
在博客上了解更多信息: https://swarm.ptsecurity.com/fork-bomb-for-flutter/
该框架有助于使用flutter库的修补版本进行反向工程,该版本已经编译并准备好进行应用重新包装。该库的快照供应过程已修改,以便您以方便的方式执行动态分析。
关键功能:
socket.cc已修补以进行流量监视和拦截;dart.cc已修改为打印类,功能和某些字段;Dockerfile支持手动弹奏代码更改 # Linux, Windows, MacOS
pip3 install reflutter==0.8.0
impact@f:~ $ reflutter main.apk
Please enter your Burp Suite IP: <input_ip>
SnapshotHash: 8ee4ef7a67df9845fba331734198a953
The resulting apk file: ./release.RE.apk
Please sign the apk file
Configure Burp Suite proxy server to listen on *:8083
Proxy Tab -> Options -> Proxy Listeners -> Edit -> Binding Tab
Then enable invisible proxying in Request Handling Tab
Support Invisible Proxying -> true
impact@f:~ $ reflutter main.ipa您需要指定位于带有Flutter应用程序设备的同一网络中的Burp Suite代理服务器的IP。接下来,您应该在BurpSuite -> Listener Proxy -> Options tab中配置代理
8083All interfacesTrue 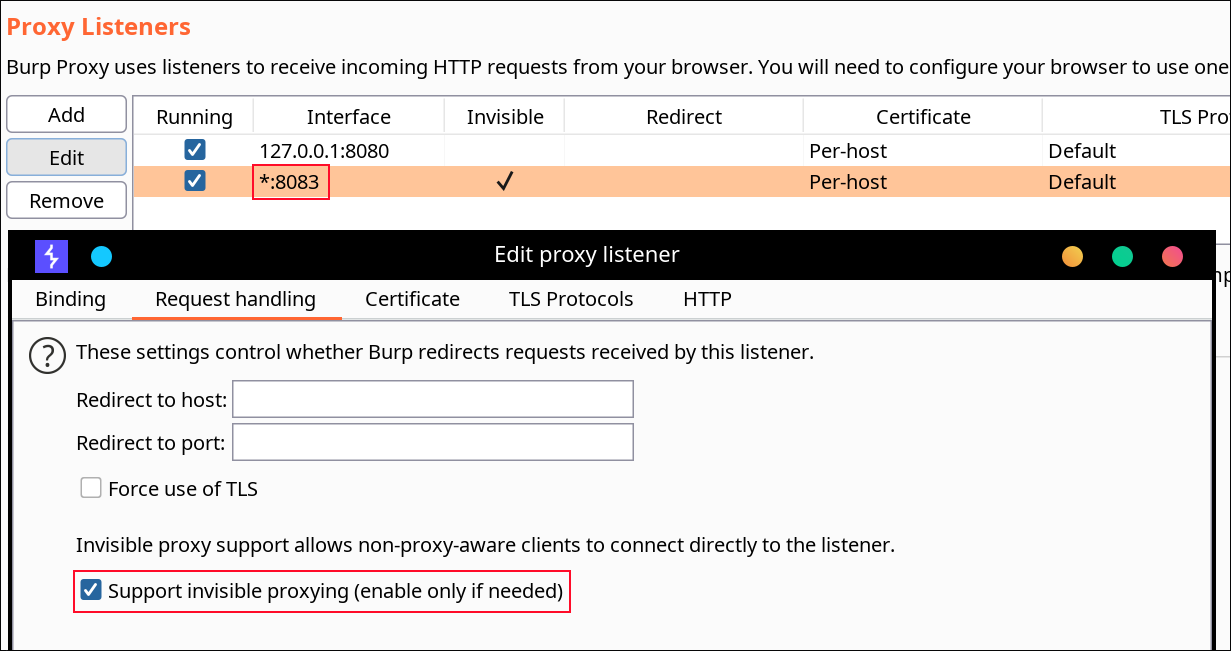
您无需安装任何证书。在Android设备上,您也不需要root访问。回流还允许绕过一些扑朔迷离的证书固定实现。
结果APK必须对齐并签名。我使用Uber-apk-Signer java -jar uber-apk-signer.jar --allowResign -a release.RE.apk 。要查看通过DARTVM加载哪个代码,您需要在设备上运行该应用程序。请注意,您必须手动查找_kDartIsolateSnapshotInstructions (例如0xB000)等于使用二进制搜索的内容。回流将转储写入应用程序的根文件夹,并将777权限设置为文件和文件夹。您可以使用ADB命令提取文件
impact@f:~ $ adb -d shell " cat /data/data/<PACKAGE_NAME>/dump.dart " > dump.dart Library : 'package:anyapp/navigation/DeepLinkImpl.dart' Class : Navigation extends Object {
String * DeepUrl = anyapp : //evil.com/ ;
Function 'Navigation.' : constructor. ( dynamic , dynamic , dynamic , dynamic ) => NavigationInteractor {
Code Offset : _kDartIsolateSnapshotInstructions + 0x0000000000009270
}
Function 'initDeepLinkHandle' : . ( dynamic ) => Future < void > * {
Code Offset : _kDartIsolateSnapshotInstructions + 0x0000000000412fe8
}
Function '_navigateDeepLink@547106886' : . ( dynamic , dynamic , { dynamic navigator}) => void {
Code Offset : _kDartIsolateSnapshotInstructions + 0x0000000000002638
}
}
Library : 'package:anyapp/auth/navigation/AuthAccount.dart' Class : AuthAccount extends Account {
PlainNotificationToken * _instance = sentinel;
Function 'getAuthToken' : . ( dynamic , dynamic , dynamic , dynamic ) => Future < AccessToken *> * {
Code Offset : _kDartIsolateSnapshotInstructions + 0x00000000003ee548
}
Function 'checkEmail' : . ( dynamic , dynamic ) => Future < bool *> * {
Code Offset : _kDartIsolateSnapshotInstructions + 0x0000000000448a08
}
Function 'validateRestoreCode' : . ( dynamic , dynamic , dynamic ) => Future < bool *> * {
Code Offset : _kDartIsolateSnapshotInstructions + 0x0000000000412c34
}
Function 'sendSmsRestorePassword' : . ( dynamic , dynamic ) => Future < bool *> * {
Code Offset : _kDartIsolateSnapshotInstructions + 0x00000000003efb88
}
}使用在reflutter main.ipa命令执行后创建的IPA文件。要查看通过DARTVM加载哪个代码,您需要在设备上运行该应用程序。回流将使用回流标签登录到Xcode Console logs Current working dir: /private/var/mobile/Containers/Data/Application/<UUID>/dump.dart接下来,您需要从设备中拉出文件,
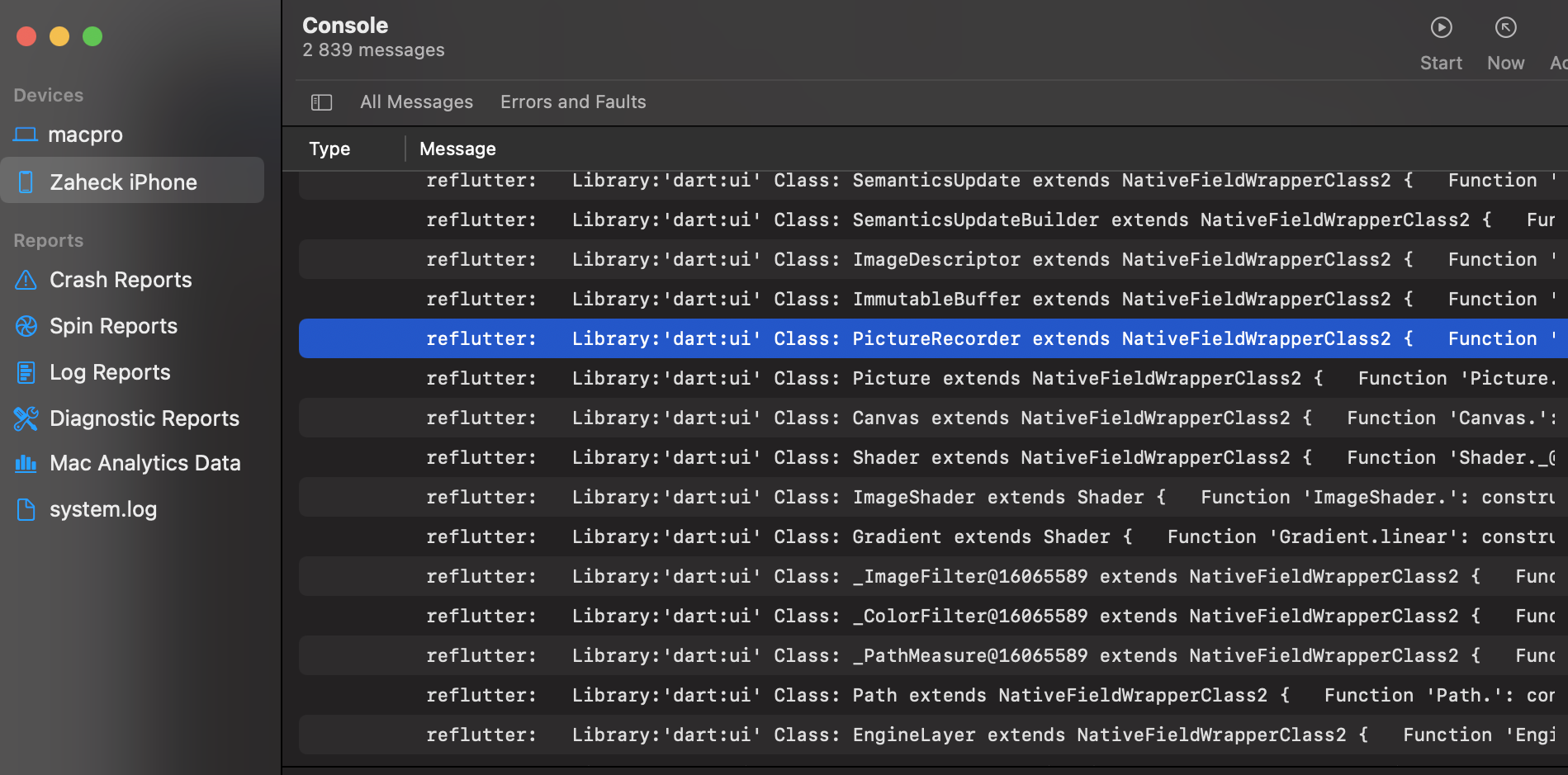
垃圾场的结果偏移可用于Frida脚本
frida -U -f <package> -l frida.js
Value获得_kDartIsolateSnapshotInstructions readelf -Ws libapp.so值
App.framework和libapp.so内部邮政编码的检测这些发动机是使用GitHub操作中的回流构建的,以构建所需的版本,提交和快照哈希在此表中使用。快照的哈希人是从storage.googleapis.com/flutter_infra_release/flutter/<hash>/android-arm64-release/linux-x64.zip提取的。
如果您想实现自己的补丁,则使用专门精心设计的Docker支持手动弹奏代码更改
git clone https://github.com/Impact-I/reFlutter && cd reFlutter
docker build -t reflutter -f Dockerfile .构建命令:
docker run -it -v " $( pwd ) :/t " -e HASH_PATCH= < Snapshot_Hash > -e COMMIT= < Engine_commit > reflutter例子:
docker run -it -v " $( pwd ) :/t " -e HASH_PATCH=aa64af18e7d086041ac127cc4bc50c5e -e COMMIT=d44b5a94c976fbb65815374f61ab5392a220b084 reflutter示例构建Android Arm64:
docker run -e WAIT=300 -e x64=0 -e arm=0 -e HASH_PATCH= < Snapshot_Hash > -e COMMIT= < Engine_commit > --rm -iv ${PWD} :/t reflutter标志:
-e x64 = 0 <禁用X64体系结构的构建,用于减少构建时间>
-e ARM64 = 0 <禁用用于ARM64建筑的建筑物,用于减少建筑时间>
-e ARM = 0 <禁用用于ARM32架构的建筑物,用于减少建筑时间>
-e等待= 300
-e hash_patch = [snapshot_hash]
-e commits = [Engine_commit] <在此处指定引擎版本的提交,从Enginhash.csv表或Flutter/Engine Repo>