Update some papers that I have read during my study and feel good. For some papers with classic or novel ideas, I will read them carefully, and write some reading notes to upload and update them simultaneously. (The content is updated synchronously to Zhihu and CSDN), and the papers are discharged in chronological order .
Note:
In order to facilitate searching papers and archives, search tools are provided, and the usage is as follows:
python3 search_kits.py
Big Model • Clustering • Vector Recall • Dialogue System • Dialogue State Management • Machine Learning • Language Models
Datasets • Text similarity/match/categorization • Deep learning • Speech system • Speech recognition • Models
Pre-training • Subword • Task-based dialogue • Dialogue status tracking • Dialogue intent recognition • Dialogue slot filling
GNN • Retrieval dialogue system • Speech synthesis • Overview • Unsupervised • Data enhancement
Reading Comprehension Model • Interpretability • Prompt • Evaluation • Dialogue Strategy Learning • Relationship Extraction
Distillation • Anomaly Detection • Self-Supervised • Loss Function • Semi-Supervised • Community Discovery
Graph Algorithm • Search • Text Summary
注:论文按时间排序,并进行分类归档,可直接在本页Ctrl+F查询,或使用上述搜索工具查询(推荐)
下述列表项格式:<标签 | 论文 | 阅读笔记 | 简述 | 作者时间>
[Graph Algorithm-Search] | The PageRank Citation Ranking: Bringing Order to the Web | Reading Notes | The classic PageRank algorithm, originally used as a calculation method for Internet web pages, was used for Google search engine web page sorting. The core idea of this algorithm is to define a random walk model (first-order Markov chain) on a directed graph (weighted). Under certain conditions, the probability of accessing each node from the limit situation converges to a stationary distribution. The stationary probability value on the node is the PageRank value, which is used to represent the importance of the node | L Page et al, 1998
[Clustering] | Accelerating exact k-means algorithms with geometric reasoning | Reading notes | The paper introduced by K-Means in computers, K-Means belongs to Partition-based methods, and the idea is to initialize the central point, and then through heuristic algorithms, the goal of "the points in the class are close enough and the points between classes are far enough" is achieved | et al Dan Pelleg, 1999
[Anomaly Detection - Machine Learning] | LOF: Identifying Density-Based Local Outliers | Reading Notes | The LOF algorithm proposed in this article is a density-based algorithm. Its advantage is that it takes into account the local and global properties of the data set (the definition of local accessible density actually implies an assumption that there are no points greater than or equal to K repetitions). The outliers are not determined by absolute values, but are determined relative to their domain point density. Therefore, when there are different clusters of different densities in the dataset, the LOF algorithm performs well and is more suitable for medium and high-dimensional datasets | Markus M. Breunig et al, 2000
[Clustering] | Mean Shift: A Robust Approach toward Feature Space Analysis | Read Notes | The implementation is an algorithm for sliding windows. In each iteration, the center of the sliding window is moved to the higher density area by moving the center point to the average position of all points in the window (hence the name). The density in the sliding window is proportional to the number of points inside it. By switching to the average position of points in the window, the window will gradually move to areas with higher point density. Advantages: The biggest advantage of Mean-Shift is that it can automatically discover the number of clusters without manual selection; the fact that the center of the cluster is aggregated to the maximum density point is also very satisfactory, because it can be understood very intuitively and naturally fit the data-driven; it can handle cluster classes of any shape; the algorithm only needs to set the radius parameter, the radius affects the kernel density estimation of the data set; the algorithm results are stable and there is no need to perform sample initialization similar to K-means; the disadvantages: the disadvantage is that the selection of window size/radius "r" may be non-trivial; the radius is set too small, the convergence is too slow, and the number of cluster classes is too large; the radius is set too large, and some cluster classes may be lost. For larger feature spaces, the calculation amount is very large | Dorin Comaniciu et al, 2002
[Vector recall] | similarity estimation techniques from rounding algorithms | Reading notes | The SimHash proposed in the paper was an algorithm used by Google to deduplicate text at that time. The main method is to extract a certain number of keywords from the document, then convert them into hash codes and add them according to columns, 1+weight, 0-weight, and the result is obtained according to the integer of 1 and the negative number is 0 to obtain the final hash code, and then divide the hash code into m tables, and memorize and calculate and search separately | Moses S. Charikar et al,2002
[Graph Algorithm - Text Summary - Unsupervised] | TextRank: Bringing Order into Texts | Reading Notes | This article proposes a graph-based sorting algorithm for keyword extraction and document summary. It is improved by the PageRank algorithm. It uses the co-occurrence information (semantics) between words inside a document to extract keywords, and uses the extracted automatic abstract method to extract the key sentences of the text. Compared with the TF-IDF method, the relationship between text elements can be fully utilized. Of course, it is also affected by word participle, stop word, text cleaning | Rada Mihalcea et al, 2004
[Clustering] | k-means++: The Advantages of Careful Seeding | Reading Notes | Original K-Means (randomly selected cluster center) are sensitive to initialization cluster centers, so k-means++ has been improved, randomly select the first initial center point, calculate the distance between other points and the center point, and select the second initial center point according to the distance with a higher probability, and so on | et al David Arthur, 2006
[Clustering] | Clustering by Passing Messages Between Data Points | Reading Notes | The basic idea is to regard all samples as nodes of the network, and then calculate the clustering center of each sample through message delivery of each edge in the network. During the clustering process, there are two types of messages passed between each node, namely responsibility and availability. The AP algorithm continuously updates the attraction and attribution values of each point through an iterative process until m high-quality Expemplars are generated. The advantage is that there is no need to specify the clustering "number" parameter; the clustering center point is generated from the actual sample point; the initial value is insensitive and there is no requirement for the symmetry of the distance matrix. AP starts the algorithm by inputting a similarity matrix, so the data is allowed to be asymmetric, the data is very applicable, and the data is very robust, and the error is low. The disadvantage is that Preference and Damping factor need to be manually specified in AP clustering applications. This is actually a variant of the original cluster "number" control, and the algorithm is relatively complex | Brendan J. Frey et al, 2007
[Cluster-Community Discovery-Graph Algorithm] | Maps of random walks on complex networks reveal community structure | Reading Notes 1 / Reading Notes 2 | Classic infomap algorithm, which belongs to the dynamic community discovery algorithm. The core idea of infoma is to create a sequence by constructing the transfer probability, performing random walks on the graph, and then performing hierarchical encoding of the sequence to minimize the target, thereby completing clustering. There are several points that need to be explained: (1) The construction of transfer probability, for example, on the basis of the weighted graph, the probability is obtained by normalizing the weight (because the optimization goal only looks at the relative probability, so in fact it is OK to normalize or not); (2) Random walk refers to the path sequence obtained by jumping from one point to another according to probability in the graph (there is no need to really generate a sequence in realization, and the goal is to optimize this random sequence to achieve stability); (3) The so-called minimization goal is the minimum information entropy (shortest coding length) objective function obtained under the hierarchical encoding scheme; (4) The link of nodes merged into the class is to try to assign each node to the class where the neighbor node is located in sequence, and assign the class when the average bit drops the maximum to the node. If it does not fall, the class of the node remains unchanged. Infomap algorithm has a very clear information theory explanation, and there is almost no hyperparameter (the only "travel probability" parameter) | M. Rosvall et al, 2007
[Community Discovery-Clustering-Graph Algorithm] | Near linear time algorithm to detect community structures in large-scale networks | Reading Notes | LPA is a community discovery algorithm based on label propagation. Its core idea is not complicated. By initializing a unique label (PUSH algorithm) for the nodes in the graph, and then randomly selecting nodes in each iteration, changing their own labels according to the labels to which the nodes connected to it belong. The selection method can be based on the number, weight, etc. If there are multiple identical ones, it will be randomly selected until it stabilizes after multiple iterations. The LPA algorithm is simple and does not require a specified number of communities, but the disadvantage is the update order and random selection in the algorithm process, which makes the algorithm unstable. The entry point for improvement is naturally to start from these two aspects | Usha Nandini Raghavan et al, 2007
[Clustering] | A Tutorial on Spectral Clustering | Reading Notes | Not the original paper, but this article talks very well about Spectral Clustering. Spectral Clustering is to use Laplacian eigenmaps to reduce the dimensionality of data (simplely speaking, it is to convert the data into an adjacency matrix or similarity matrix, then convert it into a Laplacian matrix, then perform feature decomposition of the Laplacian matrix, and arrange the smallest K feature vectors together), and then use k-means to complete the clustering. Spectral clustering is a good method. The effect is usually better than k-means and the computational complexity is lower, all thanks to the effect of dimensionality reduction. Advantages: Spectral clustering only requires a similarity matrix between data, so it is very effective for clustering of sparse data. This is difficult to achieve in traditional clustering algorithms such as K-Means; because they use dimensionality reduction, the complexity of processing high-dimensional data clustering is better than that of traditional clustering algorithms. Disadvantages: If the dimension of the final cluster is very high, the operating speed of spectral clustering and the final clustering effect are not good due to insufficient dimensionality reduction; the clustering effect depends on similar matrices, and the final clustering effect obtained by different similar matrices may be very different | Ulrike von Luxburg et al, 2007
[Anomaly Detection - Model - Machine Learning] | Isolation Forest | Reading Notes 1 / Reading Notes 2 / Reading Notes 3 | The first paper of the classic isolated forest algorithm, an extended version was published in 2012. Isolated Forest is a fast outlier detection method based on Ensemble, which mainly targets anomaly points in continuous structured data, with linear time complexity and high accuracy. Its theoretical basis is (1) The proportion of abnormal data to sample size is very small; (2) The eigenvalues of abnormal points differ greatly from normal points. Isolated forests are simple and efficient, but in some cases, for example, the distribution of data is not along the characteristic axis, but is randomly distributed, or flow-type distribution, the effect of isolated forests is not good, so you need to consider choosing another method | Fei Tony Liu et al, 2008
[Community Discovery-Graph Algorithm] | Fast unfolding of communities in large networks | Reading Notes 1 | Reading Notes 2 | The classic Louvain algorithm, which is a community discovery algorithm based on module optimization, and is a heuristic greedy algorithm. The process is: (1) At the beginning, each vertex is treated as a community, with the number of communities the same as the number of vertices; (2) Combine each vertex with its adjacent vertices in sequence to calculate whether their maximum modularity gain is greater than 0. If it is greater than 0, put the node into the community where the adjacent node with the largest modularity increment is located; (3) Iterate the second step until the algorithm is stable, that is, the communities to which all vertices belong will no longer change; (4) Compress all nodes in each community into one node, the weight of the points in the community is converted into the weight of the new node ring, and the weight between communities is converted into the weight of the new node edge; (5) Repeat steps 1-3 until the algorithm is stable. It is generally believed that the modular index used to evaluate the effect will have a clear community structure when it is between 0.3 and 0.7. The advantage of the Louvain algorithm is that it has low time complexity (nlogn), suitable for large-scale network and community division results, with stable specific indicators, and naturally hierarchical. The disadvantage is that it can easily lead to "overfitting". | Vincent D. Blondel et al, 2008
[Dialogue System-Dialogue State Management] | The Hidden Information State model: A practical framework for POMDP-based spoken dialogue management | Articles about dialogue state management can be used to supplement relevant background knowledge | Young et al,2010
[Vector recall] | Product quantization for nearest neighbor search | Reading notes | This paper is the success of the PQ algorithm. PQ is a quantization method, essentially a compressed expression of data (this paper uses the KMeans algorithm to obtain a codebook with the center of mass). First, the vector is divided into m segments, and each segment is converted into a compressed vector according to the codebook, and then a similar search is performed using SDC or ADC algorithm. However, the paper further improved and proposed the IVFADC algorithm, an ADC algorithm based on inverse index, which was divided into two steps. The first step is to PQ once (become a coarse quantizer), and then subtract the quantized vectors with the vector to obtain the residuals. The second step is to perform PQ once on all the obtained residual sets, and finally use the resulting vector to establish the inverse index | Herve Jegou et al, 2011
[Clustering] | Scalable K-Means++ | Reading Notes | K-Means++ is difficult to parallel due to its sampling strategy, limiting its use on large-scale datasets. To solve this problem, k-means II changes the sampling strategy (in the form of oversampling), initializes a center point, and then logs (n) times, selects multiple points according to a probability calculation formula at a time to add them to the center set. The final candidate center set is then clustered through k-means++ to select k cluster centers | Bahman Bahmani et al, 2012
[Vector recall] | Fast Search in Hamming Space with Multi-Index Hashing | Reading Notes | Mainly to solve R-Neighbors of query and KNN query on Hamming space, the paper proposes a hashing method with multi-segment index. The query efficiency reaches sublinearity. The method is to divide the Hamming code into m segments, and quickly find the results of the Hamming distance in each segment with less than r/m. All results are merged into candidate sets | Mohammad Norouzi et al, 2012
[Vector Recall] | Learning Deep Structured Semantic Models for Web Search using Clickthrough Data | Reading Notes | The classic DSSM semantic similarity matching model is what we usually call the double tower model. Using Word Hashing's n-gram was very unique at that time. Its core idea was to map query and doc to the semantic space of the common dimension, and to maximize the cosine similarity between query and doc semantic vectors, we can train the implicit semantic model to achieve the purpose of retrieval. Negative Sampling 1:4 | Po-Sen Huang et al, 2013
[Machine Learning] | Parameter Server for Distributed Machine Learning | Reading Notes | The paper says that the Parameter Server introduced in this article belongs to the third generation PS, providing a more general design, including a Server Group and several Worker Groups in architecture, providing the following features: Efficient Communication, Elastic Scalability, Fault Tolerance and Durability, Ease of Use | Mu Li et al, 2013
[Vector recall] | Optimized Product Quantization | Reading notes | PQ is a method that directly and simply and roughly segments the original eigenvectors without removing the correlation. If you remove the correlation and then perform PQ to make the retrieval effect better. OPQ provides a method of balancing information in each subspace, that is, using an orthogonal matrix to rotate the cluster center, and provides two algorithm ideas for Non-Parametric and Parametric | Tiezheng Ge et al, 2013
[Language Model] | Efficient Estimation of Word Representations in Vector Space | Reading Notes | One of the pioneering works of Word2vec, specializing in two tricks in training: hierarchical softmax and negative sampling | Tomas Mikolov et al, 2013
[Language Model] | Distributed Representations of Words and Phrases and their Compositionality | Reading Notes | One of the pioneering works of Word2vec, which proposed a more streamlined language model framework based on predecessors and used to generate word vectors. This framework is Word2vec | Tomas Mikolov et al, 2013
[Vector Recall] | Speeding Up the Xbox Recommender System Using a Euclidean Transformation for Inner-Product Spaces | Microsoft's Inner Product quick calculation method mainly solves the problem of Inner Product Top-K Search. After simplifying the problem to an Euclidean distance search problem through various formulas, use a PCA-Tree to solve it | Yoram Bachrach et al, 2014
[Machine Learning] | Scaling Distributed Machine Learning with the Parameter Server | Reading Notes | In PS, each server is actually only responsible for the part of the parameters assigned (servers jointly maintain a global shared parameter), and each work is only assigned part of the data and processing tasks. Compared with its previous article, PS has described it in more detail and expanded some details. The combination of the two articles has benefited a lot | Mu Li et al, 2014
[Vector recall] | Approximate nearest neighbor algorithm based on navigable small world graphs | Reading notes | Classic NSW algorithm, based on building an approximate DG graph, add Expressway mechanism. When building, use abandoned lists and dynamic lists to speed up Yury Malkov et al, 2014
[Dataset] | The Second Dialog State Tracking Challenge | The DSTC series corpus is specially used for dialogue state tracking, which is very classic, but its official website seems useless | Henderson et al, 2014
[Vector recall] | Locally Optimized Product Quantization for Approximate Nearest Neighbor Search | LOPQ is further optimized based on OPQ. OPQ only considers the rotation problem of CodeBook. LOPQ considers that each subspace performs different rotations | Yannis Kalantidis et al, 2014
[Vector Recall] | Asymmetric LSH (ALSH) for Sublinear Time Maximum Inner Product Search (MIPS) | Reading Notes | Traditional MIPS problem cannot find the LSH function. For this paper, an algorithm of "asymmetric LSH" is proposed. Its core technique is to construct vectors through "asymmetric transformation" to eliminate the impact of the vector modulus length of the set X to be found on the MIPS result. The problem of cleverly converting the problem to Euclidean distance and finding the approximate solution of NN through the LSH function | Anshumali Shrivastava et al, 2014
[Graph Algorithm-GNN-Model-Unsupervised] | DeepWalk: Online Learning of Social Representations | Read Note 1 / Read Note 2 | The DeepWalk proposed in this article is a method that we understand that Graph Embedding cannot be bypassed. The core idea is to use RandomWalk to sample nodes in the graph, so as to use the co-occurrence relationship between nodes in the graph to learn vector representation of nodes (the idea comes from Word2Vec skip-gram). The whole is divided into two steps. The first step is to randomly walk the sampling node sequence, and then use skip-gram to learn the representation vector | Bryan Perozzi et al, 2014
[Language Model-Text Similarity/Matching/Classification] | Convolutional Neural Networks for Sentence Classification | Classic TextCNN, static/non-static several eigenvector learning methods | Yoon Kim et al, 2014
[Deep Learning] | Neural Machine Translation Bu Jointly Learning To Align And Translate | Original text of Bahdanau Attention | Bahdanau et al, 2014
[Deep Learning] | Convolutional Neural Networks at Constrained Time Cost | A good overview of computational cost and tradeoffs between depth and filter size for convolutional networks | Kaiming He et al, 2014
[Speech System-Speech Recognition-Model] | Attention-Based Models for Speech Recognition | Location Sensitive Attention used by Tacotron2 | Chorowski et al, 2015
[Dialogue System] | Context Sensitive Spoken Language Understanding Using Role Dependent LSTM Layers | Work done in SLU using LSTM, through agent and client role division, it can solve the ambiguity in multiple rounds of conversations | Hori et al, 2015
[Deep Learning] | Batch Normalization: Accelerating Deep Network Training by Reducing Internal Covariate Shift | Reading Notes | Classic Batch Normalization Original Paper | Sergey et al, 2015
[Distilling-Pre-training] | Distilling the Knowledge in a Neural Network | Reading Notes | The pioneering work of the distillation method, transferring the knowledge of a complex model to a simple model. The specific method is to add a temperature parameter to the softmax of the complex classification model (teacher), and then train it with hard target. The output of the softmax of the model is the soft target we need. Then use a simple model to train based on soft and hard targets. When the simple model is trained in soft targets, the temperature of softmax is set the same as that of the teacher. When the hard target is trained, the temperature is set 1, and then the loss calculation is used to calculate the weighted average of the cross entropy of the two targets (the cross entropy of the output data of the soft targets and the small model, the cross entropy of the output data of the hard targets and the small model). In addition, through gradient calculation formula conversion, when my temperature is particularly large (and the logits generated by the model are 0), knowledge distillation is equivalent to the MSE of the logits of the large model and the logits of the small model | Geoffrey Hinton et al, 2015
[GNN-Graph Algorithm-Model-Unsupervised] | LINE: Large-scale Information Network Embedding | Reading Notes | The LINE method proposed in this article is applied to graph embedding, which is a method based on domain-like assumptions. In total, the article proposes a perspective of similarity calculation in two dimensions: (1) First-order is suitable for undirected graphs, which is believed that the two points directly connected in the graph are similar, so the purpose is to make the vector representation distribution of the two points as similar as possible; (2) Second-order is suitable for undirected graphs or directed graphs. It is believed that it is a node. In addition to learning its own representation vector, it also needs a representation to represent its directly adjacent nodes (as a context vector). When two nodes are not directly connected, if their neighbor nodes overlap, the context vector can be used to calculate the similarity. Node number sequence number and encoded with embedding layer. Both methods are optimized and calculated by KL divergence as the objective function | Jian Tang et al, 2015
[Model] | Highway Networks | Reading Notes | Highway Networks' name acquisition is very interesting, and the entire network structure idea is also in line with the naming. Simply put, it is to limit the output of the network by setting a function T (drawing from the gate idea in LSTM). When T is taken 0, the output is y=x. At this time, the gradient is directly transmitted to the next layer. That is to say, the gradient transmission can be controlled through T, thereby solving the problem of gradient disappearance to a certain extent. Highway has fewer parameters, suitable for transform of single nonlinear layer | Rupesh Kumar Srivastava et al, 2015
[Deep Learning] | Learning both Weights and Connections for Efficient Neural Networks | There is a table that lists the relative costs of computing and memory access, and in addition to discussing how to streamline neural networks | Song Han et al, 2015
[Model] | Pointer Networks | Reading Notes | The original text is a network structure designed around solving convex hulls. The weight of Attention is directly used for prediction, which can adapt to the scale of inputs. Many network structure applications later developed into Copying Mechanism to solve OOV problems | Oriol Vinyals et al, 2015
[Dialogue System-Model] | A Neural Conversational Model | Dialogue Model of Seq2Seq Structure | Oriol et al, 2015
[Dataset] | The Ubuntu Dialogue Corpus: A Large Dataset for Research in Unstructured Multi-Turn Dialogue Systems | Ubuntu Unstructured Multi-Round Dialogue Dataset | Ryan Lowe et al, 2015
[Vector Recall] | Clustering is Efficient for Approximate Maximum Inner Product Search | K-Means Tree, using K-Means to build trees | Alex Auvolat et al, 2015
[Model] | Training Very Deep Networks | Reading Notes | Classic Highway networks, based on deep CNN stacking networks, use transform gate and carry gate (in fact, it was later unified as Shortcut), to bring shallow feature information to the deep layer to solve the problem of divergence and difficulty in training in deep networks | Rupesh Kumar Srivastava et al, 2015
[Deep Learning] | Effective Approaches to Attention-based Neural Machine Translation | Original text of Luong Attention | Luong et al, 2015
[Pre-training - Language Model] | Character-Aware Neural Language Models | Provide a powerful, powerful language model that encodes subword dependencies while solving rare word problems in previous models, using fewer parameters to obtain comparable expressiveness | Yoon et al, 2015
[Model-Subword] | Neural Machine Translation of Rare Words with Subword Units | It is the Byte Pair Encoding we are familiar with, which is a method of using some byte pairs that appear frequently to form new bytes | Sennrich et al, 2015
[Vector Recall] | Deep Compression: Ccompressing Deep Neural Networks With Pruning, Trained Quantization And Huffman Coding | Reading Notes | ICLR's best paper, the main content is about the compression of deep learning network parameters. It is divided into three steps, Network pruning, that is, first train a network, then prune some connections with very small weights (determined by the threshold), and then retrain the network. The second step is to quantify the weight; the third step is to use Huffman coding for lossless encoding | Song Han et al, 2015
[Machine Learning] | Optimal Whitening and Decorrelation | Mathematical Proof of Five Whitening Methods | Agnan Kessy et al, 2015
[Deep Learning] | Strategies for Training Large Vocabulary Neural Language Models | Reading Notes | It mainly summarizes some Softmax and Samplings at that time, and proposes the Differentiated Softmax method | Wenlin Chen et al, 2015
[Machine Learning-Model] | XGBoost: A Scalable Tree Boosting System | Reading Notes 1 / Reading Notes 2 | The XGBoost proposed in this article is an integrated algorithm based on Boosting. To be more precise, XGBoost includes optimizations of mathematical principles and engineering implementations, and has many advantages including higher accuracy, strong flexibility, and parallel computing. Generally, in some business scenarios, baseline (integration in data science competitions can be done without brains) to implement package xgboost | Tianqi Chen et al, 2016
[Clustering] | Approximate K-Means++ in Sublinear Time | Reading Notes | K-MC2 is different from the sampling method of k-means II. It uses MCMC sampling. The main idea is to replace the sampling method in K-Means++ with the MCMC (Markov Chain Monte Carlo) based sampling method (for the introduction of MCMC, please refer to: MCMC Random Sampling). The MCMC method is used to sample a sequence of length M, and the last (K-1) numbers are taken as the center point to initialize. The target distribution is a function of distance. The longer the distance is satisfied, the greater the probability (the meaning of the expression is the same as k-means++). The proposal distribution is a normal function, 1/sample number. | Olivier Bachem et al, 2016
[Clustering] | Fast and Provably Good Seedings for k-Means | Reading Notes | AFK-MC2 is based on K-MC2 improvement. Since the proposal distribution of K-MC2 is a normal function and is not robust enough, AFK-MC2 adds the distance-related distribution as a term to the original distribution, optimizing the proposal distribution | Olivier Bachem et al, 2016
[Model] | Deep Residual Learning for Image Recognition Reading Notes | Classic ResNet, based on deep CNN stacking network, uses residual connections (2 or 3 layers in ResNet) to solve the degradation problem in the depth model. The optimal residual structure is to advance both BN and ReLU and become pre-activation | Kaiming He et al, 2016
[Model-text similarity/match/categorization] | Siamese Recurrent Architectures for Learning Sentence Similarity | Siamese LSTM, a model used to calculate sentence similarity | Jonas Mueller et al, 2016
[Model-text similarity/match/classification] | Learning Text Similarity with Siamese Recurrent Networks | The network contains 4 layers of BiLSTM (64-d hidden), the hidden state and cell state of BiLSTM of the last layer are concat, and then averaged in the timestep dimension, followed by a Dense layer (the activation function is tanh), and the two Embedding Spaces are calculated by Cosine sim, and the obtained similarity score E is used for the calculation of the loss function. The loss function uses a comparison loss function, and the calculation method is, the positive example of the loss function: 1/4(1-E)^2, and the negative example: E^2 (if E<m), otherwise 0 | Paul Neculoiu et al, 2016
[Deep Learning] | Exploring the Limits of Language Modeling | CNN Softmax method, although it still cannot be separated from the original Softmax, it works very well after changing the perspective | Rafal Jozefowicz et al, 2016
[Deep Learning] | Weight Normalization: A Simple Reparameterization to Accelerate Training of Deep Neural Networks | Weight Normalization is a method of normalizing the weight dimension | Tim Salimans et al, 2016
[Model] | Incorporating Copying Mechanism in Sequence-to-Sequence Learning | Reading Notes | CopyNet model, a model that uses Copying Mechanism to alleviate the problem of unlogined words. In tasks such as text summary, the effect is good | Jiatao Gu et al, 2016
[Vector recall] | Efficient and robust appropriate nearest neighbor search using Hierarchical Navigable Small World graphs | Reading notes | HNSW algorithm, based on NSW, introduces hierarchical structure to implement Expressway mechanism, achieve the idea of rough search at the top level and detailed search at the bottom level | Yu. A. Malkov et al, 2016
[Model-Subword] | Achieving Open Vocabulary Neural Machine Translation with Hybrid Word-Character Models | A very excellent framework, mainly for word-level translation, but it can be convenient to use Character-level input when needed | Luong et al, 2016
[Dialogue System-Task-Task-Task-Task-Official Dialogue System | Reading Notes | A Task-Task-Task-Task-Official Dialogue Model Architecture that is well worth reading | Wen et al,2016
[Deep Learning] | Training Deep Nets with Sublinear Memory Cost | keras_recompute | This paper talks about a trick that saves memory by exchanging time for space, that is, by discarding the results of low-cost operations, that is, retaining none of the intermediate result feature maps, killing them all, and recalculating them during backpropagation (of course, the paper's compromise is to retain a feature map every sqrt(n).). Can reduce memory by sqrt(n) by one, surpassing most memory-saving tricks. For specific implementations, please refer to tf.recompute_grad, or an open source implementation | Tianqi Chen et al, 2016
[Model-Subword] | Learning Character-level Representations for Part-of-Speech Tagging | Character-level to build word-level. This network structure mainly convolves characters to generate word embeddings, and at the same time uses a fixed window to operate on word embeddings of PoS tags | Jason et al, 2016
[Language Model - Text Similarity/Matching/Classification] | Very Deep Convolutional Networks for Text Classification | VDCNN, character level, uses only small-scale convolution kernel pooling operations, and contains 29 convolutional layers. The effect improvement is not very obvious, but the highlight is that the number of CNN layers is relatively deep, which proves to some extent that Shortcut connections like ResNet can reduce the impact of gradient vanishing, thereby improving the effect | Alexis Conneau et al, 2016
[Model-Language Model] | A Joint Model for Word Embedding and Word Morphology | The goal of this model is the same as word2vec, but uses the input of Character-level, which uses a bidirectional LSTM structure to try to capture morphology and be able to infer roots | Kris et al, 2016
[Dialogue System-Dialogue State Tracking] | Neural Belief Tracker: Data-Driven Dialogue State Tracking | Reading Notes | NBT Framework, Good Articles on Understanding Belief State and Tracking | Young et al, 2016
[Machine Learning] | Gaussian Error Linear Units (GELUS) | Reading Notes | The goal of GELU is to add regularization to activation (with the ability to fit nonlinearly). ReLU will deterministically multiply the input by a 0 or 1, while Dropout will be randomly multiplied by a 0. GELU also realizes this function by multiplying the input by 0 or 1, but whether the input is multiplied by 0 or 1 is randomly selected depending on the input's own distribution at the same time. In other words, whether it is 0 or 1 depends on how much the current input is greater than the rest of the input. Since the input x of neurons often follows a normal distribution (especially Normalization is common in deep networks), GELU can be defined as a "cumulative distribution function of standard normal distribution". Using erf, the formula can be obtained: x/2*(1+erf(x/sqrt(2))) | Dan Hendrycks et al, 2016
[GNN-Graph Algorithm-Model-Unsupervised] | node2vec: Scalable Feature Learning for Networks | Reading Note 1 / Reading Note 2 | The node2vec proposed in this article is a graph embedded method that comprehensively considers the DFS neighborhood and the BFS neighborhood. The overall algorithm idea framework inherits DeepWalk, obtains sequences through random walks, and uses Word2Vec to learn to represent vectors. Unlike DeepWalk, it uses biased random walks, and uses two parameters p and q to control the direction of the sequence walk in the form of alias sampling (whether to choose an adjacency node or a second-degree node) | Aditya Grover et al, 2016
[GNN-Graph Algorithm-Model-Unsupervised] | Structural Deep Network Embedding | Reading Notes 1 / Reading Notes 2 | The SDNE model proposed in this article is the graph embedding method proposed in the same year as Node2Vec, which can be regarded as an extension based on the LINE method. SDNE uses an autoencoder structure to optimize both 1st and 2nd order similarities simultaneously (LINE is optimized separately), and the learned vector representation can retain local and global structures and is robust to sparse networks.通过输入的邻接矩阵和网络重构出的邻接矩阵计算一阶二阶损失函数,并配合一个正则项组成联合损失函数进行优化| Daixin Wang et al, 2016
[模型-文本相似度/匹配/分类] | Bag of Tricks for Efficient Text Classification | 阅读笔记| 比较经典的FastText,比较依赖Word Embedding的质量(槽点本身难点就在于embedding,结果文章不谈这个),整个网络结构使用N-gram,对得到的Embedding求和,并过两个Dense然后输出,本身网络结构就那没啥,当然fast啦,外加论文具体加了hashing trick,hierarchical softmax等进行加速、内存优化| Armand Joulin et al,2016
[模型-语言模型] | Enriching Word Vectors with Subword Information | word2vec的升级版,对于具有大量形态学的稀有词和语言有更好的表征,它也可以说是带有字符n-gram的w2v skip-gram模型的扩展| Piotr et al,2016
[深度学习] | Layer Normalization | 阅读笔记| 层归一化方法,针对Batch Normalization的改进| Jimmy et al,2016
[深度学习] | Instance Normalization:The Missing Ingredient for Fast Stylization | Instance Normalization是一种不受限于批量大小的算法专门用于Texture Network中的生成器网络| Dmitry Ulyanov et al,2016
[对话系统-对话意图识别-对话槽位填充] | Attention-Based Recurrent Neural Network Models for Joint Intent Detection and Slot Filling | 使用Attention-Based的RNN模型进行联合意图识别和槽位填充,达到不错的效果| Bing Liu et al,2016
[GNN-文本相似度/匹配/分类-图算法] | Semi-supervised classification with graph convolutional networks | 阅读笔记1 / 阅读笔记2 | 这就是非常经典的GCN啦,GCN对非结构化数据构造特征节点,进而构造graph,通过使用邻接矩阵、度矩阵等图结构对输入的节点embedding进行优化学习(本质上是一种局部加权求和的方式,类似Attention的思想,不过有很多trick在里面,比如对称归一化等),能够通过相邻节点传递特征信息。GCN能够有效地提取空间特征来进行机器学习,虽然目前在NLP任务中的表现不算特别突出,但是它的功劳在于提供一种处理、研究的模型,扩广了解决方案的思路| Thomas N. Kipf et al,2016
[深度学习] | Efficient softmax approximation for GPUs | 阅读笔记| Adaptive Softmax,针对GPU的矩阵计算,实现了多倍与普通Softmax计算效率的提升,值得一看| Edouard Grave et al,2016
[机器学习] | An overview of gradient descent optimization algorithms | 阅读笔记| 对当前主流的梯度下降算法进行概述| Sebastian Ruder et al,2016
[模型-Subword] | Google's Neural Machine Translation System: Bridging the Gap between Human and Machine Translation | wordpiece作为BERT使用的分词方式,其生成词表的方式和BPE非常相近,区别在于BPE选择频率最高的相邻字符对进行合并,而wordpiece是基于概率生成的| Yonghui et al,2016
[模型-Subword] | Fully Character-Level Neural Machine Translation without Explicit Segmentation | 比较经典的Character-Level的Subword算法模型| Jason et al,2016
[深度学习] | Categorical Reparameterization With Gumbel-Softmax | 阅读笔记| Gumbel Max由来已久,而这篇文章就是基于Gumbel Max,首次提出并应用Gumbel Softmax的。目标就是使用梯度估计的方法,来解决Categorical Distribution中,使用类似argmax操作导致网络不可微的问题。文章主要探讨了部分隐变量是离散型变量的变分推断问题,比如基于VAE的半监督学习| Eric Jang et al,2016
[对话系统-检索式对话系统] | Sequential Matching Network: A New Architecture for Multi-turn Response Selection in Retrieval-Based Chatbots | 阅读笔记| SMN检索式对话模型,多层多粒度提取信息| Devlin et al,2016
[深度学习] | Large-Margin Softmax Loss for Convolutional Neural Networks | 阅读笔记| L-Softmax在原Softmax的基础上增加了控制系数m,使得类内距离尽可能小,类间距离尽可能大| Weiyang Liu et al,2016
[深度学习] | An empirical analysis of the optimization of deep network loss surfaces | 论文中得出一个结论,即Batch Normalization更有利于梯度下降| Shibani et al,2016
[模型-语言模型] | Language Modeling with Gated Convolutional Networks | 阅读笔记| 受LSTM门控机制的启发,将线性门控机制应用于卷积结构,文中对比GLU、GTU等结构性能| Yann N. Dauphin et al,2016
[语音系统-语音合成] | Tacotron: A Fully End-To-End Text-To-Speech Synthesis Model | 阅读笔记| Tacotron,端到端的语音合成系统| Yuxuan et al,2017
[模型] | Densely Connected Convolutional Networks | 阅读笔记| CVPR 2017的Best Paper,提出了DenseNet,借鉴highway networks和ResNet的思路,DenseNet将shortcut用到了“极致”——每两层之间都添加shortcut,当然具体实现中使用了一些tricks防止模型过大的问题| Gao Huang et al,2017
[模型-语言模型] | A Simple But Tough-To-Beat Baseline For Sentence Embeddings | Smooth Inverse Frequency,一种简单但是效果好的Sentence Embedding方法| Sanjeev Arora et al,2017
[深度学习] | Sigmoid-Weighted Linear Units for Neural Network Function Approximation in Reinforcement Learning | 提出SILU激活函数,其实从某种角度讲就是GELU激活的一种近似,x*sigmoid(x) | Stefan Elfwing et al,2017
[深度学习] | Cosine Normalization: Using Cosine Similarity Instead of Dot Product in Neural Networks | Cosine Normalization是一种将unbounded的向量点积换成夹角余弦操作,从而进行归一化的方法| Luo Chunjie et al, 2017
[深度学习] | Massive Exploration of Neural Machine Translation Architectures | 阅读笔记| 展示了以NMT架构超参数为例的首次大规模分析,实验为构建和扩展NMT体系结构带来了新颖的见解和实用建议。 | Denny et al,2017
[GNN-图算法-模型-无监督] | struc2vec: Learning Node Representations from Structural Identity | 阅读笔记1 / 阅读笔记2 | | 本文提出的struc2vec方法是用于graph embedding,相较于经典的DeepWalk和Node2Vec方法(关注存在直连节点的相似性),struc2vec如它名字一样,关注的是节点的结构相似性,这使得它可以表示两个距离很远但结构(连接度,局部拓扑结构)相似的节点。大体的流程分为四步:(1)根据不同距离的邻居信息分别算出每个节点对的结构相似度,这涉及到了不同层次的结构相似度的计算,其中使用DTW(一种动态规划方法)计算有序度序列的距离;(2)构建一个多层次的带权重网络M,每个层次中的节点皆由原网络中的节点构成,距离计算对应其层数的有序度序列的距离;(3)在M中生成随机游走,为每个节点采样出上下文;(4)使用word2vec的方法对采样出的随机游走序列学习出每个节点的节点表示| Leonardo FR Ribeiro et al, 2017
[模型] | Get To The Point: Summarization with Pointer-Generator Networks | 阅读笔记| 结合Copying Mechanism和Coverage mechanism两种技巧的LSTM-Base模型,一定程度上解决OOV和重复词问题,经典值得一读| Abigail See et al,2017
[深度学习] | SphereFace: Deep Hypersphere Embedding for Face Recognition | 阅读笔记| A-Softmax,思路和L-Softmax差不多,区别是对权重进行了归一化| Weiyang Liu et al,2017
[模型-语言模型] | Supervised Learning of Universal Sentence Representations from Natural Language Inference Data | InferSent,通过不同的encoder得到Sentence Embedding,并计算两者差值、点乘得到交互向量,从而得到相似度| Alexis Conneau et al,2017
[对话系统-对话意图识别] | Latent Intention Dialogue Models | 阅读笔记| 离散潜在变量模型学习对话意图的框架| Wen et al,2017
[模型-预训练-语言模型] | Attention Is All You Need | 阅读笔记| Transformer的开山之作,值得精读| Ashish et al,2017
[社区发现-综述] | Network Community Detection: A Review and Visual Survey | 阅读笔记| 一篇关于社区发现的综述,文章对社区发现概念和发展进行了介绍,并对当下社区发现算法按照分类进行了细致的介绍,包括传统的社区发现技术、基于分裂的社区发现技术、基于模块化优化的社区发现技术、重叠社区发现技术、动态社区发现技术等| Bisma S. Khan et al, 2017
[深度学习] | ProjectionNet: Learning Efficient On-Device Deep Networks Using Neural Projections | 阅读笔记| 一种叫ProjectionNet的联合框架,可以为不同机器学习模型架构训练轻量的设备端模型。 | Google et al,2017
[深度学习-损失函数] | Focal Loss for Dense Object Detection | 阅读笔记| 分类问题我们一般使用交叉熵损失函数,交叉熵损失函数是平等对待正负样本的,当正负样本不均衡的时候,正样本总的损失会淹没小量负样本总的损失,导致模型最终的学习方向并不会把重点放在负样本上,解决方案就是增加负样本的权重,减少正样本的权重,从而是模型重点倾向于学习负样本的规律。这种方式还是不能解决easy/heard samples的问题,Focal loss对交叉熵损失函数增加了一个调制因子,实现对easy samples的降权,从而使模型训练的损失可以集中在比较难学习的负样本上| Tsung-Yi Lin et al,2017
[对话系统-任务型对话-对话状态跟踪] | An End-to-End Trainable Neural Network Model with Belief Tracking for Task-Oriented Dialog | 阅读笔记| 面向任务的对话系统的新型端到端可训练神经网络模型| Liu et al,2017
[数据集] | DailyDialog: A Manually Labelled Multi-turn Dialogue Dataset | 数据集地址| 包含对话意图和情感信息的多轮对话数据集| Yanran Li et al, 2017
[机器学习] | Swish: A Self-Gated Activation Function | 提出的Swish激活函数,通SILU激活函数一样,没啥差别,x*sigmoid(x) | Prajit Ramachandran et al,2017
[综述-对话系统] | A Survey on Dialogue Systems:Recent Advances and New Frontiers | 对话系统的最新研究和方向| Chen et al,2017
[语音系统-语音合成] | Natural TTS Synthesis By Conditioning Wavenet On Mel Spectrogram Predictions | 阅读笔记| Tacotron2,相较于Tacotron有着更好的性能,使用WaveNet作为Vocoder | Jonathan et al,2017
[异常检测-机器学习] | XGBOD: Improving Supervised Outlier Detection with Unsupervised Representation Learning | 本文主要是提出一种通过无监督算法来增广特征,进而融合原始特征用于XGB的有监督的训练思路,命名为XGBOD。在ADBench中,半监督的总体效果来讲好于直接使用XGB,监督学习的情况下,指标提升差不了多少(然后XGBOD在训练代价上更大),因此在有监督的情况下,直接使用XGB作为baseline更加简单直接一些| Yue Zhao et al, 2018
[数据集] | LCQMC: A Large-scale Chinese Question Matching Corpus | LCQMC,开放域的中文语义相似度语料,更加侧重于intent相似,总共26万的文本对| Xin Liu et al,2018
[数据集] | The BQ Corpus: A Large-scale Domain-specific Chinese Corpus For Sentence Semantic Equivalence Identification | 关于Bank Question的中文语义相似度语料,总共12万的文本对| Jing Chen et al,2018
[聚类] | Robust and Rapid Clustering of KPIs for Large-Scale Anomaly Detection | 阅读笔记| 关于快速时序聚类的文章,提出ROCKA系统架构,包括了数据预处理、基线提取、相似性度量、基于密度的聚类算法。ROCKA算法仅仅是使用了派发策略,单是并未在有效的利用过程中的计算结果,导致在派发过程中复杂度较高| Zhihan Li et al,2018
[对话系统-检索式对话系统] | Multi-Turn Response Selection for Chatbots with Deep Attention Matching Network | 阅读笔记| DAM检索式对话模型,完全基于注意力机制的多层多粒度提取信息| Xiangyang et al,2018
[对话系统-对话意图识别-对话槽位填充] | Slot-Gated Modeling for Joint Slot Filling and Intent Prediction | 阅读笔记| 提出了Slot-Gated机制,联合意图识别和槽位填充效果提升| Chih-Wen Goo et al,2018
[模型-语言模型-无监督] | Unsupervised Random Walk Sentence Embeddings: A Strong but Simple Baseline | Unsupervised Smooth Inverse Frequency,USIF改进SIF对句向量长度敏感,在相似度任务上提升很大| Kawin Ethayarajh Arora et al,2018
[深度学习] | Fixing Weight Decay Regularization in Adam | 原英文版阅读笔记| 阅读笔记| 论文提出Adam在算法实现上的改进方法--AdamW(注意是算法实现)。Adam相较于传统的GD算法来说,增加了一阶动量(各时刻方向的指数移动平均值)和二阶动量(历史梯度平方和),在算法库的具体实现中,一般是通过在计算梯度之初就加上了正则项,这就导致这个正则项随着梯度一同计算,而AdamW的做法则是在梯度计算完之后,在加上这个正则项(称为weight decay)。论文中比较了SGD和SGDW、Adam和AdamW,通过实验证明了weight decay相较于一般实现的l2正则效果更好| Anonymous authors et al, 2018
[深度学习] | Additive Margin Softmax for Face Verification | 阅读笔记| AM-Softmax在A-Softmax的最大区别是AM是角度距离,A是余弦距离
[预训练-语言模型] | Deep contextualized word representations | 阅读笔记| ELMo模型原paper,想了想还是放在预训练里吧。ELMo模型很经典了,在Transformer这个大杀器提出后,依旧以LSTM为核心结构提出新的SOTA语义编码结构,还是尤其独到之处(ps:同年BERT也被提出了)。ELMo的结构可以分为两侧各一个多层LSTM,左侧的多层LSTM负责编码文本的正向语义,右侧的负责编码反向语义,然后对左右两边每一层的输出进行concat并乘上一个权重,最后的ELMo向量就是每一层输出的和。ELMo最大的亮点就是编码了文本的双向语义,因此相对于一些单向、静态编码器来讲,效果更好,但是问题也在这,这种将正反向的语义分开编码方式,就比不上BERT这种融合式的双向编码了,事实上也证明了这一点| Matthew E. Peters et al,2018
[深度学习] | Self-Attention with Relative Position Representations | 阅读笔记| 对Transformer里面用到的位置编码进行讨论,对自注意力进行改造,从而使用相对位置编码代替硬位置编码| Mihaylova et al,2018
[深度学习] | Group Normalization | Group Normalization是将输入的通道分成较小的子组,并根据其均值和方差归一化这些值| Yuxin Wu et al,2018
[语音系统-语音识别-预训练] | Syllable-Based Sequence-to-Sequence Speech Recognition with the Transformer in Mandarin Chinese | 使用Transformer应用在普通话语音识别,数据集是HKUST datasets | Shiyu et al,2018
[模型-Subword] | Subword Regularization: Improving Neural Network Translation Models with Multiple Subword Candidates | unigram在给定词表及对应概率值下,直接以最大化句子的likelihood为目标来直接构建整个词表| Kudo et al,2018
[对话系统-对话状态跟踪] | Global-Locally Self-Attentive Dialogue State Tracker | 阅读笔记| 全局-局部自注意力状态跟踪| Zhong et al,2018
[深度学习] | How Does Batch Normalization Help Optimization? | 讨论Batch Normalization是如何帮助优化器工作的,主要结论是BN层能够让损失函数更加平滑| Shibani et al,2018
[模型-对话系统] | Multi-Cast Attention Networks for Retrieval-based Question Answering and Response Prediction | 阅读笔记| 一种用于通用序列对建模的整体架构,结合多种注意力机制进行特征增强| Yi Tay et al,2018
[对话系统-数据增强] | Sequence-to-Sequence Data Augmentation for Dialogue Language Understanding | 使用seq2seq生成模型对语义文本进行数据增强,核心步骤为Delexicalisation->Diversity rank->generation->surface realisation | Yutai Hou et al,2018
[模型] | Sliced Recurrent Neural Networks | 切片RNN网络,尝试突破RNN时序限制的模型| Zeping Yu et al,2018
[模型-文本相似度/匹配/分类-GNN-图算法] | Graph Convolutional Networks for Text Classification | 将GCN应用于文本分类中,在不引入预训练模型的情况下,该方法的表现已经很优异了。该方法将每个独立的单词以及文档作为节点,即graph中包含单词级别和文档级别两类节点。初始化单词one-hot(不使用训练向量)。对于边,则包含(文档-单词)、(单词-单词)两类边,其中(文档-单词)使用tf-idf进行度量,(单词-单词)使用PMI指数。本文的模型结构的缺点在于,只考虑到共现度方面的信息,因此语义方面很低(作者原意就是不使用预训练embedding),而且可能会受到长尾问题的影响,因此可以使用注意力来辅助提升| Liang Yao et al, 2018
[语音系统-语音合成] | Neural Speech Synthesis with Transformer Network | 阅读笔记| 本文受Transformer启发,使用多头自注意力机制取代Tacotron2中的RNN结构和原始注意力机制。 | Naihan et al,2018
[预训练-语言模型] | BERT: Pre-training of Deep Bidirectional Transformers for Language Understanding | 阅读笔记| 顶顶大名的BERT,单独抽离Transformer的Encoder架构,并提出NSP、MLM预训练方式,也是基于此,是的BERT拥有强大的表征能力,并用于下游相关任务| Devlin et al,2018
[深度学习] | RelGAN: Relational Generative Adversarial Networks For Text Generation | 阅读笔记| 提出了新型的生成器和判别器结构,使得直接用Gumbel Softmax训练出的文本GAN大幅度超过了以往的各种文本GAN模型。主要由三个模块组成,分别是:在生成器上,利用relational memory,使得具有更强表达能力和在长文本上更好的模型能力;在离散数据上,训练GAN利用Gumbel-Softmax Relaxation模型,使得模型简化,替代强化学习启发式算法;在判别器上利用多层词向量表示,使得生成器往更具多样性方面更新Weili Nie et al, 2019
[异常检测-综述] | Deep Learning for Anomaly Detection: A Review | 阅读笔记| 本篇综述将异常检测归纳到三个框架(deep learning generic feature extraction、learning representations of normality、end-to-end anomaly score learning),共十一种类别中,并对每个类别的目标、流程、优缺点等进行了详细的阐述。最后给出了代表性的算法和数据集,并分析了当下和未来的发展方向,是一篇非常值得一读的异常检测综述| Guansong Pang et al, 2019
[机器学习] | Covariate Shift: A Review and Analysis on Classifiers | 阅读笔记| 通过几种分类算法,在四种不同的数据集下验证几种方法处理Covariate Shift问题后的性能分析| Geeta et al, 2019
[深度学习] | Language Models as Knowledge Bases? | 阅读笔记| 一篇讨论性的文章,主要提出的观点是认为像BERT等类似的预训练语言模型是另一种形式的knowledge database,能够保存大量的知识信息。作者通过效仿MLM的方式,将已有的NLP数据集进行整合,并挖空成完形填空的提问形式(以推理实体关系),文中实验了两种单向语言模型和两种双向语言模型,结果显示预训练模型的确包含了知识库中的信息。ps:这种观点也不一定对的,也有文章反对说BERT等模型只是由于对实体名称(表面形式)进行推理,如果过滤掉一些容易猜测的事实,那么模型精度将会急剧下降| Fabio Petroni et al, 2019
[深度学习-预训练] | What does BERT learn about the structure of language? | 阅读笔记| 本文主要是通过一些实验来补充验证BERT的不同层学习到的信息(具体没啥新结论,只是补充验证而已)。BERT的底层学习到的主要是token的表层信息,中层学习到的是语言学特征信息(句法结构之类的),顶层学习到的是语义特征信息。文中还进一步探索了BERT能够学习到组合结构的特征,使用了Tensor Product Decomposition Networks(TPDN)来设计实验,从自注意力机制的权重中推导出对应的依赖树,印证了BERT的组合建模方式和传统的句法分析相似| Ganesh Jawahar et al,2019
[模型] | Pay Less Attention With Lightweight And Dynamic Convolutions | 阅读笔记| 论文研究Lightweight、Dynamic Convolutions,卷积结构同样能够达到和Self-Attention媲美的效果| Felix Wu et al,2019
[蒸馏-预训练-语言模型] | Distilling Task-Specific Knowledge from BERT into Simple Neural Networks | 阅读笔记| 对BERT进行蒸馏,训练一个TextCNN模型,相比于直接使用BERT,TextCNN虽然有一定的损失,但是参数量和速度都大大提升。本文在知识蒸馏的方式上没有特别的创新,核心点在于(1)添加了额外的逻辑回归的目标,在标注数据下,hard label的交叉熵+teacher 模型的logits的MSE;在无标注数据下,teacher模型的softlabel的交叉熵+teacher模型的logits的MSE(2)数据增强,提出了多种方法;随机mask一个token;pos tag替换;n-gram sampling;mask_prob,执行mask增强,mask_prob << pos_prob,执行pos替换,最后执行n-gram sampling | Raphael Tang et al,2019
[深度学习] | On the Convergence of Adam and Beyond | 原英文版阅读笔记| 阅读笔记| Amsgrad,ICLR2018的最佳论文,主要是算法证明Adam在收敛性上存在的缺陷,并设计了理论实验,证明了这一点,同时提出了很简单的优化方法(实际的算法实现中,这个优化方法在相当多的实验中效果并不好)。Adam的收敛性缺陷在于,学习率通常是恒定的或降低的,所以随着训练过程的进行,二阶动量会随之减少,所以具体做法是增加一个变量来记录最大值,使用这个二阶动量的最大值替换原来的二阶动量进行计算,即v = max(avg_squared, max_squared) | Sashank J. Reddi et al, 2019
[预训练-语言模型-文本相似度/匹配/分类] | Poly-encoders: Transformer Architectures and Pre-training Strategies for Fast and Accurate Multi-sentence Scoring | 阅读笔记| Poly-encoder主要的出发点就是想要保持Bi-encoder的推理速度的同时,兼顾Cross-encoder精准匹配的潜力。思想上比较好理解,Bi-encoder的主要问题在于它要求encoder将query的所有信息都塞进一个固定的比较general的向量中,而Cross-encoder为了得到更加均衡的语义表示,需要将句子对关联起来进行推理计算,导致在检索时速度极慢。因此Poly-encoder的方案就是每个query产生m个不同的vec,利用这m个vec动态的和candidate vec计算,得到最终的final_vec(作为query的最终表示),用final_vec和candidate vec进行计算得到分数| Samuel Humeau et al,2019
[预训练-语言模型-文本相似度/匹配/分类] | How to Fine-Tune BERT for Text Classification? | 阅读笔记| BERT在Text Classification上的一些微调实验| Xipeng Qiu et al,2019
[预训练-对话系统] | Pretraining Methods for Dialog Context Representation Learning | 阅读笔记| 作者列举了四种针对对话上下文表示的预训练方法,其中两种是作者新提出的| Shikib et al,2019
[深度学习] | Scheduled Sampling for Transformers | 阅读笔记| 在Transformer应用Scheduled Sampling | Mihaylova et al,2019
[预训练-语言模型] | XLNet: Generalized Autoregressive Pretraining for Language Understanding | 阅读笔记| XLNet--自回归语言模型的复兴,30多项任务超越BERT | Zhilin Yang et al,2019
[机器学习] | Monte Carlo Gradient Estimation in Machine Learning | 阅读笔记| 本文是一篇关于Monte Carlo gradient estimation的survey,本文主要总结的内容是:随机梯度估计方法的相关背景知识,包括蒙特卡洛采样和随机优化;几种经典应用,包括变分推断、强化学习中的Policy gradient、敏感性分析、实验设计;两类经典的梯度估计算法| Shakir Mohamed et al,2019
[预训练-语言模型] | RoBERTa: A Robustly Optimized BERT Pretraining Approach | 论文发现原BERT的预训练并不充分,因此作者提出了四点Bert的改进:1):使用更大的batch在更大的数据集上对Bert进行深度训练;2):不在使用NSP(Next Sentence Prediction)任务;3):使用更长的序列进行训练;4):动态改变训练数据的MASK模式;其中动态MASK就是在每次数据输入的时候进行MASK,而不是在数据预处理的时候就预先MASK好,这种方式相当于不重复看数据,使模型学习到更多的pattern | Yinhan Liu et al,2019
[模型-文本相似度/匹配/分类] | Simple and Effective Text Matching with Richer Alignment Features | 阅读笔记| 本文模型主打的是参数少,推理速度快(实际复现也确实很快,效果也不错)。模型的结果不复杂,采用对称结构,使用Encoder、Alignment、Fusion三个模块组成的block(模型是多block结构)进行Representation,其核心应该是对于网络中三个向量的使用,residual vectors, embedding vectors 和encoded vectors。全文的模型结构不复杂,效果不错,值得一试的模型| Runqi Yang et al,2019
[预训练-语言模型-文本相似度/匹配/分类] | Sentence-BERT: Sentence Embeddings using Siamese BERT-Networks | 阅读笔记| 和之前提出的InferSent结构如出一辙,妥妥的双塔结构,只是换成了Bert来进行特征表示。模型结构没有什么创新点,但是这个结构用起来效果挺好,速度也快,很适合工业界使用。论文中在针对句向量表示计算策略分别使用了CLS向量策略、平均池化策略、最大值池化策略三个策略进行实验,实验结果中平均池化策略最优| Nils Reimers et al,2019
[对话系统-数据增强] | Data Augmentation with Atomic Templates for Spoken Language Understanding | 使用Atomic Templates(act-slot-value)进行对话数据增强,使用seq2seq生成模型进行语句生成| Zijian Zhao et al,2019
[预训练-语言模型] | NEZHA: Neural Contextualized Representation For Chinese Language Understanding | 阅读笔记| 具体来说没有啥特别的创新点吧,在位置编码部分改成了相对位置编码。其他的比如WWM、混合精度训练、优化器自适应学习率,都是屡见不鲜的东西,整体效果而言也没有令人惊艳| Junqiu Wei et al,2019
[预训练-语言模型] | CTRL: A Conditional Transformer Language Model For Controllable Generation | 阅读笔记| CTRL语言模型,提供Control Code进行定向文本生成,相较于GPT可对文本风格进行控制| Keskar et al,2019
[语音系统] | A Comparative Study on Transformer vs RNN in Speech Applications | 阅读笔记| Transformer应用在语音领域上与RNN对比的论文,并在ESPnet上面开源了模型代码| Nanxin et al,2019
[蒸馏-预训练-语言模型] | TinyBERT: Distilling BERT for Natural Language Understanding | 阅读笔记| 本文提出的TinyBERT模型大小只有BERT的13.3%,推理速度是BERT的9倍,效果下降了2-3个点左右。具体细节分为基础蒸馏:(1)Embedding蒸馏,先用权重矩阵转换一下T模型的Embedding,然后在计算两个模型的Embedding的MSE loss(2)attention层蒸馏,计算S模型和T模型的单个头Attention的MSE loss;(3)hidden层蒸馏,同Embedding的蒸馏方式,先用权重矩阵转换一下;(4)Prediction层蒸馏,计算T模型输出的logits和S模型输出logits的交叉熵,加一个temperature控制平滑。在训练的时候,分成了两段式学习框架,包含通用蒸馏和特定于任务的蒸馏,就是分别在通用语料和在下游任务语料上分别蒸馏| Xiaoqi Jiao et al,2019
[预训练-语言模型] | ALBERT: A Lite BERT For Self-superpised Learning Of Language Representations | 阅读笔记| Albert大大缩小了模型参数量,并且加快了训练速度,增加了模型效果。其主要对BERT做了3点改进,第一:把embedding size(E)和hidden size(H)分开可以更高效地利用参数,因为理论上存储了context信息的H要远大于E。第二:跨层参数共享,就是不管12层还是24层都只用一个transformer。第三:使用Inter-sentence coherence loss,即SOP(sentence order prediction) | Zhenzhong Lan et al,2019
[蒸馏-预训练-语言模型] | DistilBERT, a distilled version of BERT: smaller, faster, cheaper and lighter | 阅读笔记| 本文提出的DistilBERT,相比BERT减少40%大小,保持了97%的精度,快了60%,结果还是很棒的。DistilBERT实在预训练阶段进行蒸馏:(1)S模型结构方面,和原始BERT保持一致,token-type和pooler去掉了,然后block layer数量只有T模型的一般(两层蒸一层);(2)在损失设计方面,分为原语言模型的loss(MLM)+蒸馏loss(就是T和S输出的logits的交叉熵)+cos距离loss(T和S在block layer间的hidden对齐)。一些小tricks方面,S模型的初始化选自T模型每两层中的一层;Batch size竟可能的大;引用RoBERTa的优化策略,动态mask | Victor SANH et al,2019
[对话系统-对话意图识别-数据增强] | A Closer Look At Feature Space Data Augmentation For Few-Shot Intent Classification | 针对SLU的Intent分类任务,对其文本数据进行数据增强并比较效果,其中Linear+Transfer learning效果最佳| Varun Kumar et al,2019
[异常检测-半监督] | Deep Weakly-supervised Anomaly Detection | 阅读笔记| 本文提出的PReNet或PRO模型结构上不复杂,通过双塔结构的全连接层(也可以是其他的特征表示层)融合特征,最后通过全连接层缩放维度输出回归分数。本文主要在于对标签数据的组合训练策略,即成对关系预测任务。通过对带标签的异常样本和未带标签的样本进行组合,构成三个类型:两个样本都是已知的异常样本(标签为较大的分值8)、两个样本都是未标记的样本(可能是正常样本,也可能是未知的异常样本,标签为较小的分值0)、两个样本中一个是已知异常样本另一个是未标记样本(标签为中等的分值4)。通过这样做,预测值可以被定义为这些样本对的异常分数,并使用MAE进行训练。预测时,分别从标记异常数据和未标记数据中随机取等量样本,和预测样本进行计算分数| Guansong Pang et al, 2019
[预训练-语言模型] | CogLTX: Applying BERT to Long Texts | 本文主要介绍如何优雅且有效的的使用BERT处理长文本。一般用BERT处理长文本的方式有截断法、Pooling法、压缩法,本文介绍的就是压缩法的一种(三种效果最好的)。从直观的角度来讲,长文本中的核心语义可以由某个短文本替换(相当于长句总结),因此需要找到这个短文本。具体的做法就是(1)首先使用动态规划算法将长文本划分长文本块;(2)然后使用一个叫做MemRecall的模块对这些块进行打分(本质上是concat),从而选出分数最高的子句组成短文本;(3)然后再用这个短文本用于后续的NLP任务。总结来讲就是COGLTX相当于使用了了两个bert,MemRecall中bert就是负责打分,另一个bert执行原本的NLP任务| Ming Ding et al,2020
[数据集] | Improving Dialog Evaluation with a Multi-reference Adversarial Dataset and Large Scale Pretraining | 数据集地址| DailyDialog数据集的升级版,11K的多轮对话上下文,每个上下文包括五个标准的参考回复、五个不相关的回复、五个随机挑选的回复| Ananya B. Sai et al, 2020
[模型-预训练] | Reformer: The Efficient Transformer | 阅读笔记| 使用LSH Attention、Reversible layers、Chunking FFN layers,降低Transformer计算复杂度和内存空间消耗| Nikita Kitaev et al,2020
[Prompt-预训练-语言模型-文本相似度/匹配/分类] | Exploiting Cloze Questions for Few Shot Text Classification and Natural Language Inference | 比较早研究Prompt的工作之一,PET使用了基于手工设计模板的Prompt进行训练,对无标签数据使用了简单的prompt ensemble,即将多种prompt集成在一起计算预测结果,按不同pattern的模型acc对应权重对所有的预测进行归一化,作为soft label蒸馏一个最终模型。PET在计算loss的时候主要计算目标词的cross entropy(MLM loss作为附加,Loss=(1-a) L_CE+a L_MLM),而忽略了词表中其他备选词,这种方式在后续的工作当中是被认为不妥的,还是使用原生的MLM loss更好。论文还在PET的基础上,提出了迭代式的PET训练,即iPET。其实就是进行多代交叉的蒸馏,随机选取每一代的模型为无标签数据进行标记,并基于此进一步训练下一代的模型,最终和PET一样,用不同模型标注的无标签数据进行预测,蒸馏一个统一的模型。PET这种手动设计Prompt的方式本身难度较大,而且是基于人为经验的,这种方式使得模型比较依赖prompt,导致稍加改动就影响模型性能,因此后续工作也朝着auto prompt方向发展| Timo Schick et al,2020
[深度学习] | Consistency of a Recurrent Language Model With Respect to Incomplete Decoding | 阅读笔记| 讨论Seq2Seq模型解码停不下来的原因| Sean Welleck et al,2020
[深度学习] | GLU Variants Improve Transformer | 本文借助门控线性单元(Gated Linear Unit,GLU)对模型的FeedForward层进行了修改,同时在训练的时候去掉了Dropout,并增加了解码器输出端的Embedding(这些改动增加了模型参数,但效果更佳)。文中主要对比了Bilinear、relu、gelu、swish激活函数下,使用GLU的效果,其中gelu和swish表现最佳。总得来说,实验证明了GLU的有效性,可以应用在模型里试试| Noam Shazeer et al,2020
[数据集] | CrossWOZ: A Large-Scale Chinese Cross-Domain Task-Oriented Dialogue Dataset | 阅读笔记| 第一个大规模的中文跨域任务导向对话数据集| Qi Zhu et al,2020
[综述-对话系统-任务型对话] | Recent Advances and Challenges in Task-oriented Dialog Systems | 阅读笔记| 面向任务型对话系统的最新研究和方向| Zhang et al,2020
[深度学习] | PowerNorm: Rethinking Batch Normalization in Transformers | 对于Transformer中BN表现不好的原因做了一定的empirical和theoretical的分析| Sheng Shen et al,2020
[综述-预训练] | Pre-trained Models for Natural Language Processing: A Survey | 阅读笔记| 超详细的NLP预训练语言模型总结清单| Xipeng Qiu et al,2020
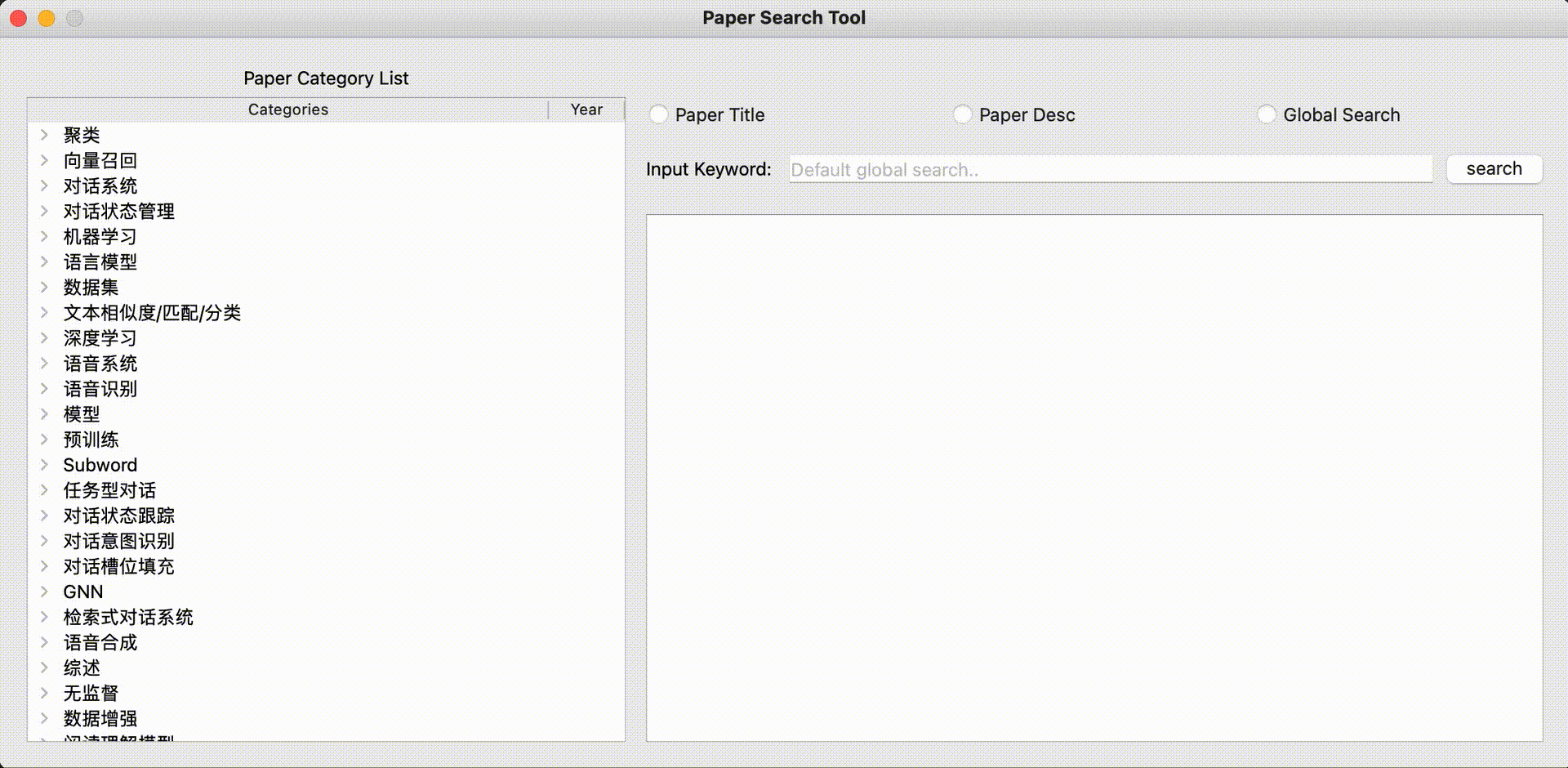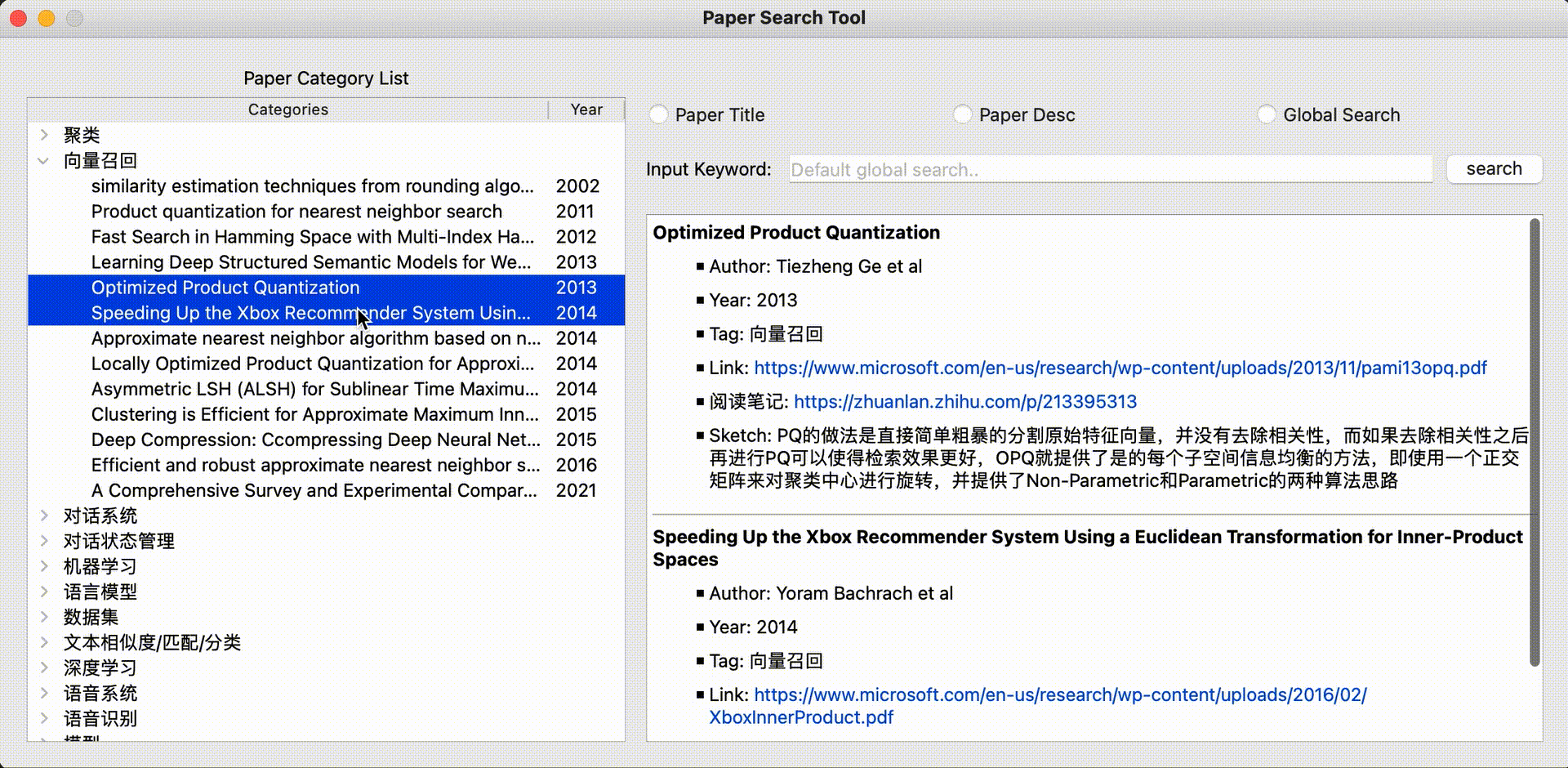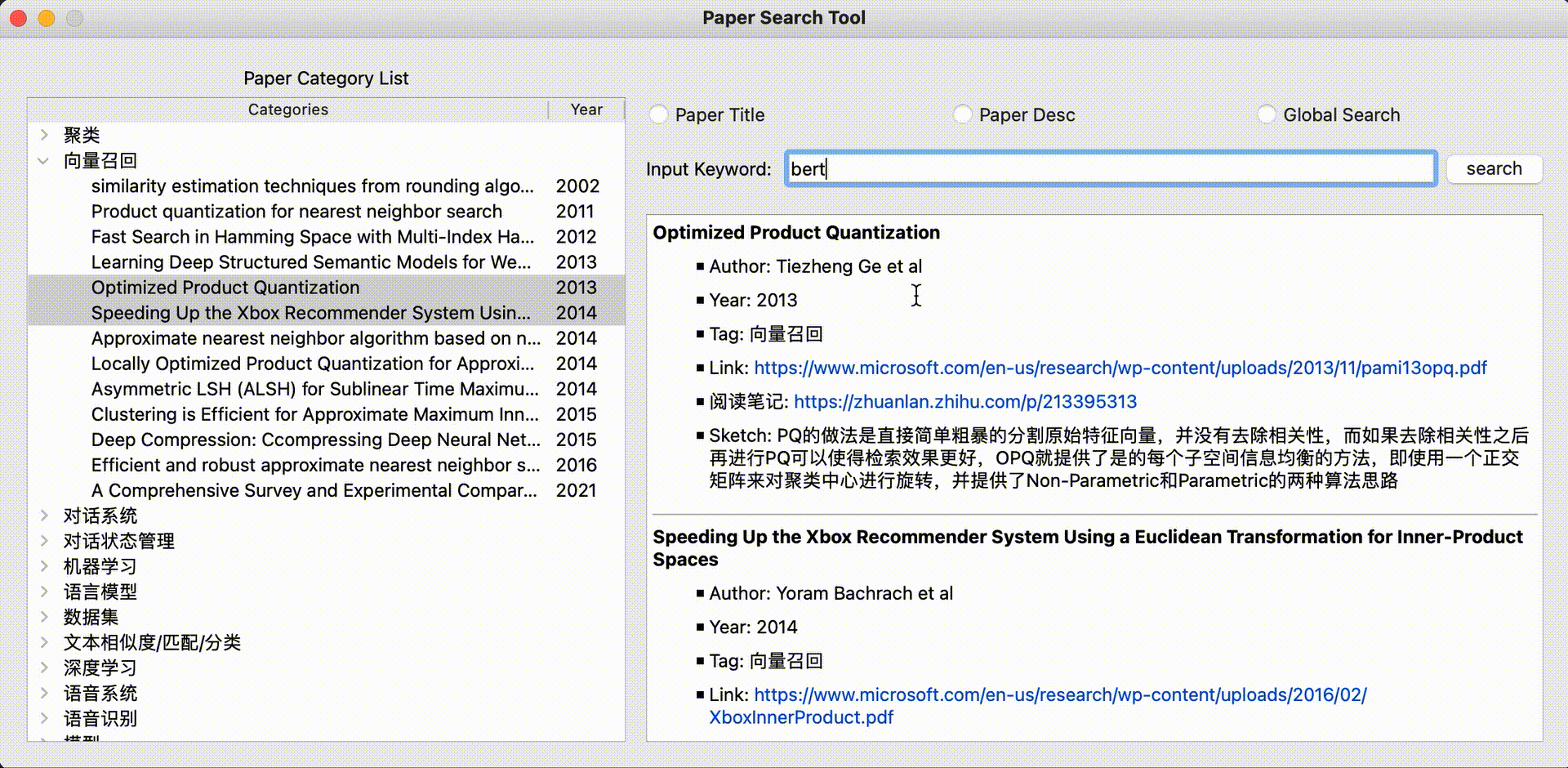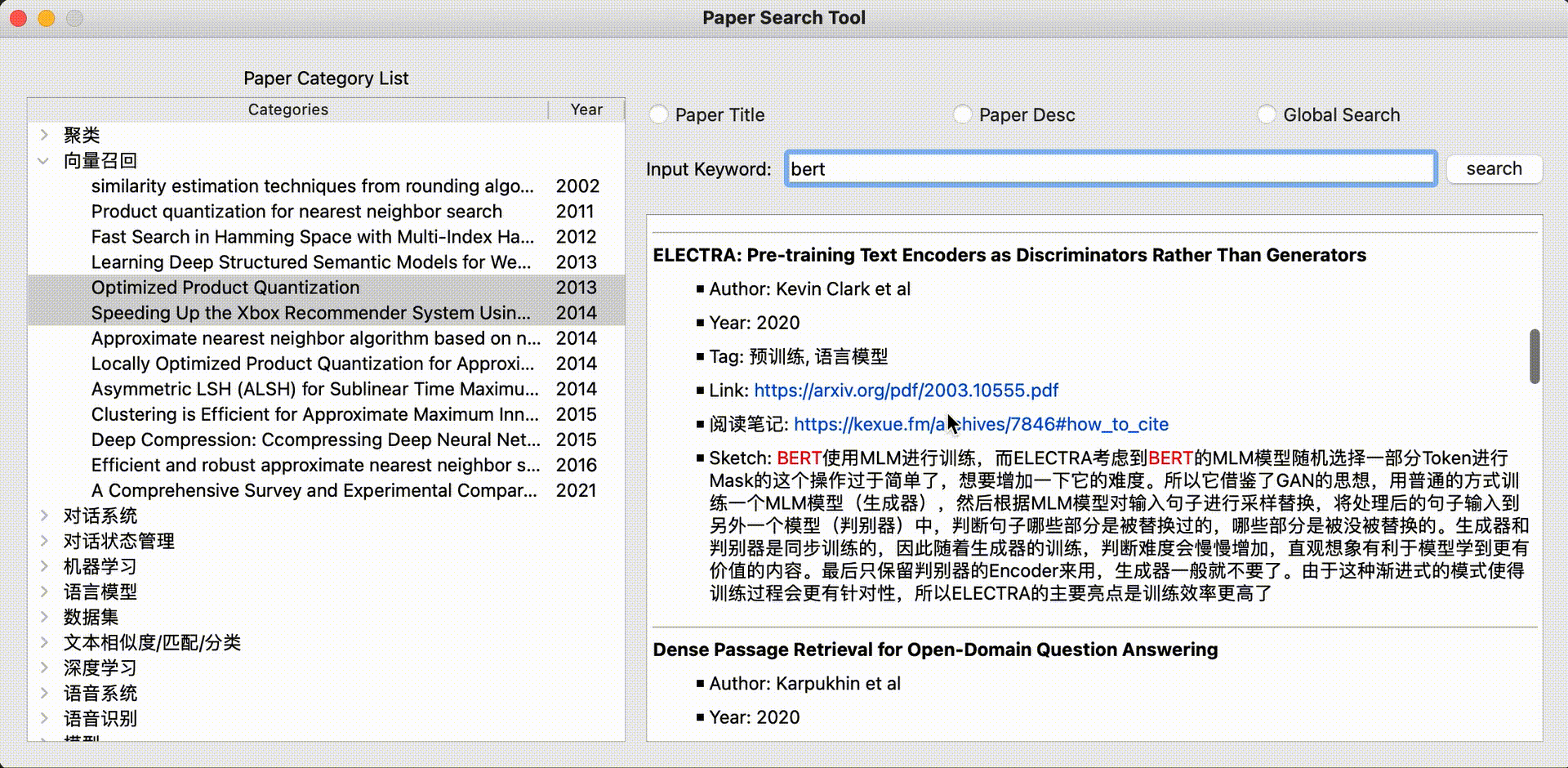
[预训练-语言模型] | ELECTRA: Pre-training Text Encoders as Discriminators Rather Than Generators | 阅读笔记| BERT使用MLM进行训练,而ELECTRA考虑到BERT的MLM模型随机选择一部分Token进行Mask的这个操作过于简单了,想要增加一下它的难度。所以它借鉴了GAN的思想,用普通的方式训练一个MLM模型(生成器),然后根据MLM模型对输入句子进行采样替换,将处理后的句子输入到另外一个模型(判别器)中,判断句子哪些部分是被替换过的,哪些部分是被没被替换的。生成器和判别器是同步训练的,因此随着生成器的训练,判断难度会慢慢增加,直观想象有利于模型学到更有价值的内容。最后只保留判别器的Encoder来用,生成器一般就不要了。由于这种渐进式的模式使得训练过程会更有针对性,所以ELECTRA的主要亮点是训练效率更高了| Kevin Clark et al,2020
[数据集] | MuTual: A Dataset for Multi-Turn Dialogue Reasoning | 阅读笔记| MuTual 数据集,用于针对性地评测模型在多轮对话中的推理能力| L Cui et al,2020
[对话系统-检索式对话系统] | Dense Passage Retrieval for Open-Domain Question Answering | 阅读笔记| DPR一种高效的开放域问答检索技术,应用了BERT进行编码| Karpukhin et al,2020
[预训练-语言模型-对话系统-任务型对话] | TOD-BERT: Pre-trained Natural Language Understanding for Task-Oriented Dialogue | 阅读笔记| 任务导向型对话的预训练自然语言理解模型| Chien-Sheng Wu et al,2020
[深度学习] | Shortcut Learning in Deep Neural Networks | 阅读笔记| 对Shortcut Learning问题进行比较详细的解释和剖析,虽然最后没有给出实际的解决方案(Shortcut Learning问题本身就没有一个体系化的策略,需要根据实际任务而定),不过提供了几种解决的视角| Robert Geirhos et al,2020
[预训练-语言模型-文本相似度/匹配/分类] | ColBERT: Efficient and Effective Passage Search via Contextualized Late Interaction over BERT | 阅读笔记| 和前面的Poly-encoder出发点都是一样的,为了就是在获得BERT representation能力的同时,提高文本计算的效率。按照本文的说法,就是尽可能离线计算好Embedding,在通过Late Interaction的方式,弥补因为query和doc分离计算导致的效果损失。本文具体的模型结构是使用原生的BERT,对query和doc进行Embedding,不同之处是为了区分query和doc,分别在输入的seq的起始位置加上[Q]和[D]。Bert是编码器,CNN做维度变换,用来对BERT的隐层输出进行降维处理,Normalize是为后面计算余弦相似度做l2正则化处理,对于doc加个标点符号的mask | Omar Khattab et al,2020
[综述-文本相似度/匹配/分类] | Evolution of Semantic Similarity - A Survey | 阅读笔记| 一篇语义相似度的综述,整体文章从数据集开始,将技术体系分为:基于知识的语义相似性方法、基于语料的语义相似性方法、基于深度神经网络的方法、基于混合模型方法四类进行分析| Dhivya Chandrasekaran et al,2020
[模型-预训练-语言模型] | Synthesizer: Rethinking Self-Attention for Transformer Models | 阅读笔记| 在Transformer架构下,对Self-Attention计算的探索研究,看完会对Self-Attention有个新认识| Yi Tay et al,2020
[综述-文本相似度/匹配/分类] | Measurement of Text Similarity: A Survey | 语义相似度的综述,大体上从独立度量到模型计算的模型概述的比较广,但不是很全,不过从了解相似度计算来讲,还是值得一看的| Jiapeng Wang et al,2020
[深度学习] | Beyond Accuracy: Behavioral Testing of NLP Models with CheckList | 阅读笔记| ACL2020的Best Paper,基于NLP领域提出了测试体系来指导我们了解NLP 模型的能力,也能够指导我们去理解问题、解决问题。不同于现代NLP 模型常常仅关注特定的任务,CheckList 希望去评估一个模型的多方面能力,这些能力有的是模型通用的,有的则是面向特定的任务或领域| Marco Tulio Ribeiro et al,2020
[预训练-语言模型] | DeBERTa: Decoding-Enhanced Bert With Disentangled Attention | 阅读笔记| DeBERTa的一大亮点在于改动位置编码的介入时机,在论文中叫作Disentangled Attention。具体做法是将原本和输入embedding混合相加的pos embedding(relative)单独拎出来,然后再用位置编码和content 编码计算attention,进而增加了“位置-内容” 和“内容-位置” 注意力的分散Disentangled Attention。然后一些其他的改动比如:1) | 因为我们在精调时一般会在BERT 的输出后接一个特定任务的Decoder,但是在预训练时却并没有这个Decoder,所以本文在预训练时用一个两层的Transformer decoder 和一个SoftMax 作为Decoder;2) | 为了弥补一下只有相对位置的损失,因此在decoder前加入一层绝对位置embedding;3) | bert的训练策略中,mask有10%的情况是不做任何替换,而DeBeta将不做替换改成了换位该位置词绝对位置的pos embeding | Pengcheng He et al,2020
[对话系统-阅读理解模型-检索式对话系统] | Leveraging Passage Retrieval with Generative Models for Open Domain Question Answering | Fusion-in-Decoder生成式阅读理解模型| Izacard et al,2020
[数据集] | MultiWOZ 2.2: A Dialogue Dataset with Additional Annotation Corrections and State Tracking Baselines | 阅读笔记| MultiWOZ是一个著名的面向任务的对话数据集,被广泛用作对话状态跟踪的基准,MultiWOZ 2.2是目前最新版本| Zang et al,2020
[预训练-语言模型] | Glancing Transformer for Non-Autoregressive Neural Machine Translation | 阅读笔记| 本文提出的GLAT是一种Non-Autoregressive翻译模型(摆脱BeamSearch),主要着重于并行化Decoder以及提高翻译质量,实际的效果速度快且在一些翻译方向上(英德)达到了SOTA。模型的核心结构沿用Transformer结构,参考预训练语言模型的MLM的做法,提出一种叫作GLM(Glancing LM)的方案,即使用两遍Decoder(同一个Decoder),第一遍的Decoder中,不加任何干预的获得模型的自然输出,这个时候将输出与Gold output进行对比,然后随机采样(也可以尝试其他的)目标词的词嵌入替换模型输出对应的hidden,然后再次喂入Decoder得到最终输出(注意,这里采样的词数量是根据训练情况好坏反比的,模型输出效果越好,采样的目标词越少,最终模型收敛到一次并行推理)。原理就是在第一次并行推理比较难学习到词与词之间的依赖关系,因此在第二次并行推理时,适当的引入目标词进行修正,进行增强训练| Lihua Qian et al,2020
[异常检测-模型-机器学习-无监督] | COPOD: Copula-Based Outlier Detection | 阅读笔记| 本文主要是基于copula统计概率函数,提出了COPOD的异常检测方法,COPOD使用了非参数(non-parametric)的方法,通过经验累积分布(Empirical CDF)来得到empirical copula,在这之后我们就可以简单的通过empirical copula来估算所有维度上的联合分布的尾端概率。因此COPOD不需要进行样本间的距离计算,从而节省运行开销且速度快,同时,该方法不需要调参,直接使用即可| Zheng Li et al, 2020
[预训练-语言模型-关系抽取] | A Frustratingly Easy Approach for Entity and Relation Extraction | 阅读笔记| 提出了一种非常简单的方法,该方法可以学习基于深度预训练语言模型构建的两个编码器,这两个模型分别被称为实体模型和关系模型(实体模型和关系模型的语境表示本质上捕获了不同的信息,因此共享其表示会损害性能)。同时,为了加快模型推断速度,该研究提出了一种新颖而有效的近似方法,该方法可实现8-16 倍的推断加速,而准确率只有很小的降低| Zexuan Zhong et al,2020
[预训练-语言模型-Prompt] | AutoPrompt: Eliciting Knowledge from Language Models with Automatically Generated Prompts | 阅读笔记| 本篇论文提出一种基于梯度的prompt搜索方案,方法比较直观,将通过梯度找出trigger word和mask拼接在文本中,形成一个语义上不通顺,但是对模型而言却具有合理prompt的样本,并且将label预测转换为masked token的预测。方法的核心在于选取trigger word,说白了就是选定一个已确定token数量的template,比如论文中{sentence}[T][T][T][T][T][P],其中T就代表trigger word,P代表label,在这个例子中,准备使用五个token作为prompt,做法就是将这五个token标识为mask token,然后通过MLM的方式预测出token,然后选前k个最大化输入与梯度乘积的token,选出的token候选一次加入到prompt并评估预测的概率。在预测prompt token之外,还拿了mask token的hidden states过一个线性层预测label,并加上原本label位置mask token的loss进行训练。AutoPrompt的方法总的来说简单粗暴,不过带来的也是可解释性差,具体效果一般| Taylor Shin et al,2020
[预训练-语言模型] | Informer: Beyond Efficient Transformer for Long Sequence Time-Series Forecasting | 阅读笔记| 一种效果远超Transformer的长序列预测模型,针对LSTF问题上的研究改进| Haoyi Zhou et al,2020
[综述-可解释性] | A Survey on Neural Network Interpretability | 阅读笔记| 关于神经网络可解释性的一篇综述,整理的挺不错的,不过就是相关领域前沿探索不足| Yu Zhang et al,2020
[深度学习] | A Theoretical Analysis of the Repetition Problem in Text Generation | 阅读笔记| 讨论Seq2Seq模型解码重复生成的原因| Zihao Fu et al,2020
[预训练-语言模型-Prompt] | Making Pre-trained Language Models Better Few-shot Learners | 阅读笔记| 文中提出的LM-BFF是一套简单的技术组合,用于仅在少量训练样本上对预训练的LM进行微调,其中包括:(1)基于Prompt的微调以及自动生成prompt的新方法;(2)一种动态的、有选择的在上下文中引入demonstration的方法。这里稍微介绍一下背景概念,Prompt方法主要分两种不同的研究方向:(1)基于prompt的fine-tuning(被认为是更适合小LM的few-shot learner);(2)而对于大模型,fine-tuning比较困难,因此是希望固定他们的参数,通过不同的prompt将它们应用在不同的任务上。对于第二个研究方向,prompt分为Discrete Prompts和Soft Prompts,可以简单的认为discrete是选随机token,而soft则是直接用随机向量替换Embedding。然后还有除了Prompt之外,还有demonstration(in-context learning, 一种新的meta-learning方式),prompt和demonstration都是GPT-3很成功的设计,demonstration是多sample+input text作为模型输入,其中也有很多优化的方法| Tianyu Gao et al,2020
[对话系统-预训练-检索式对话系统] | Distilling Knowledge From Reader To Retriever For Question Answering | 阅读笔记| 一种模型训练模型的开放域问答方法| Izacard et al,2021
[预训练-语言模型-Prompt] | Prefix-Tuning: Optimizing Continuous Prompts for Generation | 阅读笔记| 本篇论文核心是针对离散的Prompt难以优化的问题,提出了参数化的prompt,仅微调prompt,freeze住LM。在小样本任务重,这种方法极大的减小的模型的参数,减少了过拟合的风险,这种参数化的prompt在小样本场景中,能够优于fine-tune的方法。这篇文章的做法和P-tuning差不多,都是设计了非自然语言的模板,只不过Prefix-tuning主要关心的是NLG的应用,而P-tuning更加关心NLU的应用| Xiang Lisa Li et al,2021
[综述-向量召回] | A Comprehensive Survey and Experimental Comparison of Graph-Based Approximate Nearest Neighbor Search | 阅读笔记| 论文是一篇关于graph-base的向量召回综述,聚焦实现了效率和精度最优权衡的近邻图索引,综述了13 种具有代表性相关算法,包括NSW、HNSW等在内的优秀算法,并提出一个统一评估的pipeline | Mengzhao Wang et al,2021
[预训练-评估] | LogME: Practical Assessment of Pre-trained Models for Transfer Learning | 阅读笔记| 一种通用且快速的评估选择适合下游任务的预训练模型的打分方法,logME | Kaichao You et al,2021
[Prompt-预训练-语言模型] | GPT Understands, Too | 阅读笔记| 在本文之前的Prompt思路呢,要么是通过人工设计Prompt(如PET),要么是探索通过自动化搜索Prompt进行(如AutoPrompt、LM-BFF等),思路都限于搜索token来组成Prompt template(Discrete Prompt Search),而本文提出的P-tuning思路是不用关心template由哪些token word组成,对于模型而言,只需要token embedding,直观点说就是在template中,除了目标词正常以Mask token出现,prompt token则是[unused*](也就是从未见过的token来构成模板,这里的token会过一层LSTM进行编码),其中token数目是一个超参数可以调整,这种方式极大的提升了template的搜索空间(连续)。小样本的时候固定模型权重,只优化[unused*]的Embedding,这样即使样本少也能学到prompt template,不容易过拟合。标注数据足够的话就直接放开所有权重一同训练微调就行| Xiao Liu et al,2021
[Prompt-预训练-语言模型] | The Power of Scale for Parameter-Efficient Prompt Tuning | 阅读笔记| 本文的方法和p-tuning相似,是固定LM,只训练prefix,这篇文章主要是验证了全量数据情况下,仅微调prompt相关的参数,能够达到fine-tune的效果(p-tuning的prompt token人为的选用[unused*],而本文对prompt token的初始化分两种:置零和采用词表的一些预训练token embedding)。论文的最终结论有:1):在一般模型大小的情况下,prompt token越多,效果越好(超过20增益减小),但是在超大模型的情况下,单个prompt token也能达到前面20个token以上的效果;2):随机初始化、词表采样、用label标签初始化,其中label的方式效果最好;3):LM Adaptation steps 越多,效果越好;4):同时训练多个prompt进行ensemble,效果优于单一prompt | Brian Lester et al,2021
[预训练-语言模型-文本相似度/匹配/分类] | SimCSE: Simple Contrastive Learning of Sentence Embeddings | 阅读笔记| 基于Sentence-Bert,引入对比学习的思想,在无监督与有监督语义相似度计算任务达到SOTA。主要围绕对比学习质量指标Alignment和Uniformity来进行优化,对于Unsupervised,核心是使用dropout mask生成正样本,负样本是in-batch negatives。而Supervised则是NLI中entailment关系样例对。负例:a) in-batch negatives b)NLI中关系为contradiction的样例对| Tianyu Gao et al,2021
[预训练-语言模型] | Are Pre-trained Convolutions Better than Pre-trained Transformers? | 阅读笔记| 将Transformer的Attention换成了卷积,尝试预训练模型新方式| Yi Tay et al,2021
[综述-对话系统] | Recent Advances in Deep Learning Based Dialogue Systems: A Systematic Survey | 对话系统综述:新进展新前沿| JinJie Ni et al,2021
[对话系统-评估] | Towards Quantifiable Dialogue Coherence Evaluation | QuantiDCE,一种实现可量化的对话连贯性评估指标模型| Zheng Ye et al,2021
[对话系统-对话策略学习] | Retrieve & Memorize: Dialog Policy Learning with Multi-Action Memory | 阅读笔记| 联合检索和记忆块的多action的Dialog Policy Learning模型,在action生成和response生成上效果SOTA | Yunhao Li et al,2021
[对话系统] | Increasing Faithfulness in Knowledge-Grounded Dialogue with Controllable Features | 通过可控特征来增加知识对话系统的学习| Rashkin et al,2021
[综述-Prompt-预训练] | Pre-train, prompt, and predict: A systematic survey of prompting methods in natural language processing | 阅读笔记1 / 阅读笔记2 | 关于Prompt-based learning的一篇综述,Prompt(提示/题词)和之前的MLM有些相似,通过定义template的方式,基于语言模型的特性直接估计出文本的概率,从而生成答案。相较于传统的语言模型依赖于针对特定下游任务的fine-tune,Prompt更加关注模型的迁移能力(它的目标就是希望对不同下游任务建立一个统一的范例),除了便捷和泛化能力之外,这样做的一个明显优势就是不同任务之间的数据可以共享,减少标注数据,随着数据累积,新的任务可以达到zero-shot learning的目的| Pengfei Liu et al,2021
[文本相似度/匹配/分类-Prompt-预训练-语言模型] | Noisy Channel Language Model Prompting for Few-Shot Text Classification | 本篇论文以实验探索为主,含有大量的实验对比,主要出发点就是在few-shot问题中,探讨控制训练参数对于direct model和channel model效果的影响,最终的论文的结论是Noisy Channel model明显优于direct model。论文中的direct model主要是指一般的P(c|x),其中x是输入,c是label,而direct++ model则是基于direct,强化文本间的差异,引入空文本,即P(c|x)/P(c|null),而channel model则是指使用贝叶斯公式重新参数化direct,P(c|x)=P(x|c)P(c)/P(x),其中P(c)就是label数分之一,即P(1/C),而P(x)独立于c,所以最终只需要计算P(x|c)。那么最后用形象一点的例子来解释direct和channel的差异就是,direct=x->c,channel=c->x。论文中对参数的控制采用了all finetuning、head tuning、transformation tuning和Prompt tuning(这里可以认为是soft prompt,即只需在输入序列中放入一些随机向量,与词汇表中的特定word embedding无关,并进行调整,同时固定预训练模型的其他部分)。在direct和channel的方法间,channel明显优于direct。在direct model的参数控制实验中,head tuning是最优的,但是当channel model配合soft prompt时,效果是最好的| Sewon Min et al,2021
[对话系统-预训练] | General-Purpose Question-Answering with MACAW | 阅读笔记| 生成式多角度问答模型,参数量只有GPT-3的十六分之一,作者主打的亮点是通过整合7种不同的任务范式(问题生成、答案生成...),使得模型能够通过不同角度学习到QA相关的内容,目的就是得到一个强大的QA版本预训练模型。输入的话就是通过"$s1$;$s2$.."的slot方式进行文本拼接,得到的解码输出也是如此输出的,模型内核还是基于transformer的改造| Oyvind Tafjord et al,2021
[预训练-语言模型-Prompt] | PPT: Pre-trained Prompt Tuning for Few-shot Learning | 阅读笔记| 之前的工作都是在finetune阶段去使用prompt,这篇文章第一次提出了prompt pretraining的过程。一开始是因为观察了prompt tuning中的大模型尽管在全量数据下能够媲美finetune,但是在少样本情况下并不好,作者认为是因为在大模型上soft prompt对初始化很敏感,所以设计了一系列预训练的prompt task来给soft prompt提供一个很好的初始化。论文的结论是,通过prompt 的预训练,在少样本情况下,大模型的prompt tuning 同样能媲美fine-tuning 的效果| Yuxian Gu et al,2021
[对话系统-任务型对话-预训练] | Constraint based Knowledge Base Distillation in End-to-End Task Oriented Dialogs | 基于KB的End2End的Task-Oriented的对话系统,使用pairwise相似度过滤相关信息来获得KB中的n元结构,就这一点上倒没有什么新奇,只不过相对于之前的方式修改的entity格式。不过在避免检索到部分entity相似但并不是目标的record的情况,作者加入了辅助的损失函数用于embedding constraint,这种做法确实减少了相同entity之间的相似性,从而提高record的可靠性,值得借鉴。基于现有的F1指标的缺点,提出multiset entity F1 | Dinesh Raghu et al,2021
[综述] | Paradigm Shift in Natural Language Processing | 阅读笔记| 总结归纳NLP中任务范式并分析的综述,论文给出了七种范式的定义,针对此分析一些具体任务(范式迁移)的例子,并指出四种可能大一统的NLP任务范式:LM,matching,MRC,Seq2Seq(LM减少工程量,MRC具有更高的可解释性,seq2seq在处理复杂任务时具有更高的灵活性),但是没有把Prompt纳进去(狗头) | Tianxiang Sun et al,2021
[综述-数据增强] | Data Augmentation Approaches in Natural Language Processing: A Survey | 阅读笔记| 哈工大的工作,对15中NLP数据增强方法进行了总结和对比,有详细的优缺点说明,还有一些使用技巧,实用性非常强,需要的时候可以详细的参考原文以及相关的文献的应用细节。几个开源工具:Easy DA、UNsupervised DA、nlpaug、eda_nlp_for_Chinese | Bohan Li et al,2021
[预训练-语言模型-Prompt] | SPoT: Better Frozen Model Adaptation through Soft Prompt Transfer | 阅读笔记| 之前的工作证明了prompt 的初始化很重要,而在PPT(Pre-trained Prompt)那篇论文中提出的预训练方法能够给prompt 提供一个很好的初始化,但是有没有其他预训练的方式,比如不用设计预训练任务的,因此本文提出了一种prompt transfer(SPoT)的方法,即学习一个或者多个源任务的prompt 来初始化目标任务的prompt,这种方式能够使得prompt tuning 在不同模型尺寸(包括小模型)上都能媲美甚至优于fine-tuning(注意,无法超过multi-task fine-tuning 的效果)。论文的结论是在全量数据+ 仅微调prompt 的情况下,SPoT 能够在多个模型尺寸(包括小模型)下媲美和优于model tuning 的效果,并能在使用超大模型情况下媲美强基线Multi-task Tuning | Tu Vu et al,2021
[异常检测-模型-机器学习-无监督] | ECOD: Unsupervised Outlier Detection Using Empirical Cumulative Distribution Functions | 本文作者和2020年提出的COPOD算法同作者,本文提出的ECOD算法是COPOD算法的扩展版本。ECOD算法使用经验累计分布函数的无监督离群值检测,通过类似集成的方法(结合同一样本不同维度的离群分,假设各维度特征相互独立),计算每个样本的离群分,分值越高是异常值的可能性越大。另外,在计算各特征维度的左尾和右尾ECDF,并得到对应离群分后,通过skewness(偏度)来矫正集群分得到最终结果| Zheng Li et al, 2022
[预训练-语言模型-Prompt] | Rethinking the Role of Demonstrations: What Makes In-Context Learning Work? | 阅读笔记| 本文主要探讨分析Prompt范式下,预训练语言模型是如何学习并work的。主要的结论是在in-context learning 学习中,学习并不是输入与标注之间的关联,而是通过展示数据形式,来激活与训练模型的能力。此外附带两个结论:在meta learning环境下,in-context leanring的这个特点更为明显;因为标签不重要,所以可以用无标注领域内数据做in-context zero shot learning | Sewon Min et al,2022
[预训练-语言模型-文本相似度/匹配/分类] | How Different are Pre-trained Transformers for Text Ranking? | 阅读笔记| 本文主要对BERT(Cross-Encoder,即软匹配)和传统稀疏排序方法的BM25(精确匹配)进行query-doc排序结果的比较分析,尝试搞清楚Cross-Encoder和BM25的区别,弄清CE的运作原理。论文得到的结论就是:(1)精确匹配是一个重要的基础排序策略,而CE的软匹配能力是BM25不具备的;(2)对于高度相关的doc排序,CE和BM25各自的相关性定义有着很大的不同,且BM25明显低估了许多文档的相关性;(3)CE的潜力在于,它可以召回BM25非常不看好而实际却是高度相关的doc;(4)CE通过考虑上下文信息客服了对term匹配的依赖,能够找到“不可能相关”的结果,即语义泛化能力。从整个实验中也可以明显的看出CE和BM25各自都有着自己的优势,CE并不能完全替代BM25,不管是在召回还是在排序阶段,这两者依旧是相辅相成的关系(别忘了个事实,CE方法上百亿的参数,BM25相比之下“弱小”很多) | David Rau et al,2022
[异常检测-综述-自监督] | Self-Supervised Anomaly Detection: A Survey and Outlook | 一篇关于异常检测的综述论文,主要是围绕自监督形式的异常检测方法进行介绍,论文中大部分方法的切入视角是图像,搞文本或者多模态的话也可以看看,说不定有所启发。全文主要的内容大体可以分为:(1)对目前自监督形式的异常检测方法和其应用的场景进行介绍和讨论;(2)根据异常检测算法所针对的数据样本的不同,提出对这些算法进行划分,有利于根据不同场景进行算法的选择;(3)最后对未来的发展进行了讨论| Hadi Hojjati et al, 2022
[异常检测-评估] | ADBench: Anomaly Detection Benchmark | 阅读笔记| 一篇很全面的针对Tabular Data的异常检测方法的实验论文,通过设计Benchmark对30种算法(包括许多传统机器学习算法也加入了实验)进行实验分析。其主要贡献就是设计了Benchmark,设计切入的角度分为三个:(1)从完全无监督异常检测到完全监督的异常检测,标签的数量有多重要?(2)对于不同种类的异常,如何分析算法的优劣?(3)对于数据质量中面临的问题,比如噪音、重复、错误等,哪些算法更加鲁棒? | Songqiao Han et al, 2022