I create makin to make initial malware assessment little bit easier for me, I think it's useful for others as well, It helps to reveal a debugger detection techniques used by a sample.
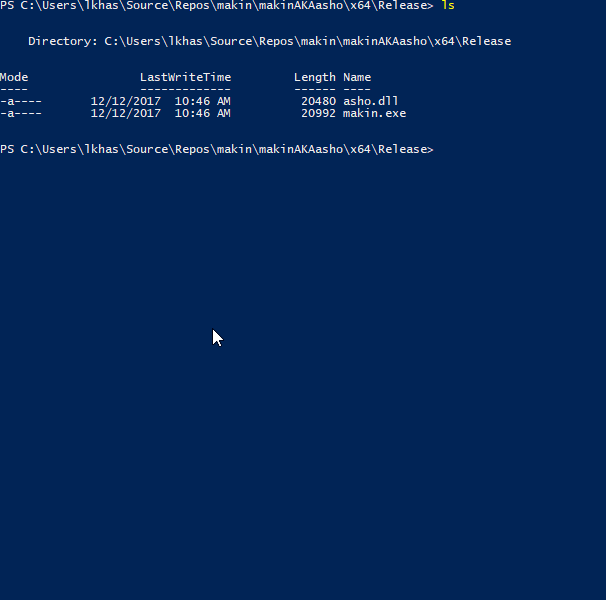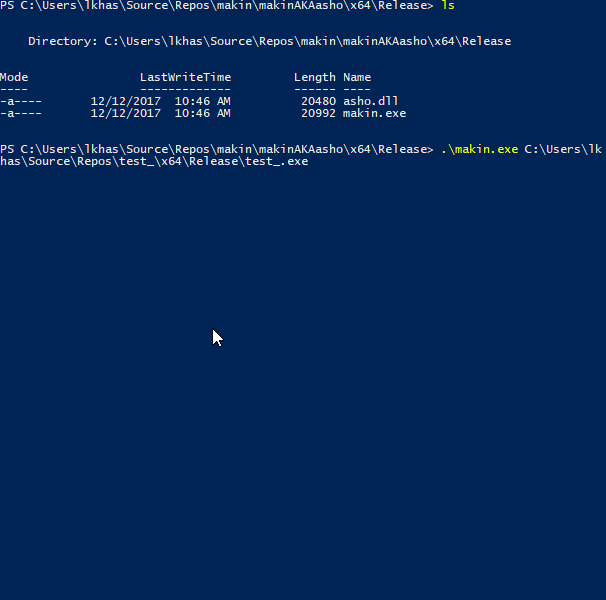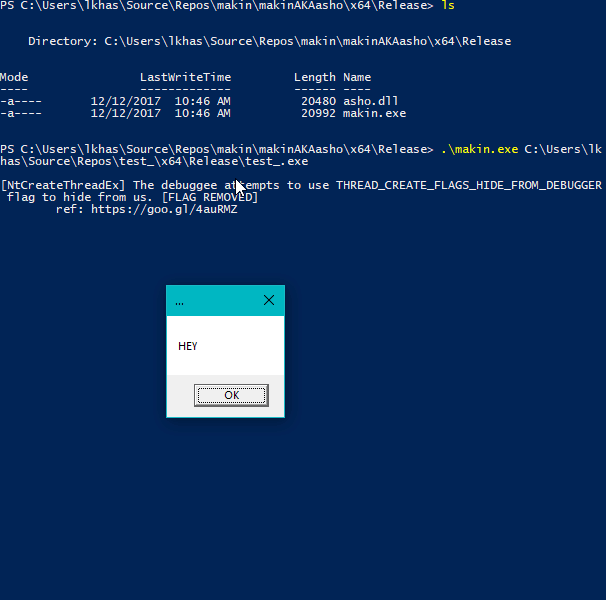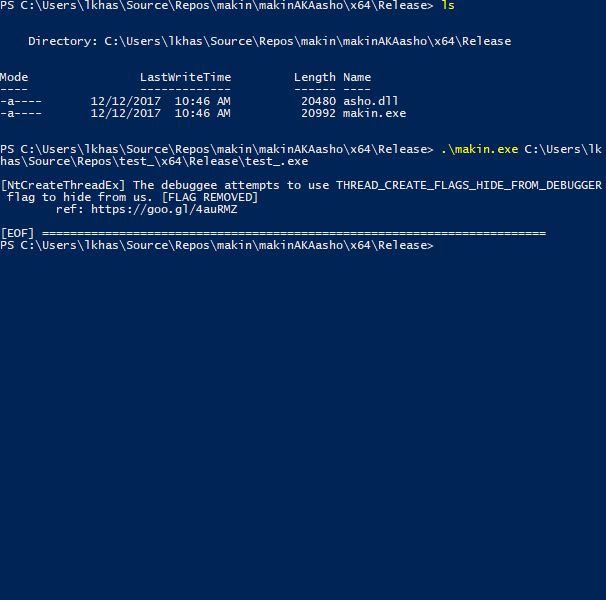
makin opens a sample as a debuggee and injects asho.dll(main module renames all dlls before injection), asho.dll hooks several functions at ntdll.dll and kernelbase.dll libraries and after parameters checkings, it sends the corresponding message to the debugger (makin.exe).
makin also generates a script for IDA Pro to set breakpoints at detected APIs.
At this moment, makin can reveal following techniques:
ntdll.dll:
NtClose - ref: The "Ultimate" Anti-Debugging Reference: 7.B.iiNtOpenProcess - ref: The "Ultimate" Anti-Debugging Reference: 7.B.iNtCreateFile - ref: The "Ultimate" Anti-Debugging Reference: 7.B.iii (Open itself)NtCreateFile - ref: The "Ultimate" Anti-Debugging Reference: 7.B.iii (Open a driver)LdrLoadDll - ref: The "Ultimate" Anti-Debugging Reference: 7.B.ivNtSetDebugFilterState - ref: The "Ultimate" Anti-Debugging Reference: 7.D.viNtQueryInformationProcess - ref: The "Ultimate" Anti-Debugging Reference: 7.D.viii.a, 7.D.viii.b, 7.D.viii.cNtQuerySystemInformation - ref: The "Ultimate" Anti-Debugging Reference: 7.E.iiiNtSetInformationThread - ref: The "Ultimate" Anti-Debugging Reference 7.F.iiiNtCreateUserProcess - ref: The "Ultimate" Anti-Debugging Reference 7.G.iNtCreateThreadEx - ref: ntuery blog postNtSystemDebugControl - ref: @waleedassar - pastebinNtYieldExecution - ref: The "Ultimate" Anti-Debugging Reference 7.D.xiiiNtSetLdtEntries - ref: ANTI-UNPACKER TRICKS: PART ONE - 2.1.2NtQueryInformationThread - ref: ntquery - NtQueryInformationThreadNtCreateDebugObject and NtQueryObject - ref: Anti-Debug NtQueryObjectRtlAdjustPrivilege - ref: Using RtlAdjustPrivilege to detect debugger by insid3codeteamPEB->BeingDebugged - Instead of calling IsDebuggerPresent(), some programs manually check the PEB (Process Environment Block) for the BeingDebugged flag.PEB->NtGlobalFlag - ref: al-khaserUserSharedData->KdDebuggerEnabled - ref: al-khaser - SharedUserData_KernelDebuggerPROCTECTED handle trick - ref: al-khaser - HANDLE_FLAG_PROTECT_FROM_CLOSEkernelbase.dll:
IsDebuggerPresent - ref: MSDNCheckRemoteDebuggerPresent - ref: MSDNSetUnhandledExceptionFilter - ref: The "Ultimate" Anti-Debugging Reference: D.xvRegOpenKeyExInternalW - checks registry keysRegQueryValueExW - checks registry key valuesYou can add more VM checks via editing checks.json file, without modification of the executable
That's all for now, you can add as much as you wish :)