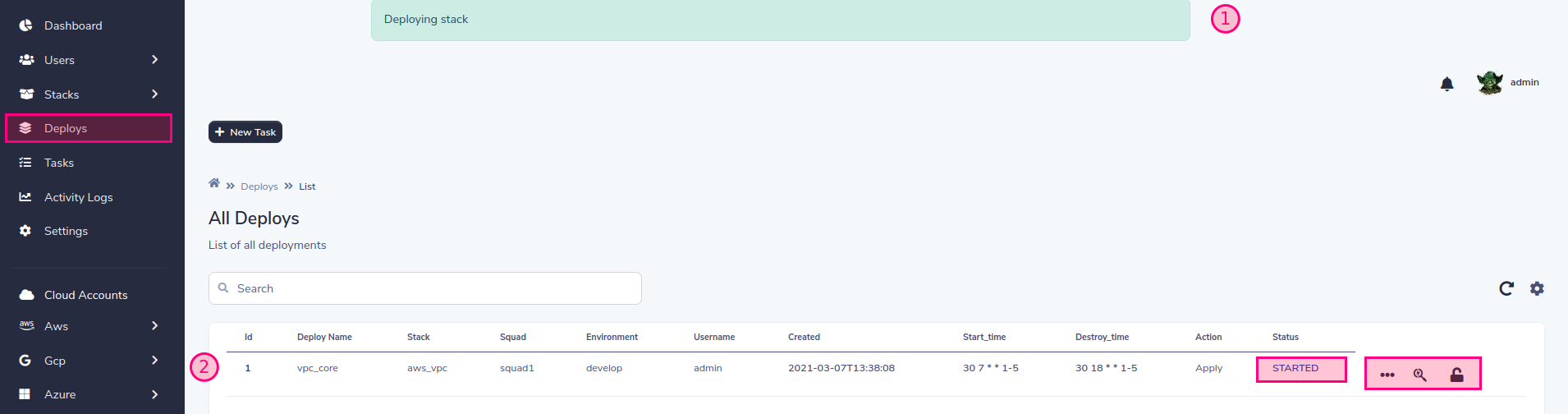
您可以控制實施生命週期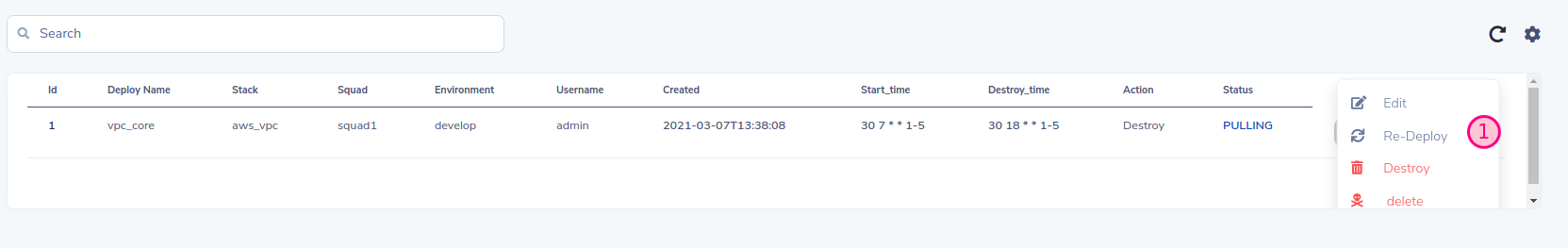 您可以銷毀,重新實現SLD會保留舊值,也可以隨意編輯這些值。
您可以銷毀,重新實現SLD會保留舊值,也可以隨意編輯這些值。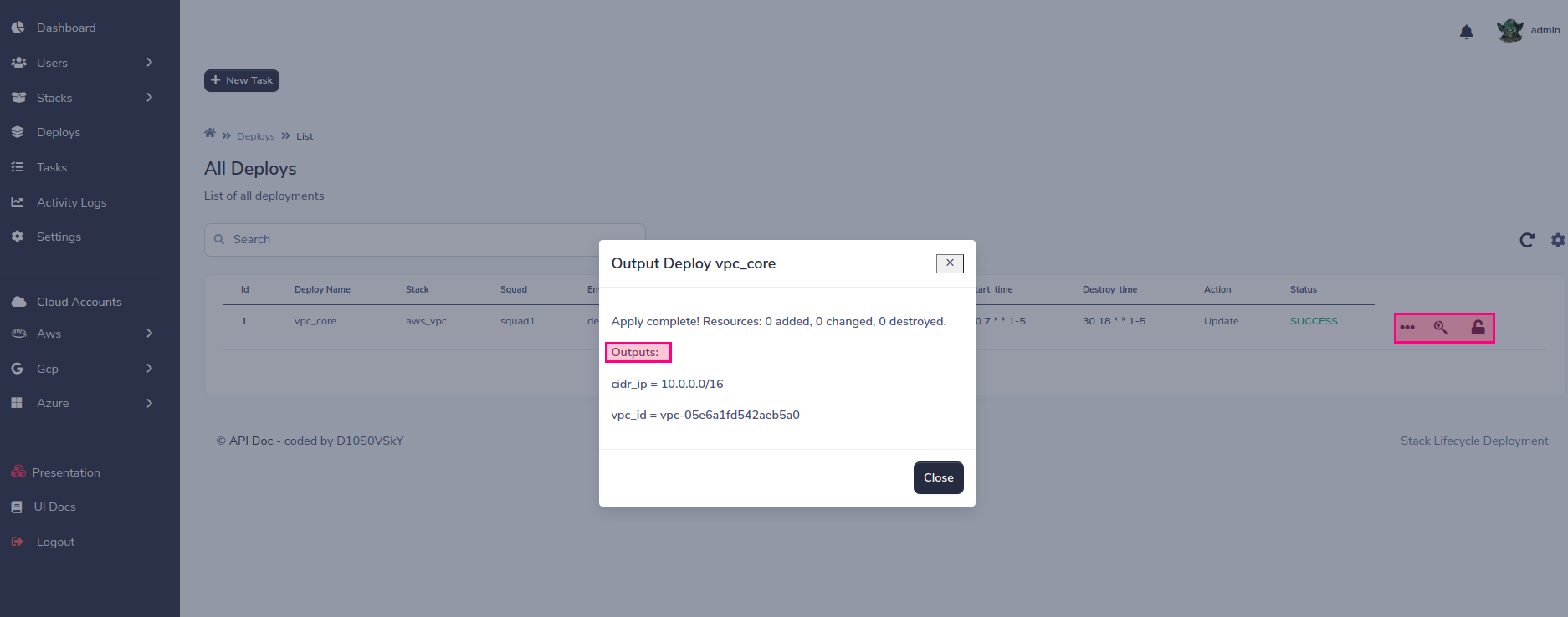 最後,您可以通過編程方式管理生命週期,處理基礎架構的破壞 /創建,這是儲蓄計劃的好實踐! ! !
最後,您可以通過編程方式管理生命週期,處理基礎架構的破壞 /創建,這是儲蓄計劃的好實踐! ! ! 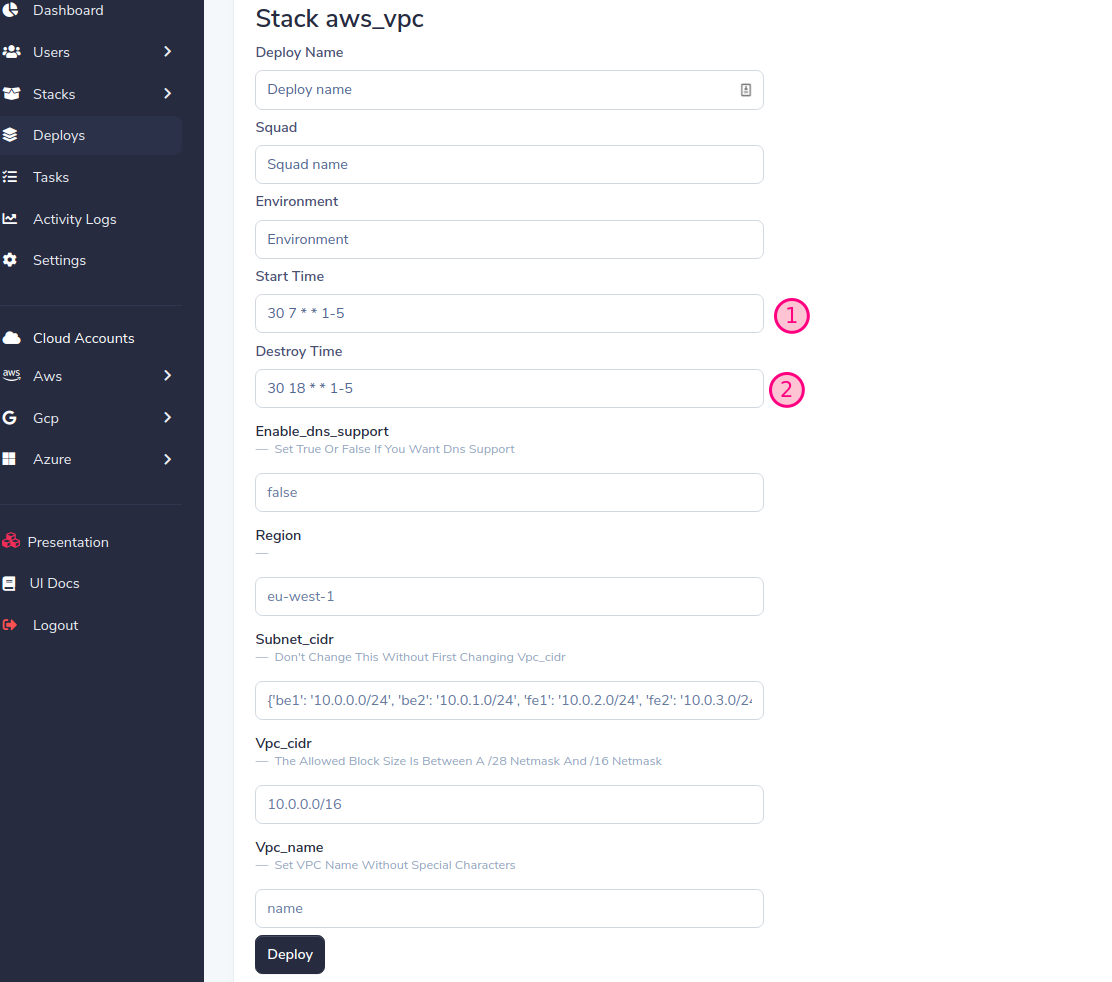
SLD使用自己的遠程後端,因此您無需在Terraform中配置任何後端。以下示例顯示了後端配置
terraform {
backend "http" {
address = "http://remote-state:8080/terraform_state/aws_vpc-squad1-develop-vpc_core"
lock_address = "http://remote-state:8080/terraform_lock/aws_vpc-squad1-develop-vpc_core"
lock_method = "PUT"
unlock_address = "http://remote-state:8080/terraform_lock/aws_vpc-squad1-develop-vpc_core"
unlock_method = "DELETE"
}
}
目前,SLD支持MongoDB,S3和本地後端(僅用於測試目的)將MongoDB配置為後端,您必須將以下變量作為參數傳遞給遙控狀態服務:
# docker-compose.yaml
environment:
SLD_STORE: mongodb
SLD_MONGODB_URL: "mongodb:27017/"
MONGODB_USER: admin
MONGODB_PASSWD: admin
# k8s yaml
env:
- name: SLD_STORE
value: mongodb
- name: SLD_MONGODB_URL
value: "mongodb:27017/"
- name: MONGODB_USER
value: admin
- name: MONGODB_PASSWD
value: admin
要配置S3,您可以通過AWS的訪問和秘密鍵,如果SLD在AWS中運行,建議使用角色
env:
- name: SLD_STORE
value: "S3"
- name: SLD_BUCKET
value: "s3-sld-backend-cloud-tf-state"
- name: AWS_ACCESS_KEY
value: ""
- name: AWS_SECRET_ACCESS_KEY
value: ""
對於Azure Env,您需要設置下一個Env
env:
- name: SLD_STORE
value: azure
- name: AZURE_STORAGE_CONNECTION_STRING
value: "DefaultEndpointsProtocol=https;AccountName=<YOUR ACCOUNT>;AccountKey=<YOUR ACCESS KEY>;EndpointSuffix=core.windows.net"
請參閱Azure-Storage-Configure-Connection-string
對於Google雲存儲集:
SLD_STORE=gcp
export GOOGLE_APPLICATION_CREDENTIALS="/app/sld-gcp-credentials.json"
導入Google服務帳戶密鑰到K8S Secret
kubectl create secret generic gcp-storage --from-file=~/Downloads/storage.json
修改sld-remote-state.yml設置GCP存儲雲後端和安裝秘密:
apiVersion: apps/v1
kind: Deployment
metadata:
name: remote-state
labels:
name: remote-state
spec:
replicas: 1
selector:
matchLabels:
name: remote-state
template:
metadata:
labels:
name: remote-state
spec:
subdomain: primary
containers:
- name: remote-state
image: d10s0vsky/sld-remote-state:latest
volumeMounts:
- name: gcp
mountPath: "/app/gcp"
readOnly: true
env:
- name: SLD_STORE
value: gcp
- name: GOOGLE_APPLICATION_CREDENTIALS
value: "/app/gcp/storage.json"
resources:
limits:
memory: 600Mi
cpu: 1
requests:
memory: 300Mi
cpu: 500m
imagePullPolicy: Always
command: ["python3", "-m", "uvicorn", "main:app", "--host", "0.0.0.0", "--port", "8080", "--workers", "1"]
ports:
- containerPort: 8080
livenessProbe:
httpGet:
path: /
port: 8080
httpHeaders:
- name: status
value: healthy
initialDelaySeconds: 60
periodSeconds: 60
volumes:
- name: gcp
secret:
secretName: gcp-storage
為了能夠使用其他堆棧的輸出,您可以按照以下方式進行配置,如下所示,alwwys與“任務名稱”相同
| 堆棧名稱 | 小隊帳戶 | env | 部署名稱 |
|---|---|---|---|
| AWS_VPC | squead1 | 發展 | VPC_CORE |
data "terraform_remote_state" "vpc_core" {
backend = "http"
config = {
address = "http://remote-state:8080/terraform_state/aws_vpc-squad1-develop-vpc_core"
}
}
測試示例:
echo "data.terraform_remote_state.vpc_core.outputs"|terraform console
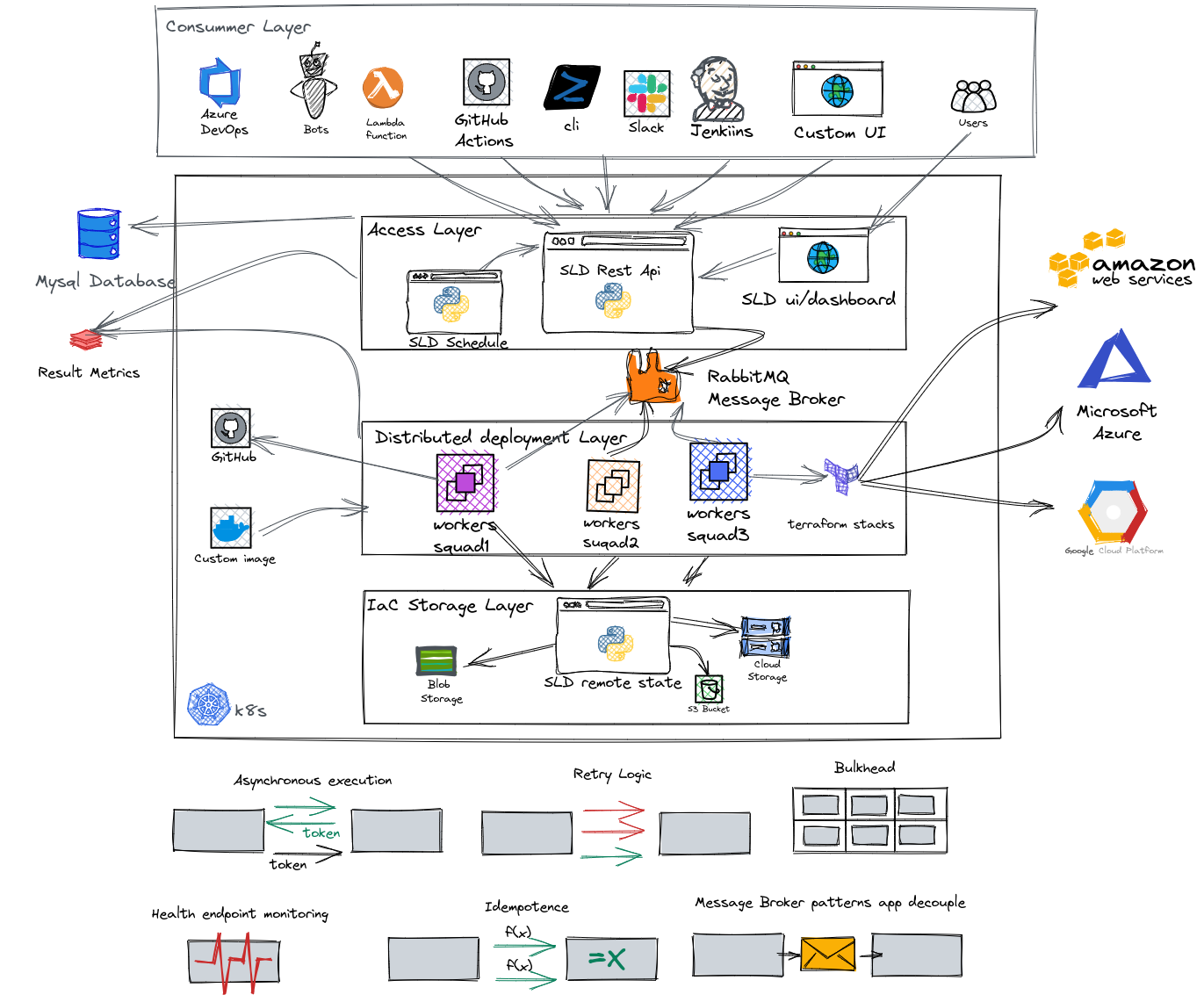
SLD的工人負責執行基礎架構部署。您可以同時為每個帳戶或幾個帳戶使用一個或多個工人。這完全取決於您考慮的並行性和隔離程度
# Example k8s worker for account squad1, change this for each of your accounts
# Stack-Lifecycle-Deployment/play-with-sld/kubernetes/k8s/sld-worker-squad1.yml
# Add replicas for increment paralelism
# Add more squad accounts if you want to group accounts in the same worker:
# command: ["celery", "--app", "tasks.celery_worker", "worker", "--loglevel=info", "-c", "1", "-E", "-Q", "squad1,"another_squad_account"]
apiVersion: apps/v1
kind: Deployment
metadata:
name: stack-deploy-worker-squad1
labels:
name: stack-deploy-worker-squad1
spec:
replicas: 1
selector:
matchLabels:
name: stack-deploy-worker-squad1
template:
metadata:
labels:
name: stack-deploy-worker-squad1
spec:
subdomain: primary
containers:
- name: stack-deploy-worker-squad1
image: d10s0vsky/sld-api:latest
imagePullPolicy: Always
env:
- name: TF_WARN_OUTPUT_ERRORS
value: "1"
resources:
limits:
memory: 600Mi
cpu: 1
requests:
memory: 300Mi
cpu: 500m
command: ["celery", "--app", "tasks.celery_worker", "worker", "--loglevel=info", "-c", "1", "-E", "-Q", "squad1"]
# Example docker-compose worker for account squad1, change this for each of your accounts
# Stack-Lifecycle-Deployment/play-with-sld/docker/docker-compose.yml
worker:
image: d10s0vsky/sld-api:latest
entrypoint: ["celery", "--app", "tasks.celery_worker", "worker", "--loglevel=info", "-c", "1", "-E", "-Q", "squad1"]
environment:
BROKER_USER: admin
BROKER_PASSWD: admin
depends_on:
- rabbit
- redis
- db
- remote-state
SLD具有三個預先配置的角色,以便用戶輕鬆管理它。
| 角色 | 範圍 | 描述 |
|---|---|---|
| 尤達 | 全球的 | 全球範圍,可以看到所有小隊,並且是完整的管理員 |
| darth_vader | 一個或多個小隊 | 限制小隊的範圍,可以看到分配的小隊,而您是這些小隊的完整經理 |
| 突擊隊員 | 一個或多個小隊 | 極限小隊範圍,可以看到分配的小隊,並且只能部署分配的部署 |
| R2-D2 | 全部,一個或多個小隊 | 此角色僅用於識別,必須與以前的角色相關聯,其用例是針對訪問API的機器人用戶 |
貢獻使開源社區成為一個令人驚嘆的學習,啟發和創造的地方。您所做的任何貢獻都非常感謝。
git checkout -b feature/AmazingFeature )git commit -m 'Add some AmazingFeature' )git push origin feature/AmazingFeature )根據MIT許可分發。有關更多信息,請參見LICENSE 。
堆棧生命週期部署