HexraysToolbox
1.0.0
Hexrays Toolbox(HXTB)是一组强大的IDAPYTHON脚本,可用于在二进制文件中查找和定位代码模式,独立于其基础处理器体系结构。
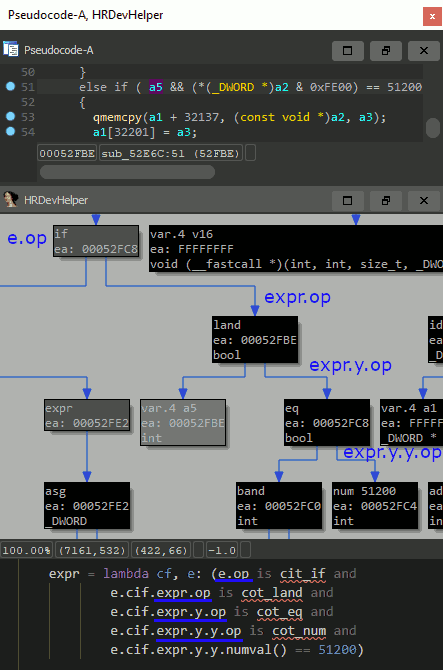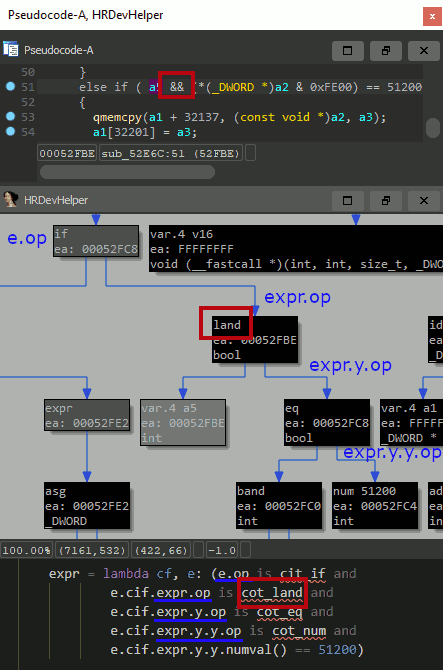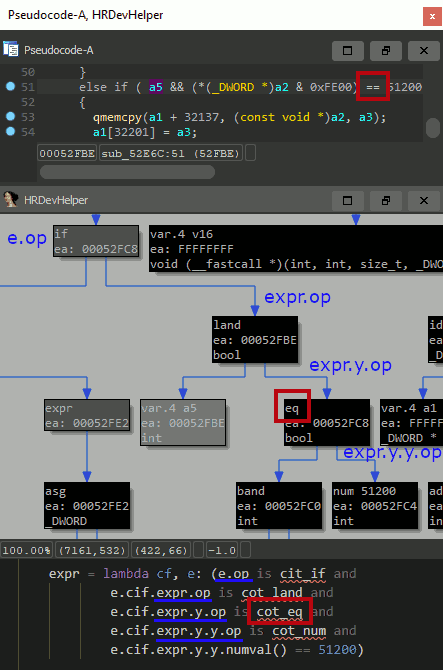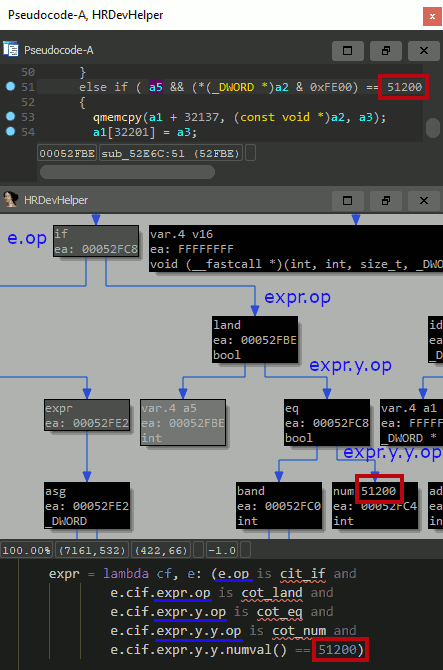
以下动画说明的查询是一个示例,说明了如何使用十字级工具箱来影响Android的WhatsApp(CVE-2019-3568,Libwhatsapp.so)的漏洞。这是通过使用IDAPYTHON LAMBDA函数定位的所需代码模式来完成的。找到示例脚本 。
。
每个目标体系结构需要有效的IDA许可证和有效的十六进制分解器许可证。
使用十六进制工具箱有几种方法,每个工具箱都具有不同程度的灵活性。
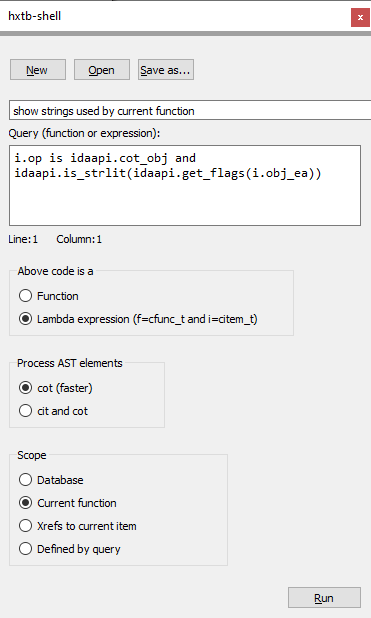
interactive.py ,一个添加便利函数以与IDA命令行接口一起使用的脚本automation.py ,一个在批处理模式下在给定的文件集上处理和运行HXTB查询的脚本从IDA中执行随附的hxtb_shell.py脚本,打开了一个可用于开发,加载和运行HXTB查询的GUI窗口。下面的屏幕截图显示了加载HXTB壳的查询的样子。
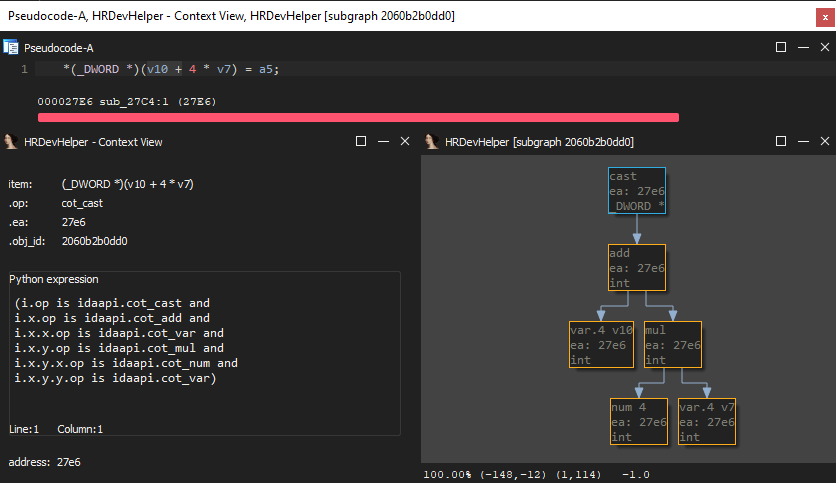
HXTB-Shell还接受HRDEVHELPER插件的上下文查看器创建的Python表达式。它们可以从中复制并直接粘贴到HXTB-Shell GUI中。
可以在HEXRAYS工具箱中包含的hxtbshell_queries子折中找到可以加载HXTB-Shell的其他示例查询。
使用IDA(ALT-F7)加载hxtb.py可以使IDAPYTHON CLI和脚本解释器(Shift-F2)均可提供诸如find_expr()和find_item()之类的功能。除其他外,这些功能可用于在当前加载的IDA数据库上运行查询。请查看下面显示的一些示例。
find_item(ea, q)
find_expr(ea, q)
Positional arguments:
ea: address of a valid function within
the current database
q: lambda function
custom lambda function with the following arguments:
1. cfunc: cfunc_t
2. i/e: cinsn_t/cexpr_t
Returns:
list of query_result_t objects
Example:
find_expr(here(), lambda cf, e: e.op is cot_call)
-> finds and returns all function calls within a current function.
The returned data is a list of query_result_t objects (see hxtb.py).
The returned list can be passed to an instance of the ic_t class,
which causes the data to be displayed by a chooser as follows:
from idaapi import *
import hxtb
hxtb.ic_t(find_expr(here(), lambda cf,e:e.op is cot_call))
Please find the cfunc_t, citem_t, cinsn_t and cexpr_t structures
within hexrays.hpp for further help and details.
cot_eq
/
x / y
(anything) cot_num --- n.numval() == 0
from idaapi import *
from hxtb import find_expr
query = lambda cfunc , e : e . op is cot_eq and e . y . op is cot_num and e . y . numval () == 0
r = find_expr ( here (), query )
for e in r :
print ( e ) cot_call
/
x /
cot_obj
from idaapi import *
from hxtb import find_expr
query = lambda cfunc , e : e . op is cot_call and e . x . op is cot_obj
r = find_expr ( here (), query )
for e in r :
print ( e )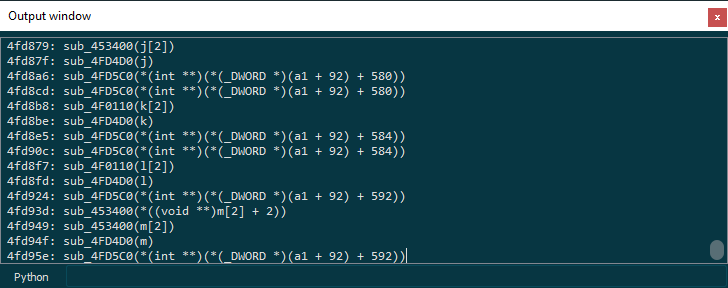
cot_call --- arg1 is cot_var
/ arg1 is on stack
x /
cot_obj --- name(obj_ea) == 'memcpy'
from idaapi import *
from hxtb import find_expr
r = []
query = lambda cfunc , e : ( e . op is cot_call and
e . x . op is cot_obj and
get_name ( e . x . obj_ea ) == 'memcpy' and
len ( e . a ) == 3 and
e . a [ 0 ]. op is cot_var and
cfunc . lvars [ e . a [ 0 ]. v . idx ]. is_stk_var ())
for ea in Functions ():
r += find_expr ( ea , query )
for e in r :
print ( e ) cot_call --- arg2 ('fmt') contains '%s'
/
x /
cot_obj --- name(obj_ea) == 'sprintf'
from idaapi import *
from hxtb import find_expr
r = []
query = lambda cfunc , e : ( e . op is cot_call and
e . x . op is cot_obj and
get_name ( e . x . obj_ea ) == 'sprintf' and
len ( e . a ) >= 2 and
e . a [ 1 ]. op is cot_obj and
is_strlit ( get_flags ( get_item_head ( e . a [ 1 ]. obj_ea ))) and
b'%s' in get_strlit_contents ( e . a [ 1 ]. obj_ea , - 1 , 0 , STRCONV_ESCAPE ))
for ea in Functions ():
r += find_expr ( ea , query )
for e in r :
print ( e ) from idaapi import *
from hxtb import ic_t
query = lambda cfunc , e : ( e . op in
[ cot_asgsshr , cot_asgsdiv ,
cot_asgsmod , cot_sge ,
cot_sle , cot_sgt ,
cot_slt , cot_sshr ,
cot_sdiv , cot_smod ])
ic_t ( query )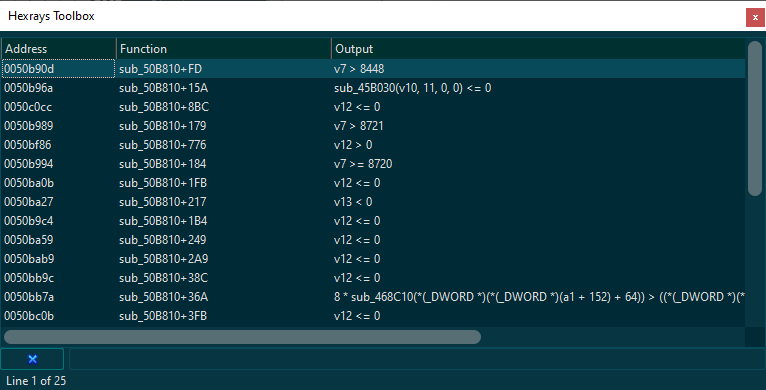
from idaapi import *
from hxtb import ic_t
ic_t ( lambda cf , i : i . op is cit_if )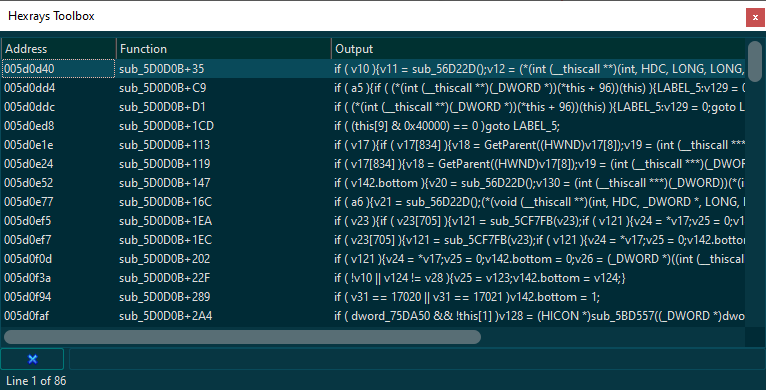
from idaapi import *
from hxtb import ic_t , query_db
ic_t ( query_db ( lambda cf , i : is_loop ( i . op )))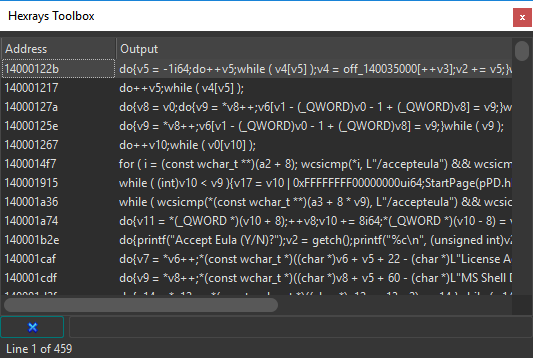
from hxtb import ic_t , query_db , find_child_expr
from ida_hexrays import *
find_copy_query = lambda cfunc , i : ( i . op is cot_asg and
i . x . op is cot_ptr and
i . y . op is cot_ptr )
find_loop_query = lambda cfunc , i : ( is_loop ( i . op ) and
find_child_expr ( cfunc , i , find_copy_query ))
ic_t ( query_db ( find_loop_query ))